Uploaded a copy of the certificate files here: https://archive.org/details/qazca-ca-certificate
Open wkrp opened 5 years ago
Uploaded a copy of the certificate files here: https://archive.org/details/qazca-ca-certificate
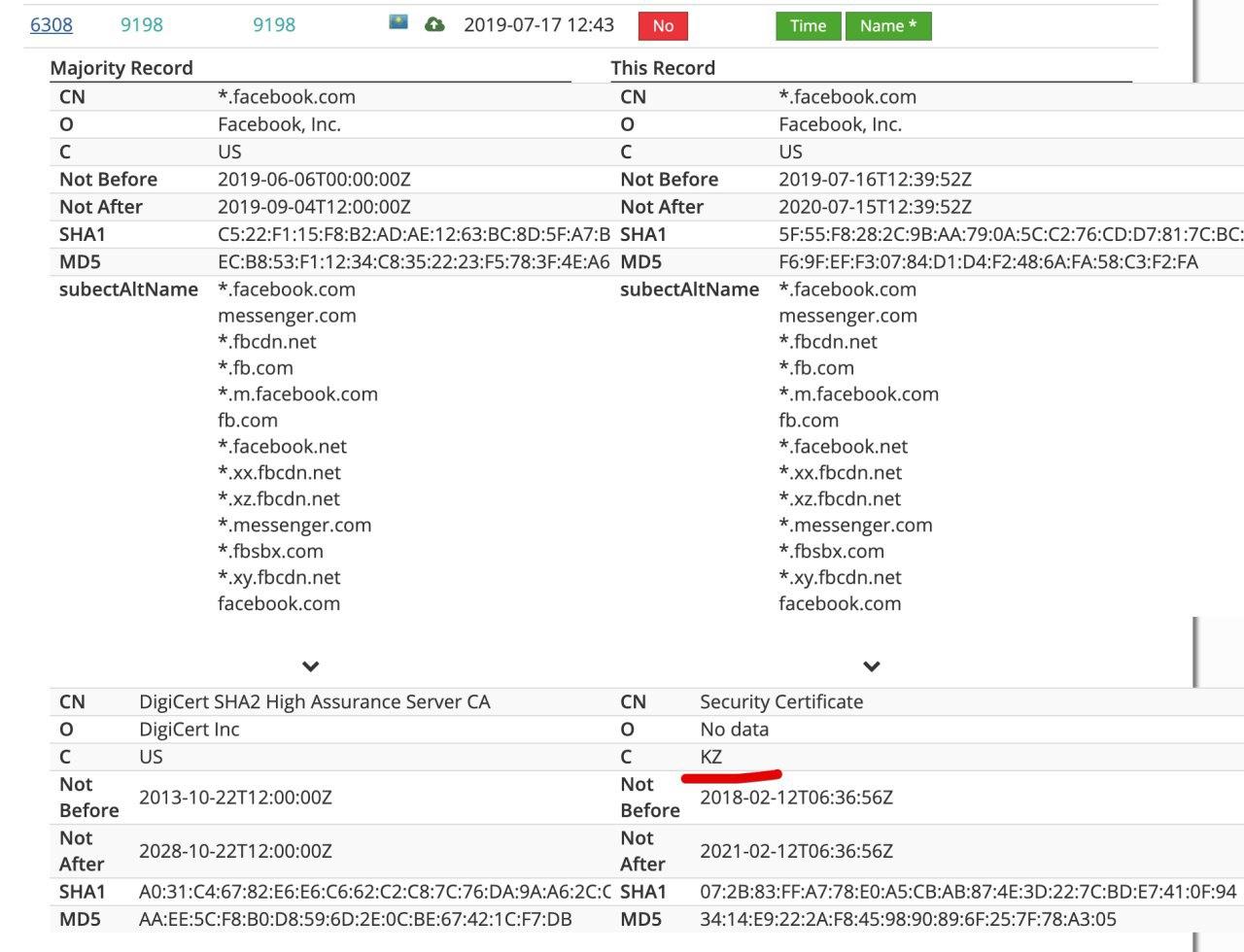
I consider it quite ironic that public key for CN=*.facebook.com signed by CN=Security Certificate is RSA 1024. One can got those certificates right from the RIPE Atlas measurement.
Censored Planet published a report on 2019-07-23. The most interesting observation, to me, is that the MITM is bidirectional: you can send an affected SNI from outside Kazakhstan to a TLS server inside, and still get a phony certificate. Here is an easy sample command line to test it:
$ curl --verbose --resolve www.facebook.com:443:95.59.142.120 https://www.facebook.com/
...
curl: (60) SSL certificate problem: unable to get local issuer certificate
More details here: https://curl.haxx.se/docs/sslcerts.htmlThe 95.59.142.120 IP address is iqala.kz from https://censoredplanet.org/kazakhstan#certificates. Other IP addresses in KZ will likely work as well, as long as there is a functioning TLS server behind them.
