Support for simplified redirect-based protocol handler (simple redirect, no origin support) landed in Firefox 54:
This a a thin UX on top of Navigator.registerProtocolHandler():
-
https://developer.mozilla.org/en-US/docs/Web/API/Navigator/registerProtocolHandler
-
https://blog.mozilla.org/addons/2017/03/13/webextensions-firefox-54/:
The protocol_handler API lets you easily map protocols to actions in your extension. For example: we use irccloud at Mozilla, so we can map ircs:// links to irccloud by adding this into an extension:
"protocol_handlers": [ { "protocol": "ircs", "name": "IRC Mozilla Extension", "uriTemplate": "https://irccloud.mozilla.com/#!/%s" } ]When a user clicks on an IRC link, it shows the application selector with the IRC Mozilla Extension visible:
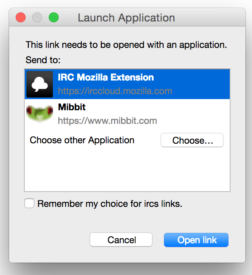
Note that this is just a redirect:
This means the address in location bar changes (Origin barrier is broken) and there are different security context for public and local gateways (different cookies, etc).
And yes, this is Firefox-only.

(living summary: updated @ 2018-09)
This issue tracks browser extension support for various protocol schemes and URIs according to four stages of the upgrade path for path addressing and IPFS Addressing in Web Browsers memo, namely:
URLs:
URI:
This issue also tracks (currently nonexistent) ways to address/workaround how Origin is calculated (Problem #2)
WebExtension APIs
Universal API
No such thing yet (but see WIP work in comments)
Firefox
web+fsprotocol is supported as a redirect: https://github.com/ipfs/ipfs-companion/issues/164#issuecomment-282513891web+prefixipfs://in address bar. It can be found inlibdwebbranch. More info in PR https://github.com/ipfs-shipyard/ipfs-companion/pull/533 and /libdweb/docs/libdweb.mdChrome / Chromium
web+prefix for non-safelisted protocolsweb+prefix (context: https://github.com/arewedistributedyet/arewedistributedyet/issues/23)Brave
Muon-based (deprecated in 2018)
browser.protocol.registerStringProtocolavailable to trusted extensionsChromium-based
Related discussions