Thank you. From the keys you use this should be from Dragalia Lost.
It seems CRI upgraded both ACB and HCA. For ACB they added a mask for byte alignment, which took me some time to figure out. About the HCA file, it looks pretty normal, when comparing header parts one by one. One noticable difference with the files I experimented before is the header size is 397 (0x18d), much larger than old ones, 96 (0x60). Anyway, all the spaces excluding header data and the checksum are filled with 0.
Here is my guess. If HCAs created by older SDKs can be played in the lastest Atom, there are definitely some "signatures" in the file structure itself, not directly recognizable, that the new player understand and so it can decode the HCA in the old way.
Possible changes I can imagine are: 1) changing the decoding process; 2) adding some conditional branches to the existing decoding process; 3) changing value tables; 4) transforming encryption keys (after input, before initializing ciph part). Sure, combinations of these are also possible. Method 1 may bring stronger side effects to CRI's product development so I think it is less likely to happen than the others.
Some explanations to method 2. The main internal parameters of the decoding process are in comp part (i.e. comp1-comp8), whose values' meanings are not easily observable. Maybe, just maybe, the new decoding process used some values or value pairs that never appeared in older decoders, so new value handlers may have been introduced.
Well I think I can still get a latest version of the free version of the SDK but I don't know if it supports decoding encrypted audio. I'll try it later.
By the way I have sent you a friend request on Steam. You can contact me there but I seldom open Steam these days, mostly because I don't have time to play those games. :/

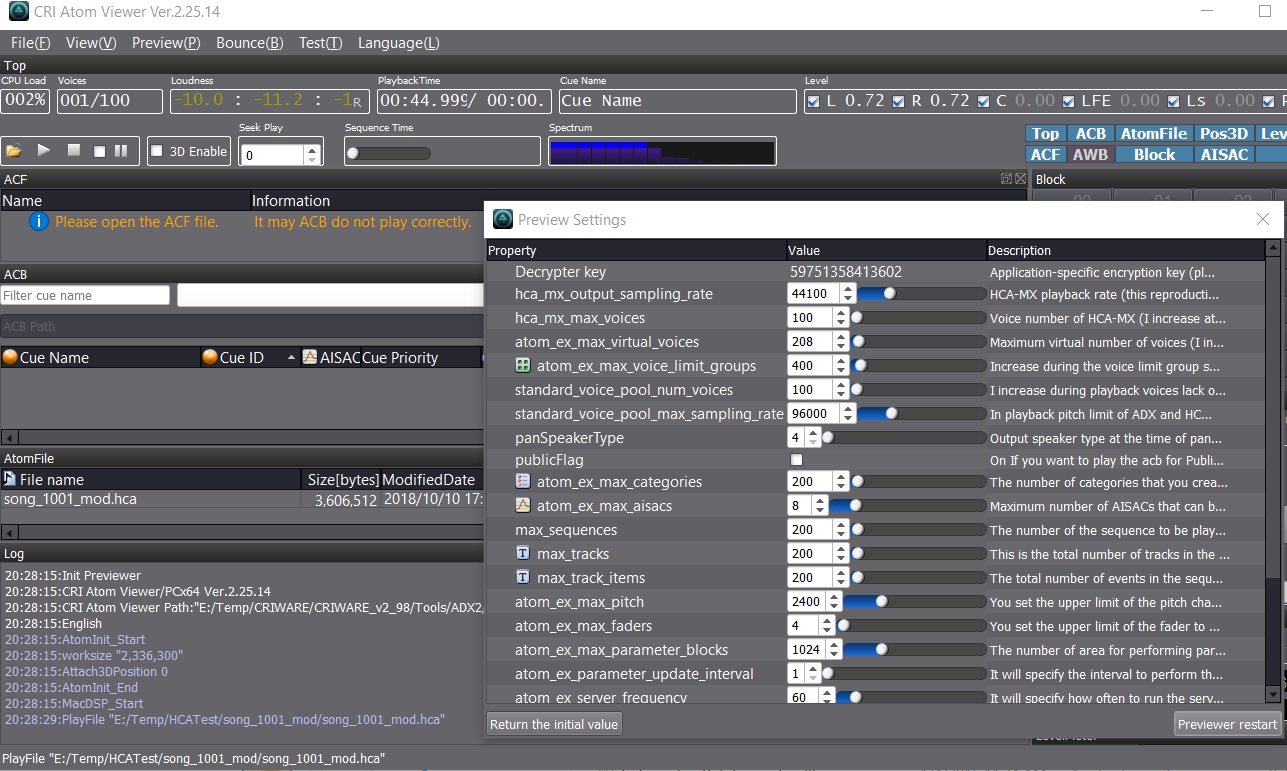


Hello again, I've been trying to use your tool to do extract+decrypt but I am encountering decryption errors. The key is correct because when I loaded the ACB into v2.98 CRIWARE SDK CriAtomViewer it plays fine. I have uploaded a sample AWB+ACB and key inside. Audio format is HCA
If you need a link to the SDK I am contactable via https://steamcommunity.com/id/fzfalzar
-Falz bgm.zip