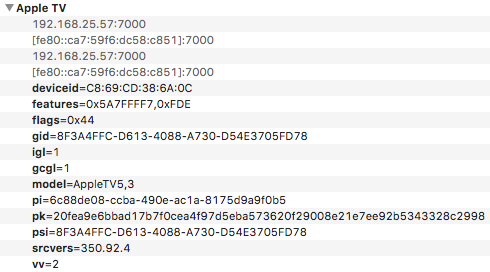
Thanks for the heads up. I will look into it, but I am not very optimistic about being able to solve it. Looks like it might be a hard nut to crack. I also don't have a ATV 4th gen, though perhaps testing on a 3rd gen with Device Verification enabled is good enough.
I will add a few warnings to the docs about upgrading to tvOS 10.2.
 Changes that Apple made in tvOS 11 beta 1 also broke AirParrot 2 and Beamer's ability to stream video to Apple TV.
Play request fails with 400 Bad Request Error.
Changes that Apple made in tvOS 11 beta 1 also broke AirParrot 2 and Beamer's ability to stream video to Apple TV.
Play request fails with 400 Bad Request Error.
TVOS 10.2 requires Device Verification, which cannot be turned off anymore. Since forked-daapd does not support Device Verification I am not able to stream music to my Apple TV anymore. I can see that Airparrot has found a work-around. Is it possible for you to update forked-daapd to reenable this feature again? Thanks in advance