hi! thanks for drawing my attention to this problem. I will try to solve it whenever I get some free time to work on pe_to_shellcode again.
- In fact, remapping the PE from raw into virtual format in memory is somewhat redundant - the converter could just do section remapping in such a way that raw format would be the same as virtual. Example:
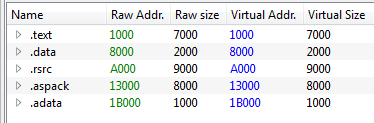
By this way, the original PE could still be run like a normal executable, and yet loading it in memory would not require allocating additional space for remapping. By this change the injecting process will allocate the memory once, implanting there the shellcodified PE, and all what the stub has to do is just applying relocations and filling the imports.
- Yes you are right, although flushing the cache is recommended as a good design, it can as well be avoided.

Thanks for your amazing repo. I'm not an expert, but probably may suggest a little improvements.
You have a call to VirtualAlloc in your shellcode. Since some windows processes have an option "Dynamic code prohibited" (DCP), so you can't do this. Such case may be handled if memory allocation is done by an external process. Thus external process allocate memory for shellcode+image size, then shellcode checks if allocation was unsuccessfull and futher pointing RAX to the end of shellcode, where memory for image is located.
Before calling EP you are flushing instructions. Again you can't do this for the processes with DCP. Probably, you don't need this call, because your newly mapped instructions are never executed before, so they are not in the processor cache, so it is not a "self-modifying" code. Moreover, because this code is for Windows platforms, it is limited to a number of processors. And in most cases (always?) flushing will be done automatically.
With this two things it is possible to run this sc in DCP processes.