Other interesting observations:
Starting 2019-08-07, there were reports that the government of Kazakhstan ceased the MITM. They characterized it as a successful, temporary "test," and said that users who had installed the root CA certificate could delete it.
https://bugzilla.mozilla.org/show_bug.cgi?id=1567114#c69 (archive)
The Kazakhstan government declared yesterday it ends testing of the certificate, claiming it was a success [1]. Mr. Tokaev, the President of the Republic of Kazakhstan, thanked the National Security Committee for the testing [2] and various sites started posting instructions on removing the certificate from phones [3]. [1] https://tengrinews.kz/kazakhstan_news/knb-zavershil-testirovanie-sertifikata-bezopasnosti-375822/ (archive) [2] https://rus.azattyq.org/a/30096331.html (archive) [3] https://www.zakon.kz/4980549-kak-udalit-sertifikat-bezopasnosti-s.html (archive)
The Kazakh security NGO TSARKA is claiming credit (archive) for moderating a discussion with the government to stop the MITM.
Over the past two weeks, residents of Nur-Sultan, capital of Kazakhstan, have faced problems with access to the Internet. Officials explained that it was happening because of the new security system's testing.
It was said to be a part of «Cyber shield of Kazakhstan» which allows to increase the country's defense capability and counteract information wars. According to previously received statistics, the authorities managed to inspect a third of all traffic in the Nur-Sultan city.
TSARKA assumed the role of a moderator in this situation and it seems that we managed to reach the top management of the country and convey our arguments. From our point of view, the optimal solution has been reached in the course of negotiations with the participants of the process.
A few hours ago we were officially informed that the tests were completed, all the tasks set during the pilot were successfully solved. Those who have established the National Certificate may delete it since it will no longer be needed. The need for its installation may arise in cases of strengthening the digital border of Kazakhstan within the framework of special regulations.
We don’t know how you guys are, but we breathed a sigh of relief when we heard about this news. Everyone got their own: we got the free Internet, the government got an instrument for fighting digital weapons.
P.S. We are especially proud of our role in the process. It was difficult not to fall into a negative point and maintain neutrality, but now we are satisfied with ourselves.
A Reuters story (archive) refers to but does not link to a tweet by the President of Kazakhstan Kassym-Jomart Tokayev that says he personally ordered the MITM. I found 4 recent tweets that are related:
@TokayevKZ 2019-08-06 16:55:12 +00:00 (archive)
КНБ по моему поручению провёл тестирование сертификата безопасности в рамках программы Киберщит. Доказана защищенность информационного пространства РК и возможность использования сертификата только в случаях вторжения извне. Неудобств пользователям интернета нет. Благодарю КНБ.
Machine translation:
The KNB, on my behalf, tested the security certificate as part of the Cybershield program. The security of the information space of the Republic of Kazakhstan and the possibility of using the certificate only in cases of intrusion from the outside are proved. There is no inconvenience to Internet users. Thanks to the KNB.
@TokayevKZ 2019-08-06 17:44:38 +00:00 (archive)
Менің тапсырмам бойынша ҰҚК Киберқалқан бағдарламасы аясында сертификат қауірсіздігін тесттен өткізді.ҚР ақпарат кеңістігі қауіпсіздігі және сертификатты сырттан қауіп төнген жағдайда ғана қолдану мүмкіндігі дәлелденді. Интернет қолданушыларға қолайсыздық жоқ.ҰҚК алғыс білдіремін
Machine translation:
On my order, the KNB has tested the certificate's uncertainty within the cybercrime program. The ability to use the information space security and certification only in case of external threats has been proven. There is no disadvantage for Internet users
@TokayevKZ 2019-08-06 18:31:37 +00:00 (archive)
Быстрое завершение тестирования сертификата безопасности по программе Киберщит показало высокий уровень технической оснащенности на случай кибератак извне, ранее имевших место неоднократно. Главное - неудобств пользователям интернета в КЗ не будет. Все опасения не имеют оснований
Machine translation:
The quick completion of testing the security certificate for the CyberShield program showed a high level of technical equipment in case of cyber attacks from the outside, which previously took place more than once. The main thing is that there will be no inconvenience to Internet users in KZ. All fears have no reason
@TokayevKZ 2019-08-06 19:17:10 +00:00 (archive)
Киберқалқан бағдарламасы б-ша қауіпсіздік сертификатын тестілеудің жедел аяқталуы сырттан қауіп төнгенде техникалық жабдықталу деңгейінің жоғары екенін көрсетті. Мұндай жағдайлар бұрын болған. Ең бастысы- ҚР интернет қолданушыларына қолайсыздық болмайды. Қауіптенуге еш негіз жоқ.
Machine translation:
The instantaneous end-to-end security test of the cybercrime program has demonstrated a high level of technical capability when exposed to external threats. There were such cases before. The most important thing is that there is no inconvenience for Internet users in Kazakhstan. There is no reason to be in danger.
