I noticed similar behavior where the onAuthenticationSucceeded was being called (in KeychainModule.java but I was still getting the UserNotAuthenticatedException. Basically the decryption key's authentication was expiring before the cipher could get initialized. (probably since I was running in a debug environment, but could also happen with slower devices)
I was able to get it to work by extending the UserAuthenticationValidityDuration attribute of the key from 1 second to 5. In my case, it was using the RSA key, so the change was in the CipherStorageKeystoreRsaEcb.java file, around line 228
return new KeyGenParameterSpec.Builder(alias, purposes)
.setBlockModes(BLOCK_MODE_ECB)
.setEncryptionPaddings(PADDING_PKCS1)
.setRandomizedEncryptionRequired(true)
.setUserAuthenticationRequired(true)
.setUserAuthenticationValidityDurationSeconds(5)
.setKeySize(ENCRYPTION_KEY_SIZE);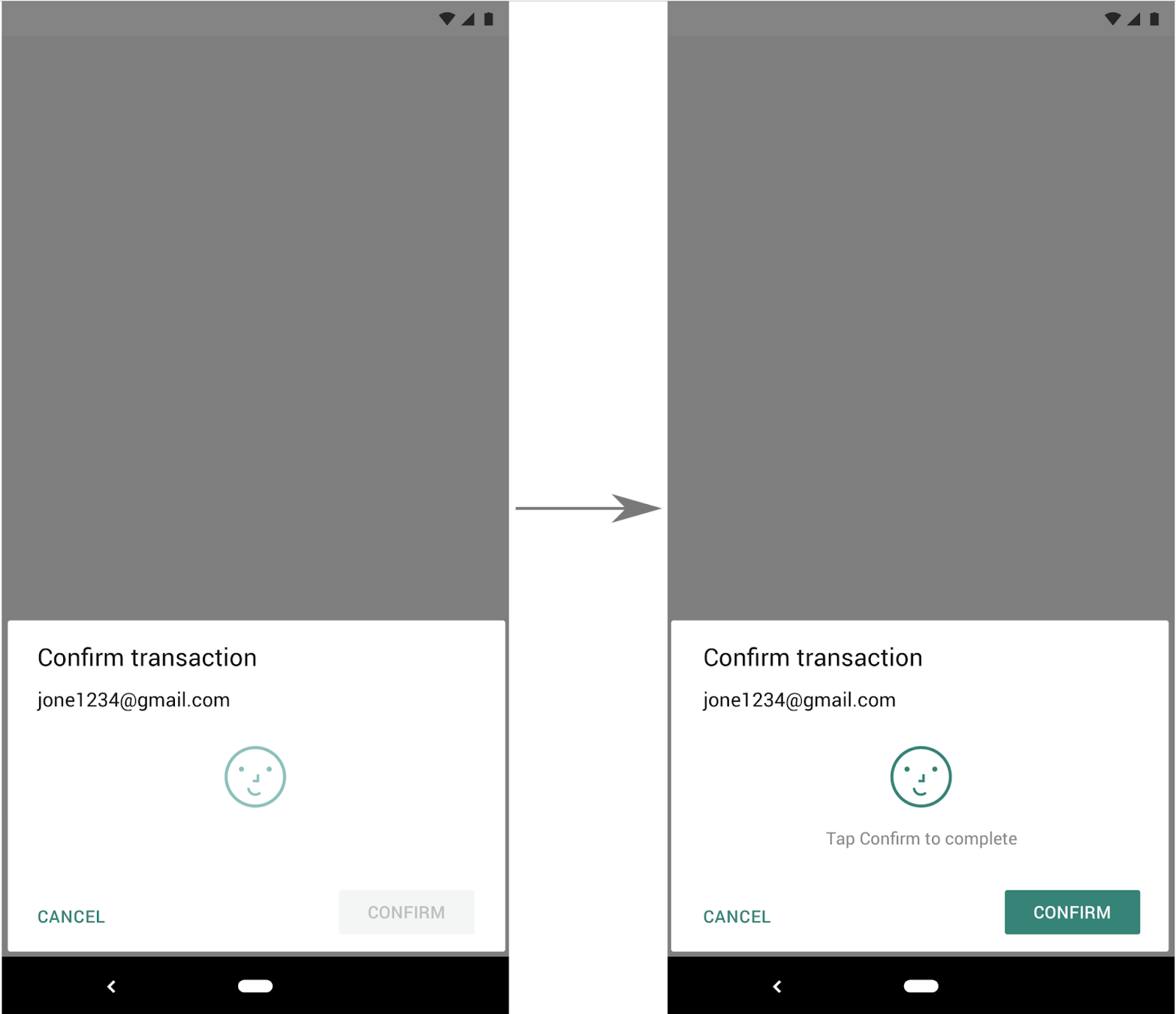
I get this error when trying to retrieve credentials stored in the keychain on Android devices. IMHO this is the effect of following exception being thrown: UserNotAuthenticatedException.
This is my code:
The error is thrown at
Keychain.getGenericPassword. On iOS the code works fine. Any idea or workaround for this?