Team's Response
Dear tester,
The team has discussed and decided to categorize this bug as not in scope and downgraded it to severity of low. The following are the justifications:
- The course has specified that the data files are protected by default on the course website as seen below.
-
Password files stored locally is bound to face some sort of security issues. Due to the constraint of this project, we are unable to implement this more securely and thus the issue is posted to the future after v2.1.
-
We feel that this would be a very rare occurrence to users as well.
Duplicate status (if any):
--
Details: While the mechanism behind the password is kept secret from the user (see Screenshot 1), it is easily exploitable due to the 2 following reasons:
0in the password file represents the empty password field (see Screenshot 2). Hence any malicious party is able to change the existing password in the file to 0, and then enter the application by just pressing enter when asked for the password. This means that the password set by the user essentially is useless since anyone can modify the file and change it to 0. This poses a major security risk to the user, and is a major flaw in the password system of the application.Steps to Reproduce:
P@ssw0rd12345)0in it (like in Screenshot 2)Expected: Change in password to be empty is detected and appropriate measures are taken
Actual: New password is set to be empty, which means just pressing enter when the password is asked lets the user in.
Screenshot: 1.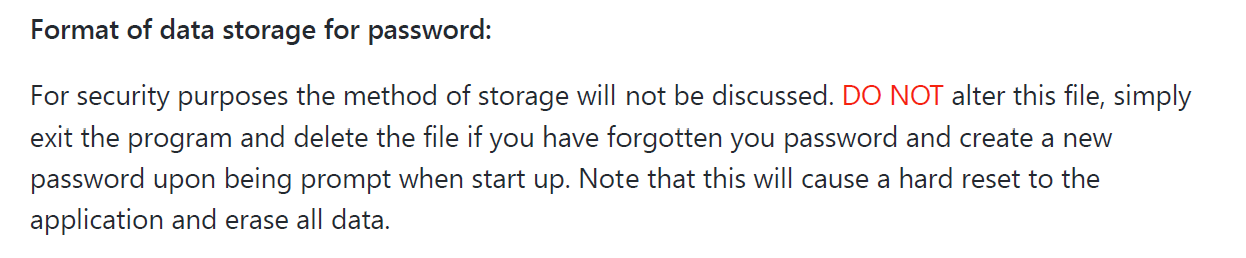
[original: nus-cs2113-AY2425S1/pe-interim#429] [original labels: severity.Medium type.FunctionalityBug]