I could see extending the limitation of the loopback address to also include the private IP ranges. I assume in that case it is extremely unlikely that the server will have an https certificate, so that's another reason to keep the limitation on the private IP ranges rather than allowing arbitrary IP addresses.
One of the benefits of the client ID being a publicly accessible web page is that the authorization server can fetch the application name and icon from that page.
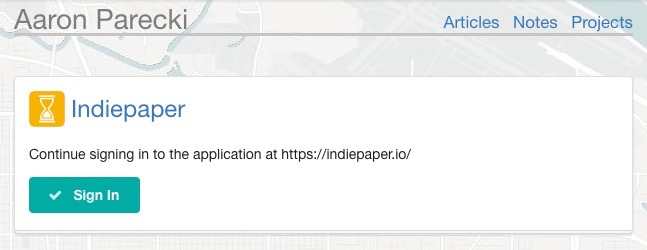
In the case of using a private IP address, the authorization server won't be able to fetch any information about the client, so the prompt will show just the IP.
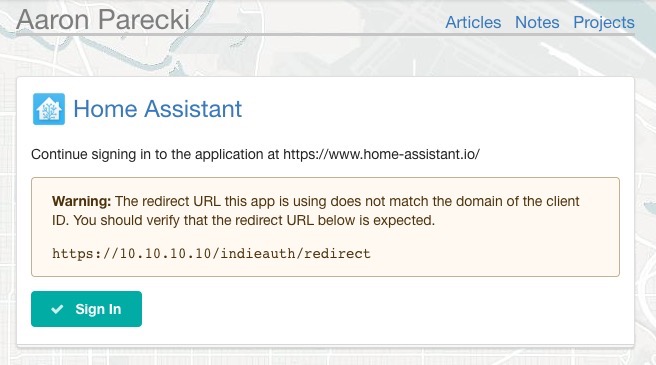
The other option is to use https://www.home-assistant.io/ as the client ID, allowing just the redirect URL to be a private IP. This breaks the rule of the client ID and redirect URL hostnames matching, so servers may show a warning like the below, but at least the application info is visible.
In section 3.2 Client Identifiers, it states the following:
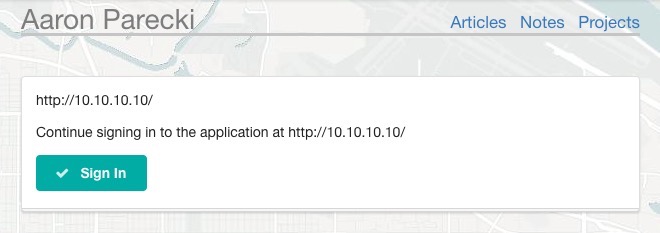
I'm currently implementing the IndieAuth spec for Home Assistant. It's a home automation framework that people run locally at home. Although the computers it runs on usually have hostnames, we don't always know that. This means that users could end up navigating to the Home Assistant interface (a website) using the IP address of the host running Home Assistant. The website is a single page app that will authenticate with the backend using a Client ID following the IndieAuth spec. However, if the website has been requested over IP, both client id and redirect url will be an ip address. This is not allowed according to the spec.
RFC1918 describes Address allocation for Private Internets. Section 3 describes three ranges of IP addresses that indicate a local internet:
I wonder if it could be possible to relax the hostname requirement of client identifiers to include the private internet addresses.