One advantage of this is that by splitting sessions from friend requests, our core application logic won't touch the signal protocol. All we would need to do is implement a mechanism which handles the passing of a pre key bundle to another user and ensuring a session is setup before messages are sent.
A rough implementation of this would be:
< A wants to send a message to B>
Do we have a session with B?
- No? Send out a session request and put the original message on hold (save it to db or something)
- Yes? Send the message
< B receives session request from A>
Process the pre key bundle
Send out a session request complete message (or any message encrypted with the new session)
< A received encrypted message from B>
Do we have pending messages?
- Yes? Start sending them out


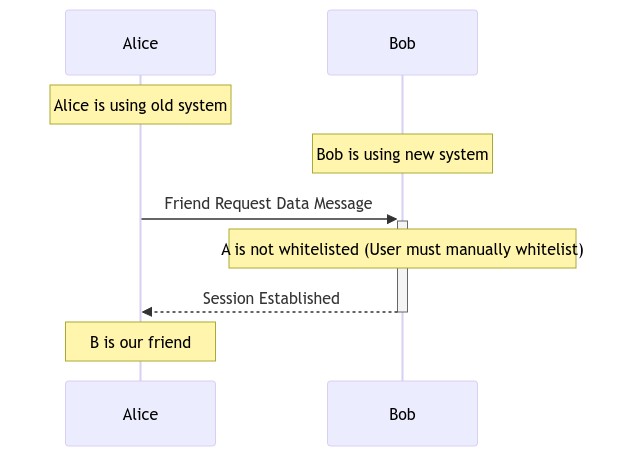
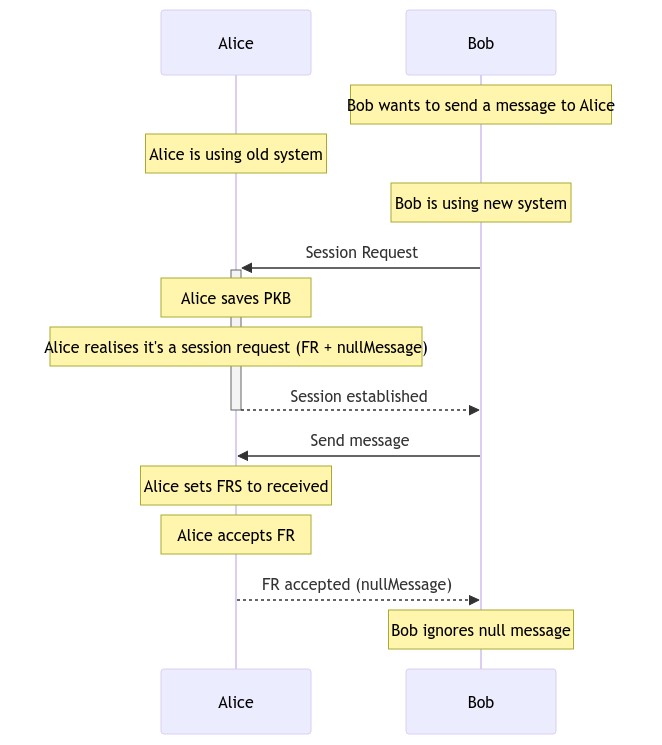
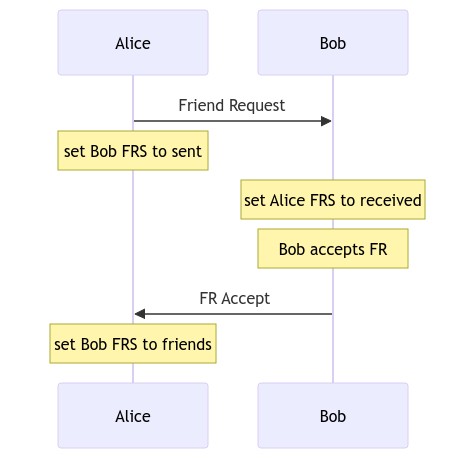
Originally having a session with a pubkey was tied up to the friend request logic. We then introduced a concept of a "session request", which would let two pubkeys establish a session without explicitly being friends. This was necessary for small closed groups as members of each group need to have pairwise sessions with each other even if they don't already have a private conversation. (The concept of a "conversation" is also annoyingly tied up to having a session, but this is probably out of scope of this proposal.) However, there is still no clear separation between the two, for example, multidevice still uses "friend requests" to establish a session between linked devices (and thus the "Please accept to enable messages to be synced across devices" message). I believe these are very different concepts and they should be isolated.
I propose building an abstraction with an API that would allow exchaning (regular as well as "control") messages between any two pubkeys, without the caller having to worry about establishing a session first. Keeping the session logic separate from everything else should greatly recude the complexity of the codebase leading to fewer corner cases (bugs) and faster development of new features.
I also propose accepting session requests automatically, which is already done for members of the same closed group. I believe the friend/not-friend relationship logic should be handled on the level above encryption. Say if we are not friends, the application will just not display any message, and if the user is banned, the messages could be dropped without even hitting the databse. Giving someone we don't like the ability to encrypt messages for us is not really that much. The only downside I see is that one might spam a user with session requests, but you can already do almost the same amount of damage with just friend requests. The latter might even be more annoying to the user since it will clutter the UI.
This proposal should line up well with the refactoring of the sending/receiving pipelines in Desktop codebase.