try to type this before typing "exploit" = set AutoLoadStdapi true
Closed zisis912 closed 3 years ago
try to type this before typing "exploit" = set AutoLoadStdapi true
i actually still dont know why the meterpreter session died but i see in your screenshot you cant load "shell" command for the fix of "Unknown Command: shell" issue just type set AutoLoadStdapi true before exploiting
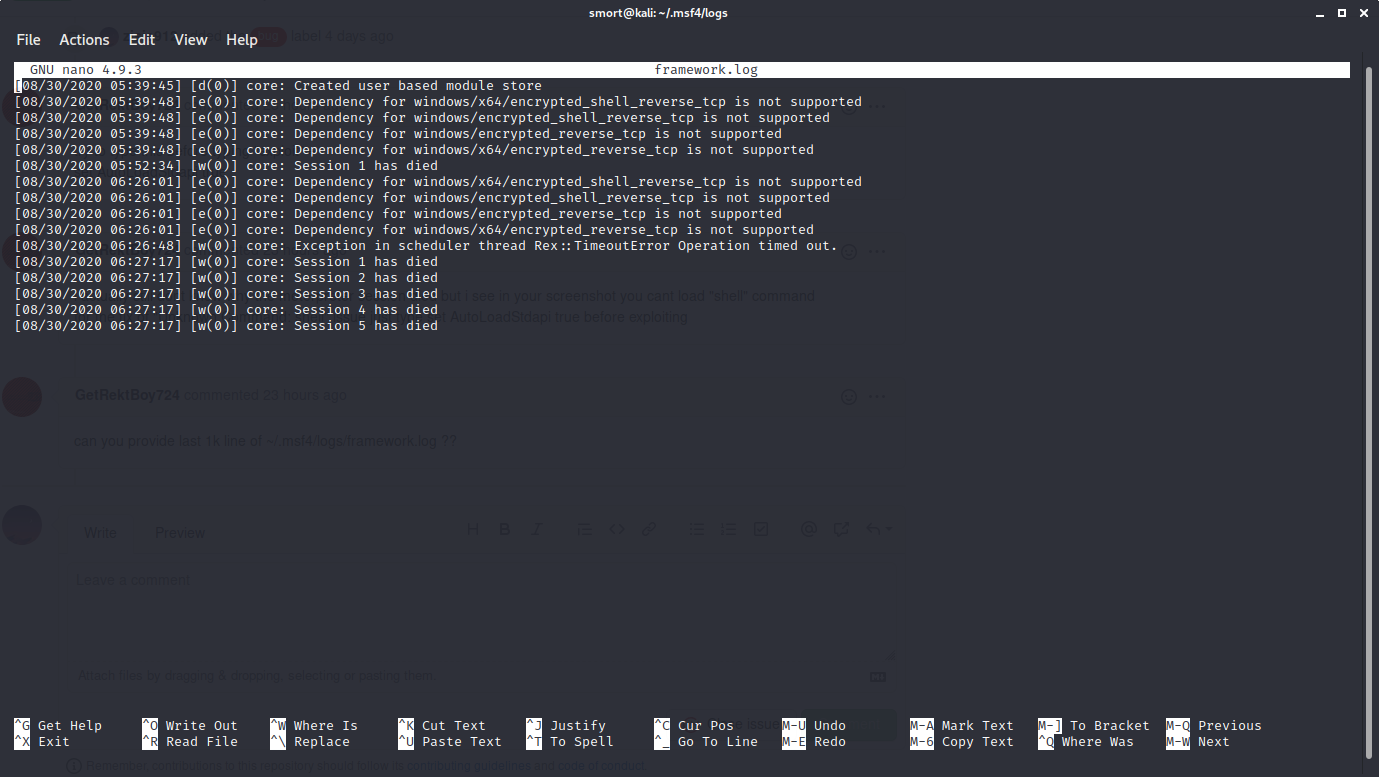
can you provide last 1k line of ~/.msf4/logs/framework.log ??
framework.log is like 15 lines, not one thousand lines, but here you go
The commands I used in the console to backdoor the device were "use exploit/multi/handler", and "set payload android/meterpreter/reverse_tcp". It had nothing to do with windows
after that I set the LPORT and the LHOST, and type exploit. Do you think the issue might be that I used LPORT 8080 instead of 4444?
after that I set the LPORT and the LHOST, and type exploit. Do you think the issue might be that I used LPORT 8080 instead of 4444?
i think yes...try to change it to 4444 cause there is a possibility that the port is used by other service running on victim
also is there an AV in your android?? cause maybe your AV immediately kill the connection or kill the process of the meterpreter
if there is no AV in your android/victim you can check the connection... do you use port forwarding?? or do you use public ip??
both the phone and the laptop are connected to my home's network. Also, I got numerous AV alerts, but I discsarded them all
hmmm
try to exploit other device....maybe you can exploit your own device first to make sure its not msf fault
and also if you want to gain full access of the victim type this before exploiting : set AutoLoadStdapi true maybe it will fix both issues
who knows?? :)
umm ok. I'll try. But do oyu think settings the LPORT to 4444 instead of 8080 will make a difference?'
yeah cause port 8080 was very common
framework.log is like 15 lines, not one thousand lines, but here you go
i see in here to there is a problem tho the problem is : "core : Exception in scheduler thread Rex::TimeoutError Operation timed out"
@wvu-r7 can you help this poor guy ?? (no offense)
Nope. I forgot how to use Metasploit.
lmao
Nope. I forgot how to use Metasploit.
lmao how do you forget how to use metasploit ??!! :)
Hi!
