That's some weird anti-adblock logic. Fixed.
Closed KonoromiHimaries closed 7 years ago
That's some weird anti-adblock logic. Fixed.
i still have a this

strefadb.pl###videodiv
strefadb.pl###tooltipAnti adblock notice video is put as an overlay.
They're not removing the video but only superimposing anti adblock notice video on the Openload video, so hiding via CSS selectors will also work.
I think the tooltip is unrelated, you can block it with custom filter if you wish.
 The thing on the bottom is blocked, it can take some time for filter list to sync.
The thing on the bottom is blocked, it can take some time for filter list to sync.
@uBlock-user Yea, but it won't dispose the player in that case.
You mean via picker ? Zapper doesn't block elements, it only removes them until a page refresh.
Still tooltip is an annoyance, should be removed.
@uBlock-user i still have

True, I thought it's permanent... I wouldn't say it's purely annoyance, as it could be helpful in some cases. I won't add it to List.
I don't speak polish, you will have to describe it.
By annoyance, I meant its position. They should have placed it somewhere else and not in the centre of the video player, that makes it an annoyance as it always appears.
Missed ads goes to EasyList. Or right click -> block element.
Still, I won't add it to List, just in case someone needs it. You can block it with with your custom filter if you don't like it.
@jspenguin2017 i know, thx. for your help : ) i manualy blocked this unwanted elements
Another thing, sometimes openload loads videos via oload.info which is its clone site and popups appear via about:blank
https://oload.info/embed/MDWXdU0koJ0/DBZ_TV_Special_01_-_Bardock_Ojciec_Goku_1990_NapisyPL.mp4
oload.*/*license
oload.*/*scriptEhm, they have a crypto miner as well... Seems to be throttled to 50% of 1 CPU core.

@okiehsch of uAssets @keraf of NoCoin
CoinHive is registering new domains.
One Linode hypervisor is experiencing hardware issues. The popup fix will have to wait.

Hm, they are using random domains.
So blocking by domain seems pointless.
Blocking the WebAssembly file only fix half the problem, the bootstraper will try to start 3 times per second. I have put /cryptonight.wasm in List until we can figure something out. Probably should fingerprint and block the wasm file by patching WebAssembly property.
Can we write a bot and list all their domains? It costs money to register domain, let's see how much funding they got.
I knew CoinHive is going to be a hard and long battle...
I know we can just $third-party all OpenLoad's connections, but that's one domain, it'll be a pain to police the entire Internet.
Well, I can see two solutions for uBO:
oload.info##script:inject(abort-on-property-read.js, WebAssembly) or
oload.info##script:inject(abort-current-inline-script.js, document.createElement, (/[A-Z0-9]{8}-[A-Z0-9]{4}-[A-Z0-9]{4}/.test(key)the second one seems preferable.
So basically we'll be chasing behind them and patch on a per domain basis? It's kind of hard tell since it throttles itself pretty hard (to 13% of CPU on my PC), they can stay under the radar for a while. The new and promising WebAssembly is getting abused right away, kind of sad that people find ways to exploit everything they find.
I don't see a better solution right now.
@uBlock-user regarding the popups, I added oload.info to uBO-filters
So basically we'll be chasing behind them and patch on a per domain basis?
That's how it has been always working with ads and trackers, there is no magic bullet.
In https://github.com/uBlockOrigin/uAssets/issues/690#issuecomment-330401913, I entertain the idea of informing users about the use of webworkers, and ability to block them (like the no-popup-switch). One problem is Firefox is not CSP3 yet, it does not know about worker-src. At least this would give users some control without having to completely wait for filter list maintainers to provide filters.
.info^$script,third-party,domain=oload.info will also work and could be added to NoCoin
@okiehsch Yes, that seems to be the safest solution for now. Though why not:
||info^$script,third-party,domain=oload.infoOK, I will add it to uBlock Origin -- Resource-abuse
Alright, my server is up, build is published. It's gone far enough off topic, so I'll lock the thread. Open a new issue for further problems.
Update: Actually, I'll leave the thread unlocked in case someone has a quick comment, but report other domains that uses CoinHive to a new issue.
Why not CSP the entire domain ? Let them run as many random domains as they want.
||oload.info^$csp=script-src 'self' 'unsafe-inline' 'unsafe-eval'
@okiehsch I already have that filter in my personal list, that doesn't stop the popups on my end. They only stop after I block license and script jses mentioned in https://github.com/jspenguin2017/uBlockProtector/issues/636#issuecomment-334316392
site https://strefadb.pl/filmy-kinowe/dragon-ball-z-tv-special_01_bardock---ojciec-goku.html
ubpe & ub ( on - not work )
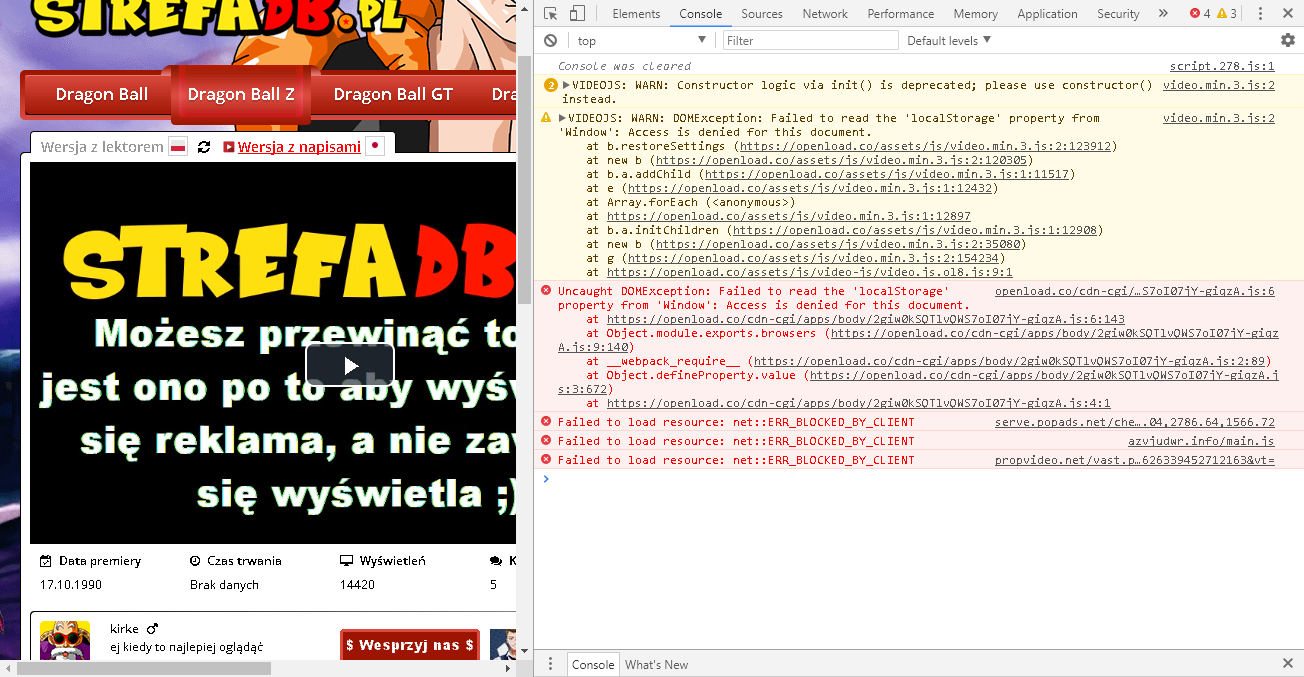
ubpe & up ( off - normaly work )

ub 1.14.8 ubpe 11.352 chrome 61.0.3163.100 x64