docker run \ --volume=/var/lib/sss/pipes/:/var/lib/sss/pipes/:rw \ --volume=/etc/sssd/:/etc/sssd/:ro \ --volume=/etc/krb5.conf:/etc/krb5.conf:ro \ --volume=/etc/ipa/ca.crt:/etc/ipa/ca.crt:ro \ --volume=/etc/nsswitch.conf:/etc/nsswitch.conf:ro \ --volume=/etc/pam.d/:/etc/pam.d/:ro \ -h myubuntuhost.my.ad.domain ... etc, etc.
OMG! I think it works! The mapping of the volumes made a difference to me. Before that I couldn't do this:
CREATE LOGIN [DOMAIN\user] FROM WINDOWS;It would tell me...
Windows NT user or group "DOMAIN\user" not found. Check the name againBut now, it works. Hmmm.
@lubo i think it need to be joined to the domain in order to create the service principles with setspn and ktpass and so on.

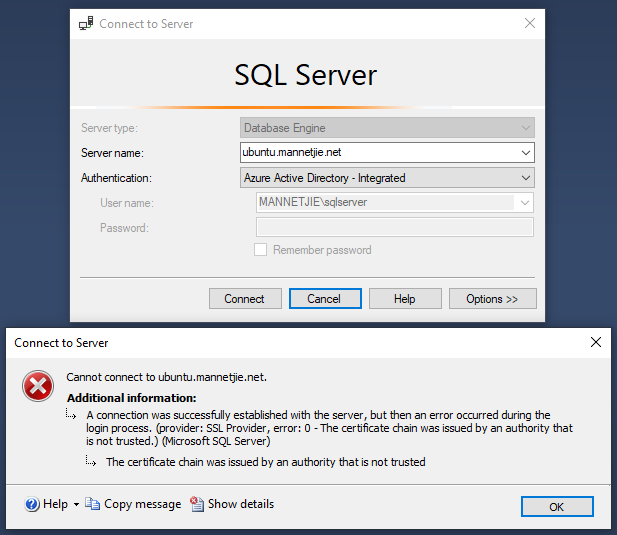

How to use windows authentication? Will assigning linux host to windows domain be enough for container to work with domain user authentication ? What can i do to achieve this ? I have windows server 2012 as active directory domain controller and debian 9 for docker.