So the only occurrences of "WireGuard" in the Diag Report are in:
*************************************************
Network Adapter(s) Info:
*************************************************
Name InterfaceDescription ifIndex Status MacAddress LinkSpeed
---- -------------------- ------- ------ ---------- ---------
Ethernet Realtek PCIe GbE Family Controller 14 Up 50-46-5D-8D-83-71 1 Gbps
TobiTunnel WireGuard Tunnel 7 Up 100 Gbps
Caption : [00000002] Realtek PCIe GbE Family Controller
GUID : {98D2E49D-710A-48FF-ABDC-89BA36048B9F} = eth1
Index : 2
InterfaceIndex : 14
Manufacturer : Realtek
NetConnectionID : Ethernet
PNPDeviceID : PCI\VEN_10EC&DEV_8168&SUBSYS_85051043&REV_09\4&21A1C3AE&0&00E5
Caption : [00000012] Wintun Userspace Tunnel
GUID : {3B758425-0C12-5B9B-708D-C6F0A39B222C}
Index : 12
InterfaceIndex : 7
Manufacturer : WireGuard LLC
NetConnectionID : TobiTunnel
PNPDeviceID : ROOT\NET\0000Can you try to capture with TShark (tshark.exe should be in the same directory as Wireshark.exe), passing it the command-line argument -i \Device\NPF_{3B758425-0C12-5B9B-708D-C6F0A39B222C} ?
What does the command ipconfig/all print?

Hello everyone, I faced a problem regarding a missing/inaccessible adapter with Wireshark/Scapy created by Wireguard. nmap --iflist returning: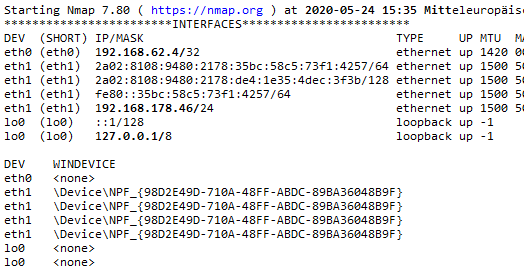 eth0 is the Virtual Adapter from Wireguard. The adapter working correctly, but I am unable to sniff data with npcap/scapy/Wirteshark.
NMap -> 7.80
Scapy -> 2.4.3
Wireshark -> 3.2.4
Wireguard -> 0.1.0
NPcap -> 0.9991
eth0 is the Virtual Adapter from Wireguard. The adapter working correctly, but I am unable to sniff data with npcap/scapy/Wirteshark.
NMap -> 7.80
Scapy -> 2.4.3
Wireshark -> 3.2.4
Wireguard -> 0.1.0
NPcap -> 0.9991
Diag Report: DiagReport-20200524-155041.txt
I tried mutliple releases and the bug is reproducable on a second device. I would be really glad if you could help regarding this problem.