I still think this is an antipattern fad that is going to go away. Cool dialog though
Closed marekjedrzejewski closed 3 years ago
I still think this is an antipattern fad that is going to go away. Cool dialog though
Antipattern or not - it is still a valuable feature for logins in various locations that still require selective character input. For me it's the only thing that forces me to use a regular KeePass from time to time. It would be great if I could use KeePassXC for every use case I have.
👍 to that.
To be honest, I didn't even know this broken authentication scheme was even a thing until people started bringing it up.
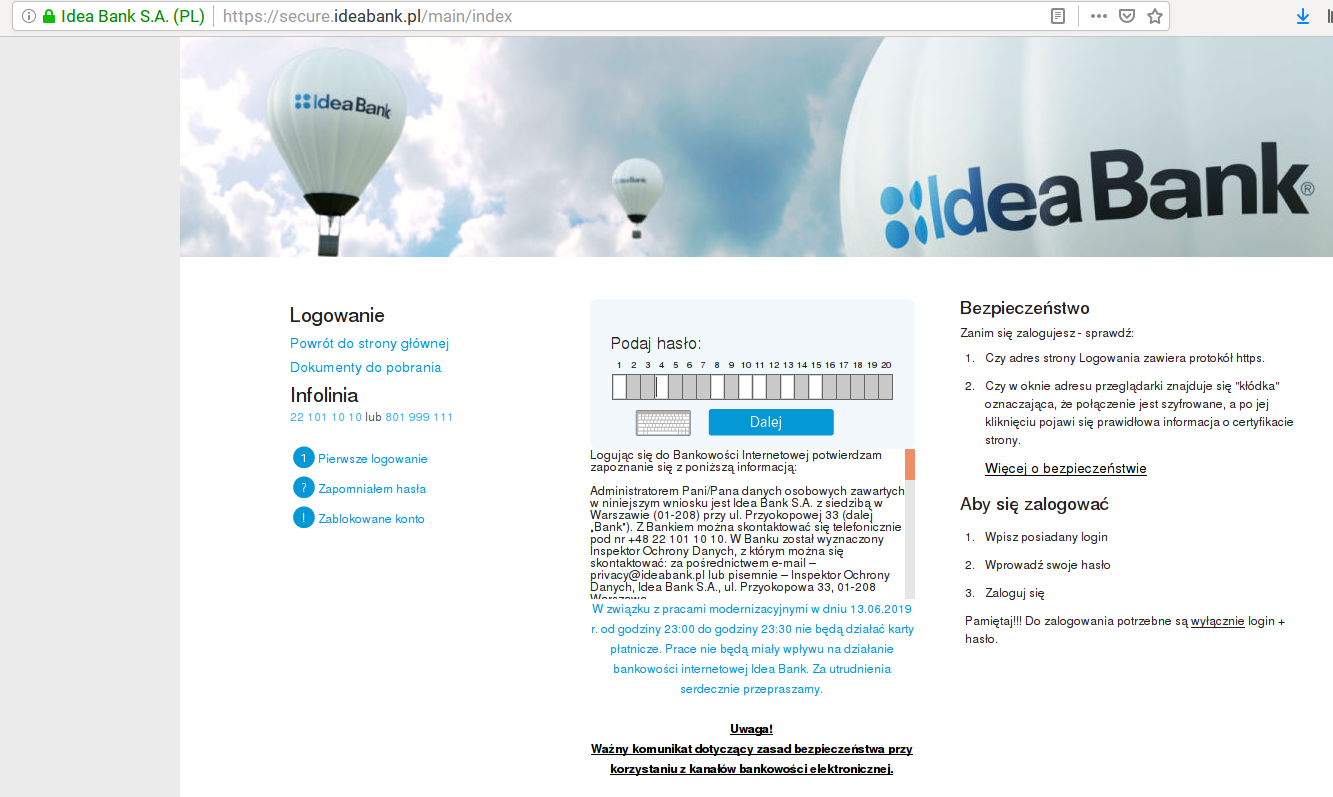
Santander, one of the world's largest banks, use this authentication scheme.

Having {PICKCHARS} is a life saver, especially when you've got a long randomly-generated string as a password :)
I think this will remain in wishlist for a long time
https://github.com/keepassxreboot/keepassxc/issues/820#issuecomment-328500837
I think #820 has been referenced in error, these are two distinct suggestions/features.
It was a specific comment that I was referencing.
Here Santander is using a bad practice authentication. The password stored in Santander database are plaintext otherwise they won't be able to know which character is in which position. Storing passwords in plaintext is a VERY BAD idea.
I'm really not interested in developing a tool that will increase the adoption of such a system.
Again, denying this option to KPXC users will NOT make Santander (or any other banking system - seems that only those use it) forfeit this login method.
Some people are stuck with certain banking solution and as long they have no other option, KPXC is useless. Imagine using a business account, where you have no saying in which bank is contracted. What would you rather see? A user not relying on kdbx and using memorized/written down, fairly simple password or a user that is doing everything he can in order to make everything as secure as possible on his side?
Do what ever you think is right, but from my point of view you're declining the feature while blaming the wrong side.
And no, those passwords are not stored as plain text. I encourage you to do some research before making any assumptions.
I've not said that we won't implement this. If we receive a PR we can even accept it.
But personally I will not waste time on this since only few website are using this scheme and there are core feature that need much work instead.
this will NOT make Santander (or any other banking system - seems that only those use it) forfeit this login method.
Never heard of strike/protest? If users don't have a way to login they should blame Santander for using that login method.
And no, those passwords are not stored as plain text. I encourage you to do some research before making any assumptions.
Then tell me how they are stored. Encrypted? Then the server has the key to decrypt them and see them in plaintext. Homomorphic encryption? To date there are no reliable homomorphic encryption scheme that are safe and reliable at the same time
The only viable option is using 2 password, one stored as hash and one stored plaintext, asking the full one and only part of the second one, but from the screenshot (and from what I read online about Santander) this is not the case
I would love reading some papers/documentations on that (but sadly all banking system are closed source proprietary software)
I was recently confronted with this weird confounding authentication scheme on a UEFI console when I tried to change secure boot settings. That was the one and only time I've ever had that. Never before, never since and I'm still puzzled by it. It is so astoundingly counter-intuitive that I almost forgot what password I chose when it asked me for the 3rd and 5th character of my temporary 7 character bullshit password.
BTW I agree with @TheZ3ro that this is very low priority. If somebody wants to implement it, fine by me. But for us it's no priority. I consider this authentication scheme very bad practice for obvious reasons. The most obvious is its terrible usability which I described above, the other is its security.
As for how banks implement this scheme, we have no idea what methods they use, because, as said before, they are all closed-source. The three supposedly most viable options would be symmetric encryption (hopefully with some sort of HSM or at least TPM), hashes of all possible combinations of letters or secret sharing where you use your partial passwords to encrypt a stored hash value which you can later compare.
None of these are industry standard best practices for storing passwords. Symmetric encryption may compromise passwords if the keys are leaked. There is expensive security hardware which is designed to prevent that, but why not simply hash the passwords for free? Hashing of partial passwords is very inflexible, costs a quadratic amount of space and when you have to hash so many passwords, you are more likely to use fast hashing algorithms which overall lowers the security considerably. Secret sharing is perhaps the best way, but I don't like it either. There has been quite some research in the field (Google Scholar lists about 1.3 million papers), but except for two recent ISO publications I can't really find any applicable industry standards. Password hashing has received a lot more attention and is considered the industry standard best practice for good reason. There are also hardly any notable libraries out there that provide a secure and proven secret sharing implementation except for various textbook Shamir-SS finger exercises. I wouldn't entrust my passwords with any of those implementations.
Is this feature still going to be implemented (if not eventually)? for me its one of the biggest headaches re keepassXC.
There was progress made in issue #1245 but that got closed.
My opinion this feature should never be implemented, it is bad in all cases, just change the bank to another with proper security practices.
please expand on "bad in all cases"; Is it a high priority feature? well no probably not. but it is important enough for Keepass to implement and would provide a benefit to a number of people.
yes the banking security is potentially a little less, but i'm not moving my bank because it's hard to type in my password / the bank does not have the best practices.
what harm, apart from needing a bit of coding time, does it cause to add it in?
please expand on "bad in all cases";
Usability/security.
Is it a high priority feature?
it should not be a feature at all, as it is a bad security practice. Check BarclayCard, they are authentication a user by 6 digit pin and 2 letters from memorable information, instead of implementing 2FA as they should.
would provide a benefit to a number of people.
benefit of usability may be, questionable, but it will be a huge step back in security, people should stop using these banks and not move bad practices into password managers.
i'm not moving my bank because it's hard to type in my password
you should move your bank because they are incompetent.
what harm, apart from needing a bit of coding time, does it cause to add it in?
more code => more complexity => more issues
Example is 2FA software token functionality should not be implemented in password managers because it kills the idea of "the second factor", but with your logic it should be added as it "would provide a benefit to a number of people".
We have already added 2FA TOTP in KeePassXC and it does not kill the idea of a second factor. You can create multiple databases and simply store your TOTP token separately from your main password database. Use a different master key and there is your second factor. In fact, I would argue this is much more secure than storing that information on a phone that only gets security updates semi-annually.
As for this "feature" I do intend to implement it based on the original PR that was submitted, but not until 2.5.0.
We have already added 2FA TOTP in KeePassXC Missed that, thats a shame it does not kill the idea of a second factor. You can create multiple databases and simply store your TOTP token separately from your main password database.
this is exactly the wrong 2FA usage, the attacker needs to get access only to one device to perform the attack now. there is no physical separation of factors anymore in your case.
I would argue this is much more secure than storing that information on a phone that only gets security updates semi-annually.
this is why phone is just an additional factor in authentication, hacking the phone or getting access to a hardware generator is not enough to log in to a system with 2FA.
As for this "feature" I do intend to implement it based on the original PR that was submitted
okey then, may be 'reboot' went to much into 'reboot'.
My opinion this feature should never be implemented, it is bad in all cases, just change the bank to another with proper security practices.
And that's exactly why YOU lose potential users, Mr. Know-it-all.
@OskarW85 that quote is not from a member of the KeePassXC team...
@OskarW85 the first: these banks should loose clients, And yes, keepassxc lost me as a client, trivial bugs are not fixed, but bad secure practices are introduced in priority.
I don't know what trivial bugs you are talking about, but I object to the statement that we implement bad security practices. I am inclined to lock this issue. The discussion has derailed and is leading nowhere.
Fully agree, sorry, I am stopping posting.
I'm also keen to see this implemented. It's the main feature missing from KeePassXC which would allow me to completely retire KeePass.
Two UK banks I'm aware of require selective character input from a password to login to their online banking: Nationwide Building Society with £232 billion group assets and Metro Bank.
Some have suggested switching banks, however there are many criteria which people use to choose a bank, and different people will assign different priorities to the various criteria. Additionally, some people have few options which satisfy their must-have criteria and changing banks is not a trivial process for many. For myself ruling out a bank just because of selective character passwords in their online banking is excessive. That said given two otherwise equally good banks I'd definitely pick the bank without selective character password input on their online banking login of course!
Here is a screenshot from Nationwide's online banking login page (note that they do have an option to login using a card reader but this requires access to a card reader as well as a debit card which is not particularly convenient):

LOL, "I've forgotten my memorable data". That login prompt is such a joke (no offense to you, thank you for the report details). A 6 digit number reduced to three digits from pickchars and "personal data". Dear God.
Lack of this tiny feature stops me from moving from original KeePass but in Poland password manager without this feature is useless for online banking. To be clear — I hate this login scheme and I think most users use short, simple passwords or write them on paper just because of this login scheme. On the other hand, I don't think that users can do anything about it because here in Poland almost every bank uses this. I read somewhere that passwords are kept encrypted in some piece of dedicated hardware and never leave it in clear text — system feeds it with user-entered characters and this magic box checks if they are correct.
Here is the biggest Polish bank for private users
 and for enterprises
and for enterprises
 this one use it only for PESEL (personal number)
this one use it only for PESEL (personal number)
 and the rest
and the rest



 and for these it is possible to turn this off (but default is on)
and for these it is possible to turn this off (but default is on)


 Those are not all banks in Poland but now you have some view.
Those are not all banks in Poland but now you have some view.
To be fair, some of the banks on the list that I have access to (i.e. Alior Bank , IdeaBank) lets you use the masking of choice and I can easily use them with full normal password inputs.
To be fair
Yes, to be fair I edited my previous post — IDEA indeed allows users to turn off masking. In the case of ALIOR, this is no longer possible since their last update in May (at least in regular / private version I have access to — perhaps it is possible in BusinessPro). I even had to introduce {DELAY=500}, because their script to move the cursor to the next filed is too slow for Auto-Type. So yes, some banks allow users to disable masking, but I bet that most users don't know about this possibility and log in default mode with masking.
Since we got a bit off the topic I will just clarify one thing.
In the case of ALIOR, this is no longer possible since their last update in May (at least in regular / private version I have access to — perhaps it is possible in BusinessPro).
This isn't true (it's not the BusinessPro):

Nevertheless, the feature would be nice to have.
For what its worth, in Europe, banks like Nationwide (which I use), will be removing memorable information logins and replacing them with Strong Customer Authentication:
Being a customer of some of these banks (where masking isn't optional and allowed to be turned off) I've produced a little workaround that can be used with KeepassXC. It's much easier and faster for me using it to authorize in banks. Maybe somebody would find it useful.
Hello Guys,
First of all thank you for KeePassXC. I discovered it few weeks ago and now cannot imagine my daily work without it. Just raising both hands to vote for it to make it possible in KeePassXC. Repeating after previous comments. Lots of main banks in Poland is using this method and by enabling this feature in KeePassXC you are giving opportunity for huge group of users to have strong password for their bank account. As per above @droidmonkey modification for milestone, I'm living with hope to see it in version 2.6.0 please :)
Im just hoping we delay long enough to let this ridiculous behavior by banks run its course. :stuck_out_tongue_closed_eyes:
Yes, delay it and people will delay using keepassxc.
@droidmonkey - banks do not care, people do. Believe me, by adding this feature you will help tons of people in Poland and also encourage many others to just use KeePassXC instead of KeePass2 which have this option. Personally I do not like this one and will not use it for many reasons but this is not the topic of this discussion. Why you are defending so hard to enable this feature? Those who do not want's it will just not use it, that is why we are calling it "option". No pressure to use it. Let the people have the choice, mate :)
I thought my tongue out smiley emoji was enough to indicate I was being sarcastic because we have kicked this one down the road quite a bit....
Either way, this is a lot of work (relatively speaking) for such a specific feature to appease an anti-feature on very select services. This all comes down to priority and time. If you want to see this sooner then I recommend making a sizeable bounty on Bountysource.
I just tried to give you straight clear picture about situation with this feature about which I'm speaking with my fiends quite a lot. It was not my intention to rushing you at all. I'm patient and even small light at the end of tunnel bring hope we will see it. (2.6, 2.7 etc) I just believe there are many other eyes watching this topic daily but bit shy to sign in there just to leave their voice in this matter or thinking "ah they do not have it so we need to use other software" We have more than 37 Million people in Poland so I assume there are hundred of thousands which you can make life easier if you just care about it. So one more time just kindly asking and voting to do not abandon this idea and implement it "somewhere in time" (repeating after Iron Maiden) ;)
@droidmonkey Assuming I understand correctly, notes and other data are fully encrypted as per the stored passwords? Given that, and your latest improvement to the notes (monospace fonts) wouldn't a suitable workaround be simply to put the password, along with an index into the notes field? i.e.
p a s s w o r d
1 2 3 4 5 6 7 8While the security of banks and other institutions doing this is debatable if such a workaround is still secure wouldn't this mean such a feature is less viable?
Yes anyone can do that workaround right now
droidmonkey changed the title Make {PICKCHARS} possible Make {PICKCHARS} possible [$5]
Oh I see, "Bussinessman mode {ON}" 😄 But why not.... I like to support great ideas. So for good start you have my 5$ and whish all the best for all of you guys from KeePassXC team.
Umm. OK. I forwarded it to Bounty Source.
@phoerious - was it something wrong from my side I pasted confirmation of my donation which you deleted, please? Just asking to know cause I'm fresh here and do not want to behave not right.
Bounties should go directly to Bounty Source. I deleted your PayPal receipt to protect you from doxing yourself. 😉
Not sure if I know what you are about (bountysource stuff) but for sure I know what project I donated as I found it very usefull and valuable. One more time whish you KeePassXC team all the best. Will not bother you more by my presence. Signed-up here only to try kindly bring your attention on this subject which affects many persons which maybe would like to use application functionality in full spectrum. Best Regards (PS: Regarding doxing, I'm not the one who changing post subject instantly ;))
The post subject is changed automatically. Anyway, thank you for your contribution.
For those using bash I made a tiny script to print selected password chars from an entered password: ppc (github.com)
You can call the script with the indexes of the chars you need then trigger auto-type to enter the password into your terminal. For example to get 1st, 3rd and 5th chars from password 'abcde':
> ppc 1 3 5
Password: <trigger auto-type>
a c eMaybe it is worth implementing it in KeepassXC-Browser?
The Polish Santander bank segregates each field of the "masked" password by giving them identifiers:
<input id="pass1" /> <input id="pass2" /> <input id="pass3" />
Another popular bank in Poland - ING, does the same:
<input id="mask-1" /> <input id="mask-2" /> <input id="mask-3" />
It would be enough to make an array from password, and in javascript run foreach for each input.
And then:
if(!element[i].disabled){element[i].value = password[i];}
This is not a perfect solution - but it can work
@TheZ3ro @phoerious
Hi, this feature is implemented using HSM (https://en.wikipedia.org/wiki/Hardware_security_module) and it is pretty secure. It is not important how passwords are stored inside HSM because extracting it from there is or at least should be extremely difficult and those kinds of machines are frequently audited and certified. So we can not simply accuse banks of storing passwords as plain text. Client e.g. bank website is contacting HSM via API. Simple HSM API may look like this:
Please don't get me wrong I still think that hashing is safer and better. One of the reasons why is: https://randomoracle.wordpress.com/2015/08/13/safenet-hsm-key-extraction-vulnerability-part-i/ But this method is a reasonable compromise between security and usability and it adds some level of protection against key loggers etc. Handling this kind of logins sites is not very bad idea. I am using keepassxc and lack of this feature is extremely irritating for me. Please take that into consideration.
@DawidKukla Are there HSM's that can store so much data that it's feasible to store the passwords for all users inside them? (even if you split them among a few). Or are the HSM's just storing an encryption key and the user passwords are encrypted on a database?
Anyway, this scheme doesn't really protect from keyloggers, it just delays them until you log in a few times (I doubt that you'll detect and get rid of keylogger in your system in time). 2FA is the real solution against keyloggers. I don't see how this scheme is a compromise between security and usability, it significantly hurts usability for a questionable defense against keyloggers, while enforcing shorter/simpler passwords.
I wonder why did this discussion trail of to whether or not masked passwords are secure.
The truth is that some websites use it, in some of them it's not optional and currently KeepassXC isn't very helpful when logging in to them.
I think that when forced to use a website that uses a masked password (like my bank does), it'd be more safe if my password manager helped me pick characters from arbitrary positions of my super-strong password, than for me to set up a super-easy password that will not make me pull my hair out when trying to type it in a masked input.
Original KeePass has {PICKCHARS} placeholders for entering partial password, would be nice if it was implemented.
Expected Behavior
When entry has {PICKCHARS} placeholder, window is opened that lets user choose which characters of the password should be entered. It looks like this in KeePass: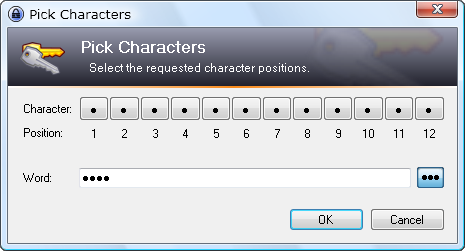
I'd gladly try to implement it myself if someone points me in the right direction :)