Use esil, anal.strings and theres another one that statically analyzes stack movements to find strings constructed like this but i dont remember ir right now.
and no, you wont see this in the strings list, because the string list you get is from RBin, aka by parsing the binary headrs, not by emulating the program, you’ll find a flag
On 14 Aug 2018, at 15:39, MariasStory notifications@github.com wrote:
Please decode strings from some simple obfuscation: https://user-images.githubusercontent.com/6576335/44095047-134280b8-9fd8-11e8-98c0-ad19ff6c95cf.png It might be already implemented, but it would be nice to have the string in the strings list ;-)
— You are receiving this because you are subscribed to this thread. Reply to this email directly, view it on GitHub https://github.com/radare/radare2/issues/11085, or mute the thread https://github.com/notifications/unsubscribe-auth/AA3-lsdf6jgcfgvRpmpbTXhwOCTRvFrmks5uQtMggaJpZM4V8dID.
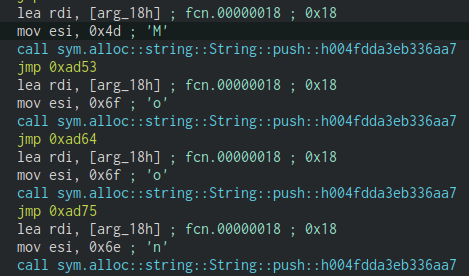

Please decode strings from some simple obfuscation:
It might be already implemented, but it would be nice to have the string in the strings list ;-)