The original questions was how to they identify vulnerability
Open prince-chrismc opened 5 years ago
The original questions was how to they identify vulnerability
I've been using Vuls with their fast scan mode. This queries the package manager to find the list of installed packages, it then runs an upgraded to get the change logs to see what CVEs were fixed in the upgrades
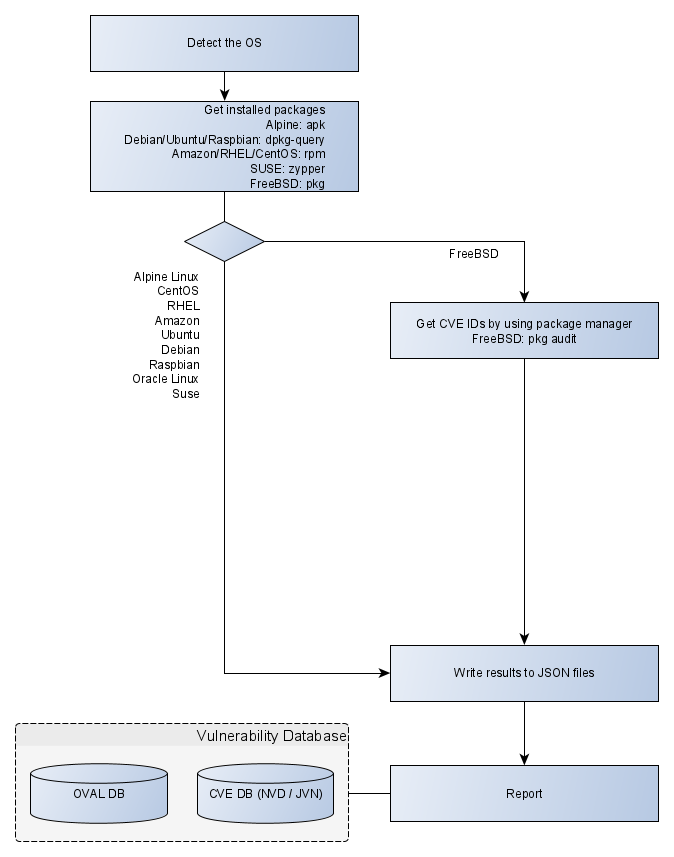
details for how anchore does it [here] which is very similar to vuls
both use the same databases https://anchore.com/cloud/docs/image-security/
Shockingly Anchore uses the package manager of the OS to obtain the packages!
It gets worse! They actually parse the package manager files in the image to determine which packages are available
How do they Identify images