Looking good!
IMHO the visible and editable form fields for the ORCID ID should be removed altogether and only allow properly authenticated ID's like ORCID guidelines suggest. This means that the only way of inserting ORCID ID's to OJS would be via authentication using the ORCID API.
If a user account has an authenticated ID, that could be used when creating the initial author profile. With the secondary authors the collection should happen with emails with links leading to a handler that whould show the suggested article and means to connect the authors ID to the article metadata.
In any case, I think it would be important to discuss any plan with ORCID before doing too much work.
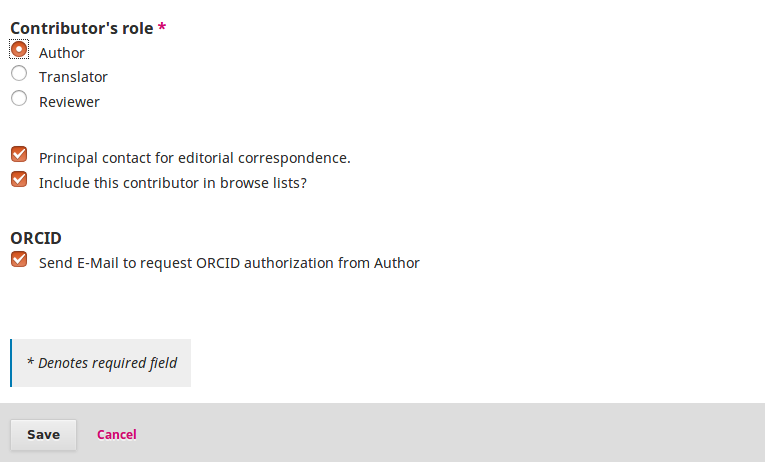 is enabled and save button is clicked. Is this preferred or should we implement a button to send requests at any time?
is enabled and save button is clicked. Is this preferred or should we implement a button to send requests at any time?

Current Status
README.md
Previous plugins
Button on registration form : Autofill firstname, lastname after validation
Input button on profile: validate and automatic-id adding
✔
✔
Display orcid id under the author on the monograph's view page
✔
References