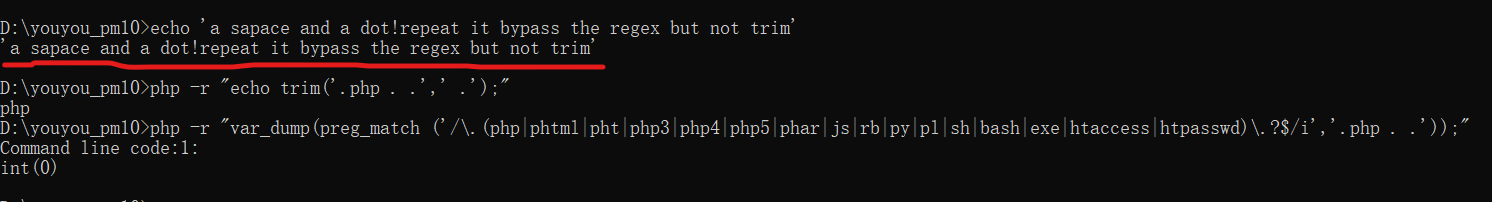
In fact,the windows system will delete all dots after last word.I understand the fixing by regex because of it.But is not a better idea,I can use ".php ."(a space and a dot)
Closed youyou-pm10 closed 1 year ago
In fact,the windows system will delete all dots after last word.I understand the fixing by regex because of it.But is not a better idea,I can use ".php ."(a space and a dot)


That mean the fixing by trim is better,not the fixing by regex.Thanks for your reply.
That mean the fixing by trim is better,not the fixing by regex.Thanks for your reply.
Ah, I see. I just modified it to filter by trimming instead. Let me know if that fixes it for you. Thanks!
In finnal additon,it still has some vulnerabilities in the windows system. (1)Alternate data streams. I can use ext ".php::data" in the windows system. (2)The diffrence of the file system between win and linux. a. The double quotes will be "." file '1"php' is equal to '1.php' b. The angle brackets,“<" and ">"will be "*" and "?". But a file named "1.<<<" just override "1.php" or "1.xxx",it can't create new file.So it is safe if has not php and so on. Follow text is just weak,but is safe at now. Warning: file ”1.php:2.jpg" will create a file "1.php" without its content,but I can do next step by "1.<<<".If has not "<>",it is safe. Notice: the file ".user.ini" with content "auto_prepend_file = anyflie" is equal to "include('anyfile')",but at now is safe because your folder has not php. You can fix it or never put php file in the folder. That' all,I think it's very safe after updating.
I just added a check for invalid characters to prevent the upload. The list includes ?*<>:|\/" although that may not be exhaustive.
Good idea
Thanks again for reporting this!
Vulnerable path /apps/filemanager/handlers/upload/drop.php
Vulnerable Codes
Line 50 of the "drop.php" use a vulnerable black list, ".(php|phtml|pht|php3|php4|php5|phar|js|rb|py|pl|sh|bash|exe|htaccess|htpasswd)$/i", The ext ".php." has Remote Code Execute Vulnerability in the windows system .
Line 61 of the "drop.php" use a vulnerable waf, because server is running under Windows system that does not allow to set the executable flag.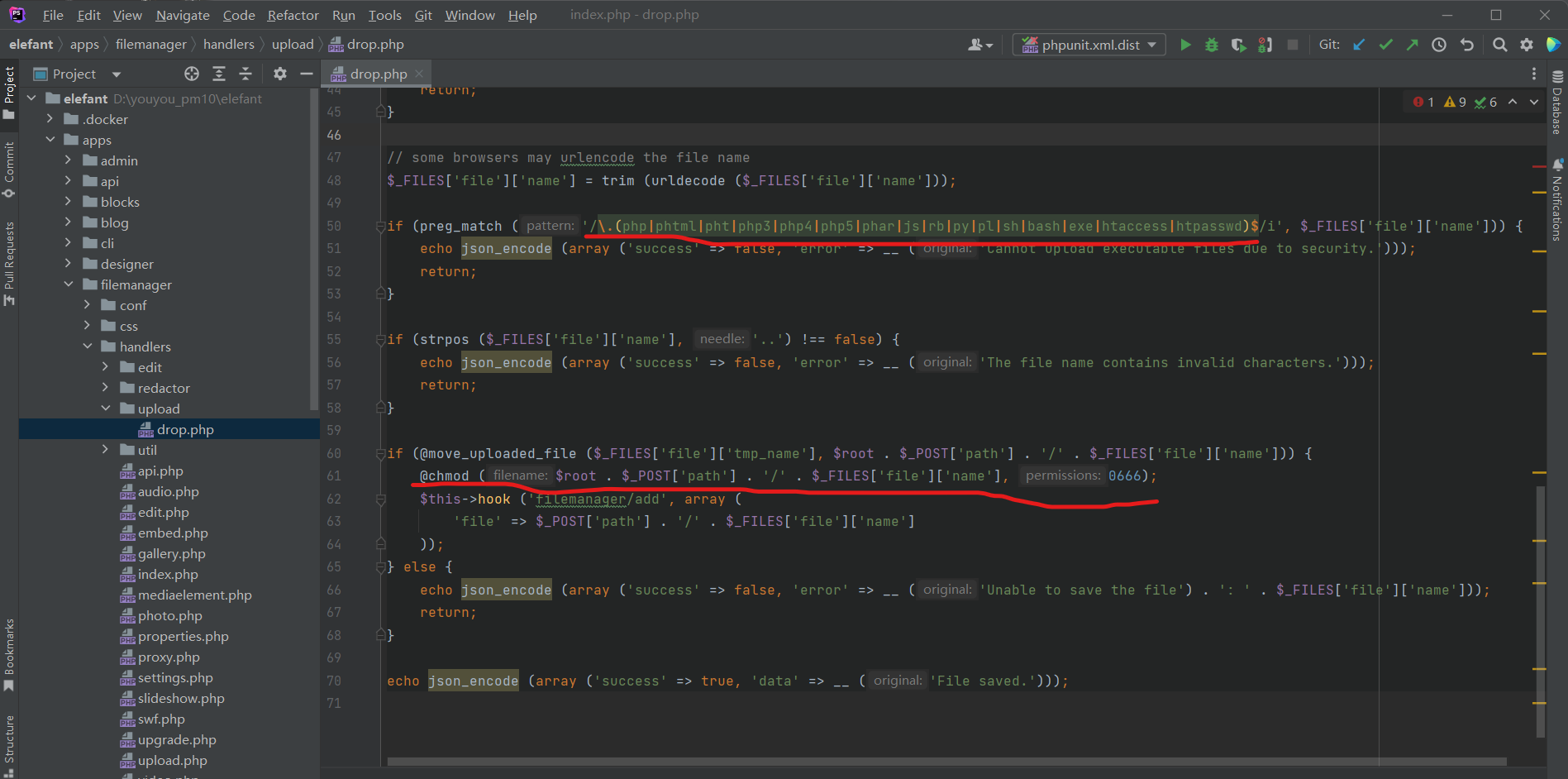
Vulnerability exploitation process:
Log in "/admin",then find a token in the js of "filemanager/util/browser" and request "/filemanager/upload/drop".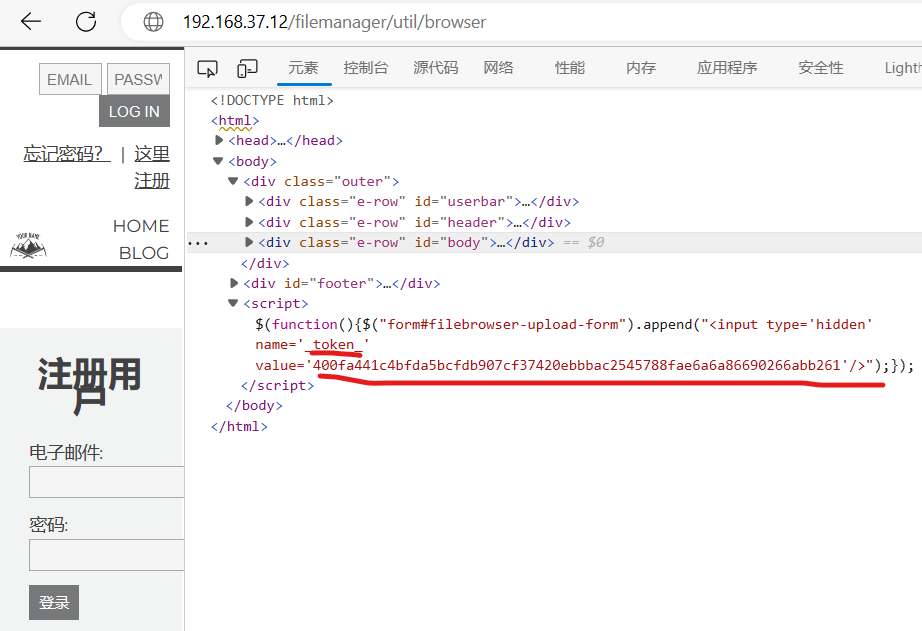 poc:
poc: