Hi, Actually, since there is no auth in the GraphQL spec, I haven't thought about a Siler provided solution for that, but we can came up with a solution! :)
On my APIs a use JWT then I add an User or a GuestUser to the GraphQL context then on each resolver I see in if there is a User the Context and if the User has proper roles.
Hello,
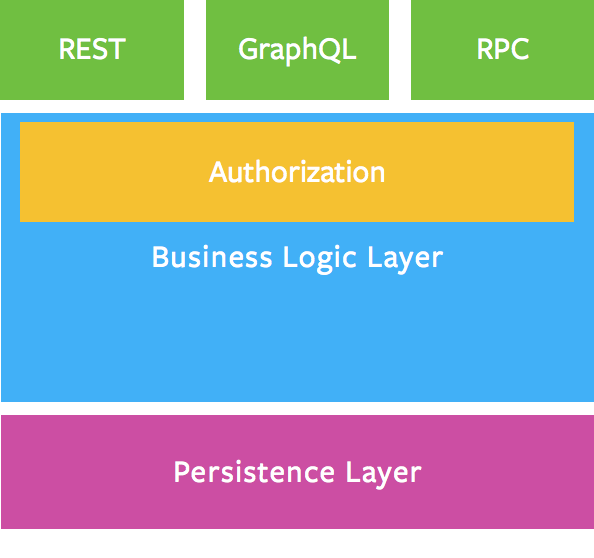
What is recommended way to add authorization logic to Siler\GraphQL module? I'm aware of that authentication could be successfully done via route middleware, but the same cannot be done with authorization (or shouldn't... to achieve it anyway, you would have to parse request once more and fetch operation type, operation name and arguments recursively...).
For instance, package
thecodingmachine/graphqliteoffers@Securityannotations that are handled by authentication and authorization services that you set in schema factory.Are there any plans to implement similar feature to Siler\GraphQL? Or maybe solution already exists and I didn't manage to find it in documentation and source code? Maybe with dispatcher...?
I created actually a temporary workaround for this in Query class, but I wouldn't recommend it to anyone...