Hi @kakaroto. You can get it through several ways:
- setup a breakpoint in kernel space (cs for kernel is 0x8, like "0x8:
"); - manually change cs register;
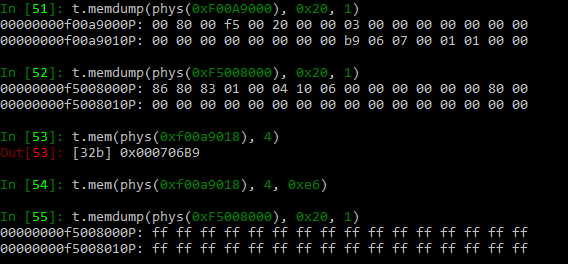
You can also use the suffix "P" to access physical memory (like "0xf0080004P"). ME doesn't have I/O ports, if I recall correctly.
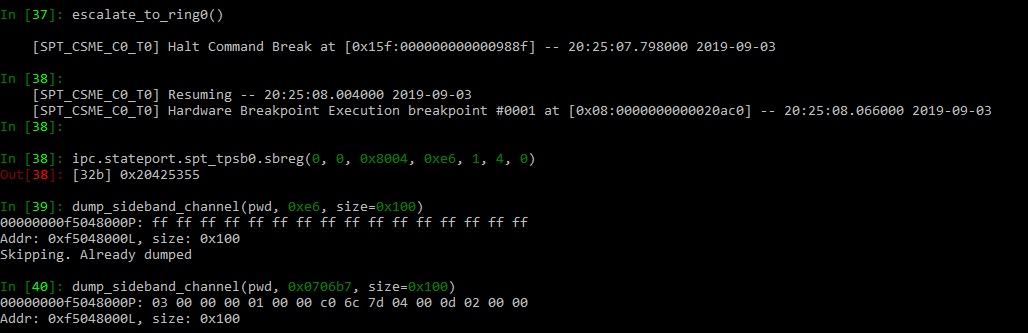 and :
and :


Hi, I have a question and maybe it's a dumb one but I can't seem to figure it out. When the JTAG is enabled, it's from the BUP process, which is a user space program, at Ring-3. Is there a way to escalate privilege to kernel mode? I can't seem to be able to set a breakpoint in kernel code, modifying the TSS doesn't work and thread.step() doesn't actually seem to work either (does the same as thread.go()) I'm not sure how we're supposed to get the full access to the ME from Ring-3, I'm trying to just read io port 0x80 for example (or any I/O port for that matter) and it all returns 0xFFFFFFF and that's because the TSS for BUP process has IOPB empty. Any advice? Thanks!