Censored Planet's live monitoring page (archive) confirms a stop of MITM late on 2019-08-06 UTC:
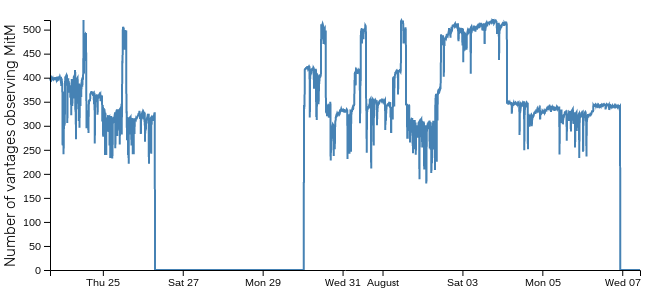
@rensafi from Censored Planet gives a precise date and time for the end of interception, according to their active measurements: 2019-08-07 08:50 +0600 (Almaty time), which is 2019-08-17 02:50 UTC. The axis on the graph above shows Michigan time (Eastern Daylight Time), so the drop appears before midnight, at 2019-08-16 22:50 -0400.
Mozilla and Google have blog posts today that say they will block the certificate in Firefox and Chrome. (Although the MITM has ceased, this will protect users who already have it installed from attacks in the future.)
https://blog.mozilla.org/blog/2019/08/21/mozilla-takes-action-to-protect-users-in-kazakhstan/ (archive)
Today, Mozilla and Google took action to protect the online security and privacy of individuals in Kazakhstan. Together the companies deployed technical solutions within Firefox and Chrome to block the Kazakhstan government’s ability to intercept internet traffic within the country.
https://blog.mozilla.org/security/2019/08/21/protecting-our-users-in-kazakhstan/ (archive)
To protect our users, Firefox, together with Chrome, will block the use of the Kazakhstan root CA certificate. This means that it will not be trusted by Firefox even if the user has installed it. We believe this is the appropriate response because users in Kazakhstan are not being given a meaningful choice over whether to install the certificate and because this attack undermines the integrity of a critical network security mechanism. When attempting to access a website that responds with this certificate, Firefox users will see an error message stating that the certificate should not be trusted.
https://security.googleblog.com/2019/08/protecting-chrome-users-in-kazakhstan.html (archive)
Chrome will be blocking the certificate the Kazakhstan government required users to install:
- Common Name
- Qaznet Trust Network
- SHA-256 Fingerprint
- 00:30:9C:73:6D:D6:61:DA:6F:1E:B2:41:73:AA:84:99:44:C1:68:A4:3A:15:BF:FD:19:2E:EC:FD:B6:F8:DB:D2
- SHA-256 of Subject Public Key Info
- B5:BA:8D:D7:F8:95:64:C2:88:9D:3D:64:53:C8:49:98:C7:78:24:91:9B:64:EA:08:35:AA:62:98:65:91:BE:50
The certificate has been added to CRLSet. No action is needed by users to be protected. In addition, the certificate will be added to a blocklist in the Chromium source code and thus should be included in other Chromium based browsers in due course.
I haven't yet found any related changes in the Firefox or Chromium source code repositories.
Using crlset-tools, I verified that the certificate's public key fingerprint is present in CRLSet version 5348:
$ date -u --iso=sec
2019-08-21T14:33:26+00:00
$ ./crlset fetch > crl-set
Downloading CRLSet version 5348
$ ./crlset dumpSPKIs crl-set | grep -i ^b5ba
b5ba8dd7f89564c2889d3d6453c84998c77824919b64ea0835aa62986591be50@darkk finds another article that says Apple will also block the certificate in Safari.
https://techcrunch.com/2019/08/21/google-mozilla-kazakhstans-browser-spying/ (archive)
Apple said it had also taken action to “ensure the certificate is not trusted by Safari and our users are protected from this issue,” said a spokesperson.
A commenter at the Mozilla Bugzilla reported on 2019-09-06 that a second certificate has been made available at http://qca.kz/security.cer (link doesn't work outside Kazakhstan). I downloaded the file using a VPN Gate server and archived it at https://archive.org/details/qazca-security.cer-ca-certificate. For me currently, http://qca.kz/ returns status code 500, but direct links to the certificate files work.
Saw the article https://myc.news/ It says that again in Kazakhstan they are blocking the certificate in Safari
Saw the article https://myc.news/ It says that again in Kazakhstan they are blocking the certificate in Safari
@gorbatkomark0 Do you have a link to the specific article? I cannot find it. I tried searching the site for "сертификат", "сафари", "казахстан" and did not find anything that looked like it was about TLS.
Via @darkk, there are reports that ISPs in Kazakhstan have today (2019-07-18) begun to MITM TLS connections and instruct users to install a custom root cert. This is something that the government of Kazakhstan had threatened in 2016, but not followed through upon until now.
There is a Firefox ticket with links to more information.
Archive of certificate download site: https://web.archive.org/web/20190718174154/http://qca.kz/ Copy of certificate files, downloaded by me just now: qazca-20190718.zip
Cached images from imgur: