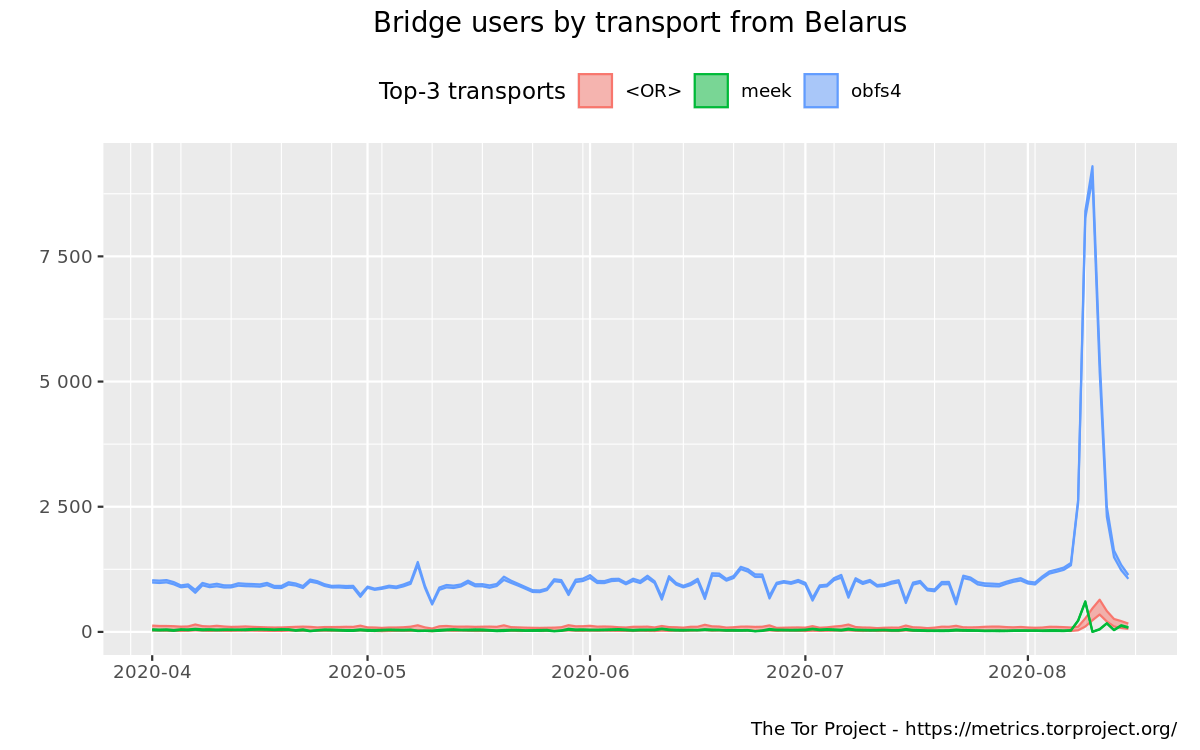
There was a decrease in Tor relay users and an increase in Tor bridge users, mainly obfs4.
https://metrics.torproject.org/userstats-relay-country.html?start=2020-04-01&end=2020-08-15&country=by
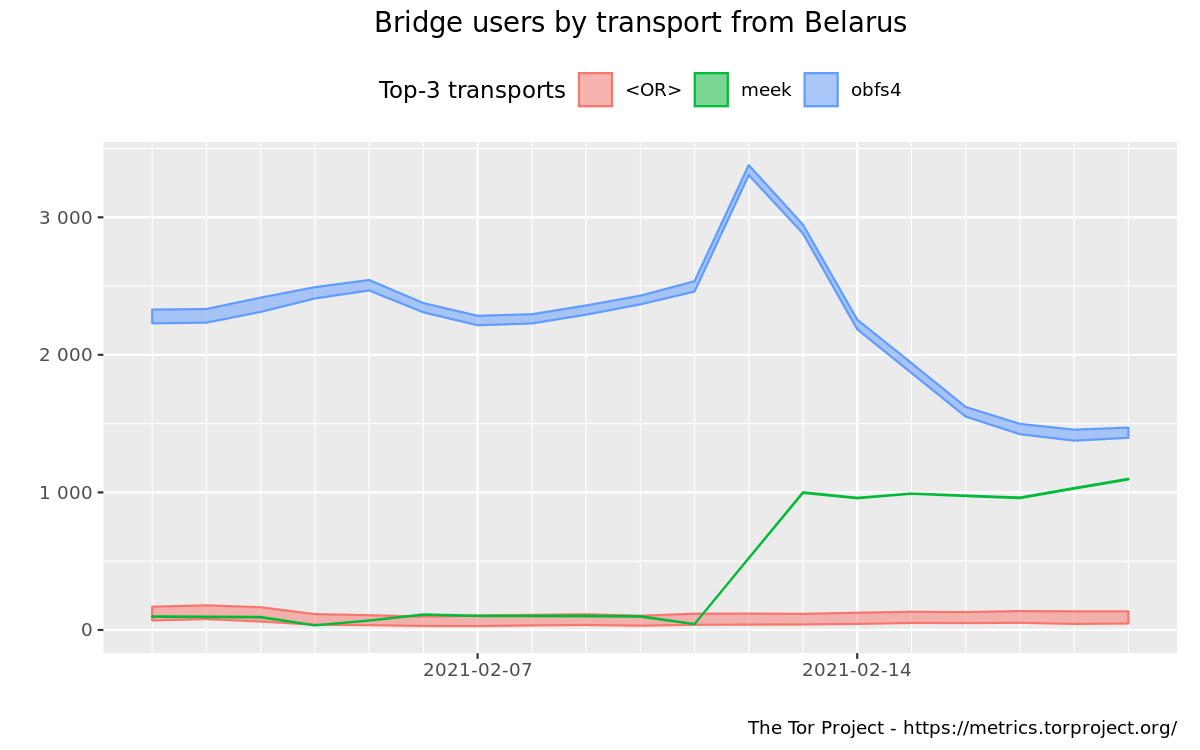
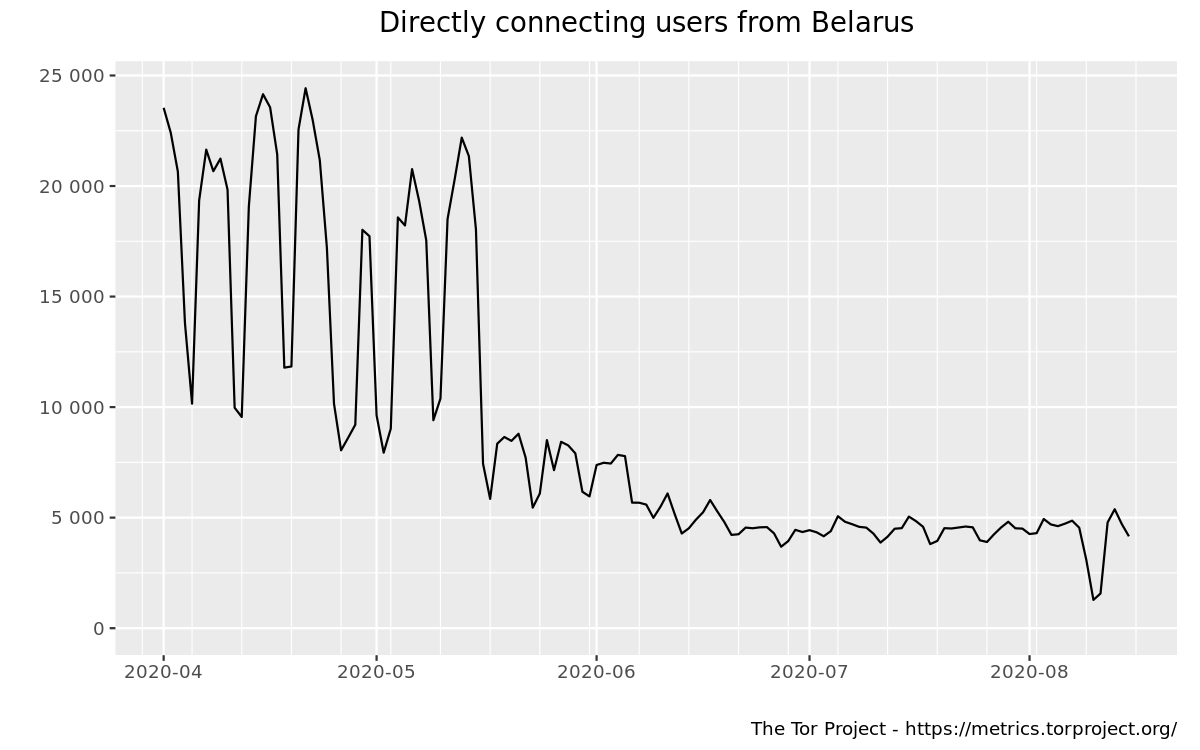 https://metrics.torproject.org/userstats-bridge-combined.html?start=2020-04-01&end=2020-08-15&country=by
https://metrics.torproject.org/userstats-bridge-combined.html?start=2020-04-01&end=2020-08-15&country=by
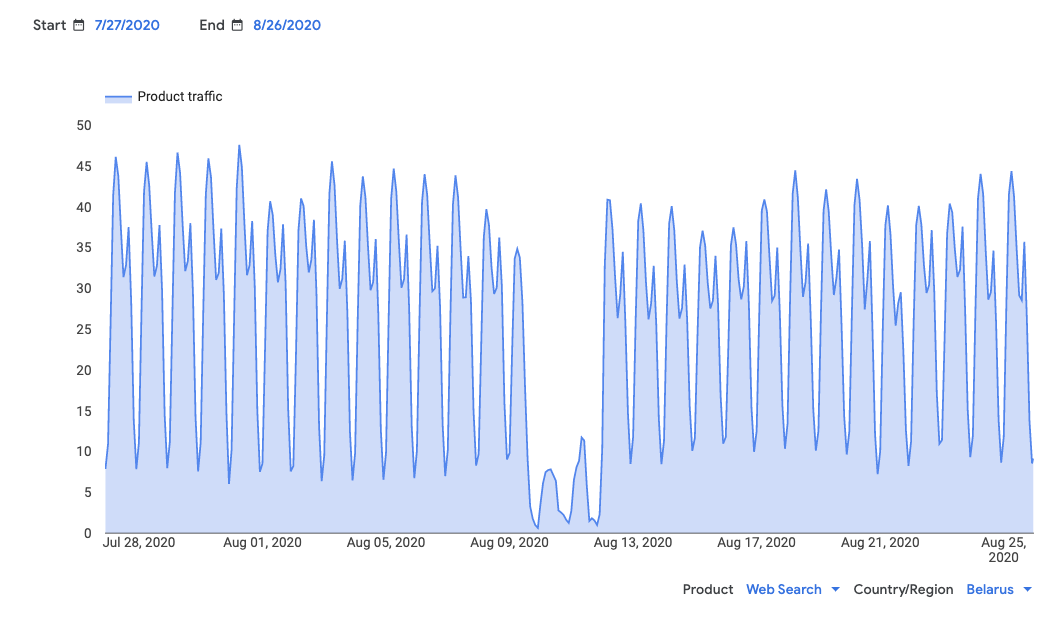
Psiphon shows an increase in daily connections from Belarus, from near zero on August 7 to over 15 million on August 11.
https://psix.ca/d/nyi8gE6Zk/regional-overview?orgId=2&var-region=BY (archive)

OONI has a decrease in "available" measurements and an increase in "blocked" measurements.
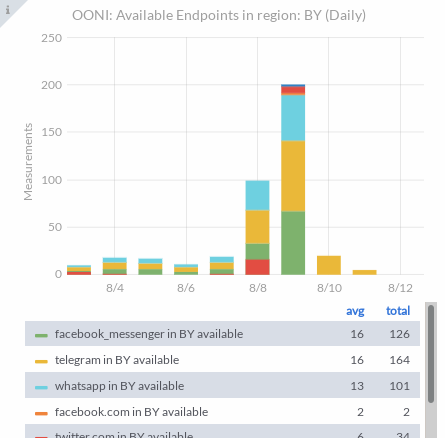





A long thread at NTC (in Russian) where @ValdikSS has prepared a server container and client VM to maintain access in Belarus. If you make an account at NTC and log in, there is an 🌐 automatic translation button beneath each post.
IODA dashboard for Belarus in the past 6 days. For help using the IODA dashboard, see the IMV talk by Ramakrishna Padmanabhan or the screencast by Philipp Winter.