This issue has been left open with no activity for a while now.
We get a lot of issues, so we currently close issues after 60 days of inactivity. It’s been at least 30 days since the last update here. If we missed this issue or if you want to keep it open, please reply here. You can also add the label "not stale" to keep this issue open!
As a friendly reminder: the best way to see this issue, or any other, fixed is to open a Pull Request.
hello bot
hey @zisis912 sorry this is taking so long to get back to you, it's hard to say for certain with the info here but I think it was mentioned before that AV might be killing it and that definitely looks to be the case I know you said you discarded the AV alerts but it might still be what's killing your session, have a go with it fully turned off/uninstalled if you get any more information that points to this being a bug with metasploit rather than an AV issues please do let us know
@dwelch-r7 so you think that the android device is the problem and not metasploit?
I think that's likely possibility yea, especially since it's running AV
I haven't installed any AV on the phone, it is the default Play Protect that most phones have. The testing phone is a Huawei Y7
You can try setting the ExitOnSession to false and use android/meterpreter/reverse_http and see if that solves your problem....
hey ! I'm having the same issue has you, i create a session but i can't execute commands, then after few second the sessions die, I have a ONEPLUS 6, i don't have any AV and using port 4444 or 8080 does not help too :/ i will look on some kali forums to to see if I found something
As the guy above said, its very likely that play protect, the built in play store's av is blocking the connection after a bit
Hi!
This issue has been left open with no activity for a while now.
We get a lot of issues, so we currently close issues after 60 days of inactivity. It’s been at least 30 days since the last update here. If we missed this issue or if you want to keep it open, please reply here. You can also add the label "not stale" to keep this issue open!
As a friendly reminder: the best way to see this issue, or any other, fixed is to open a Pull Request.
Hi again!
It’s been 60 days since anything happened on this issue, so we are going to close it. Please keep in mind that I’m only a robot, so if I’ve closed this issue in error please feel free to reopen this issue or create a new one if you need anything else.
As a friendly reminder: the best way to see this issue, or any other, fixed is to open a Pull Request.
I think you are trying to use 32 bit payload on 64 bit device and thats causing the issue
Try disable the battery saver: dontkillmyapp.com
I think you are trying to use 32 bit payload on 64 bit device and thats causing the issue
how can I create a 64bit payload?
Migrating the meterpreter to the explorer.exe process solved the issue, the merit is from a colleague of mine
Migrating the meterpreter to the explorer.exe process solved the issue, the merit is from a colleague of mine
what do you mean by migrating?
set AutoRunScript migrate -n explorer.exe
Bonjour les gas ! On dirait que j’ai le même problème que vous! Même si je suis en retard! Qui a une solution please!??
J’ai utilisé android/meterpreter/reverse_tcp et l’exploit est rejeté par un problème (meterpreter session closed ) immediately après sending! Please help!!
set AutoRunScript migrate -n explorer.exe
sorry for the stupid question but where this line supposed to be added? And I'm on linux have this error on an Android...where do I supposed to run and .exe file? Thankyou very much
In the msf interface:
msf > set AutoRunScript migrate -n explorer.exe
set AutoRunScript migrate -n explorer.exe
man for me its even not working :/
I'm facing the same issue is there any proven solution to this problem. I've tried disabling even google play protect but still got the same issue so the problem here is not AV i suppose?
Hey, I encountered the same problem under another payload. The solution was to use another compatible payload with the module I was using that has a normal shell, then upgrade to a meterpreter session, which opened a more stable one. I am not doing android pentest now but thought that this might be helpful for you guys!
remove the port from the url that you execute in the victim phone, example 10.0.0.0/filename.apk don't put 10.0.0.0:4444/filename.apk
Steps to reproduce
I don't know if you will be able to reproduce it, but I make an android backdoor, I test it on my phone, and after 20 seconds it says Session closed. Reason Died. The only way to reproduce is just make an android reverse tcp. I will provide a screenshot so you can see what happens.
This section should also tell us any relevant information about the environment; for example, if an exploit that used to work is failing, tell us the victim operating system and service versions.
Were you following a specific guide/tutorial or reading documentation?
yes, but the session opens successfully. it just dies after that
If yes link the guide/tutorial or documentation you were following here, otherwise you may omit this section. https://www.youtube.com/watch?v=llXb5JmGKXM
Expected behavior
What should happen? the connection shouldnt die
Current behavior
What happens instead? the connection dies
You might also want to check the last ~1k lines of
/opt/metasploit/apps/pro/engine/config/logs/framework.logor~/.msf4/logs/framework.logfor relevant stack tracesSystem stuff
Kali linux 2020.3 intel i3 6006U 4gb ram
Metasploit version
metasploit v5.0.101-dev
Get this with the
versioncommand in msfconsole (orgit log -1 --pretty=onelinefor a source install).I installed Metasploit with:
Source install (please specify ruby version) ruby 2.7.1p83 (2020-03-31 revision a0c7c23c9c) [x86_64-linux-gnu]
OS
What OS are you running Metasploit on? kali linux.
