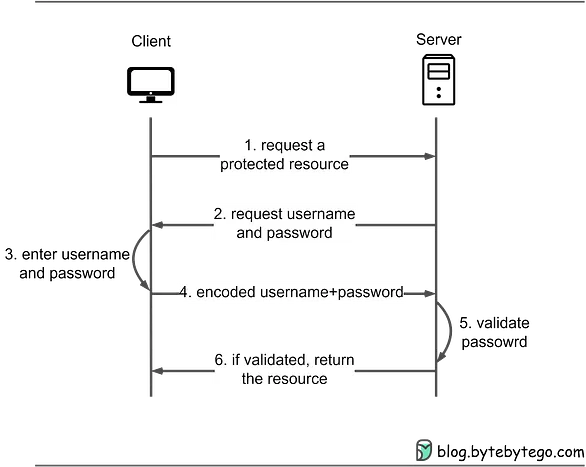
Password Authentication
- How it works: In this method, users enter their unique username and password combination to gain access to protected resources. The entered credentials are checked against stored user information in the system, and if they match, the user is granted access.
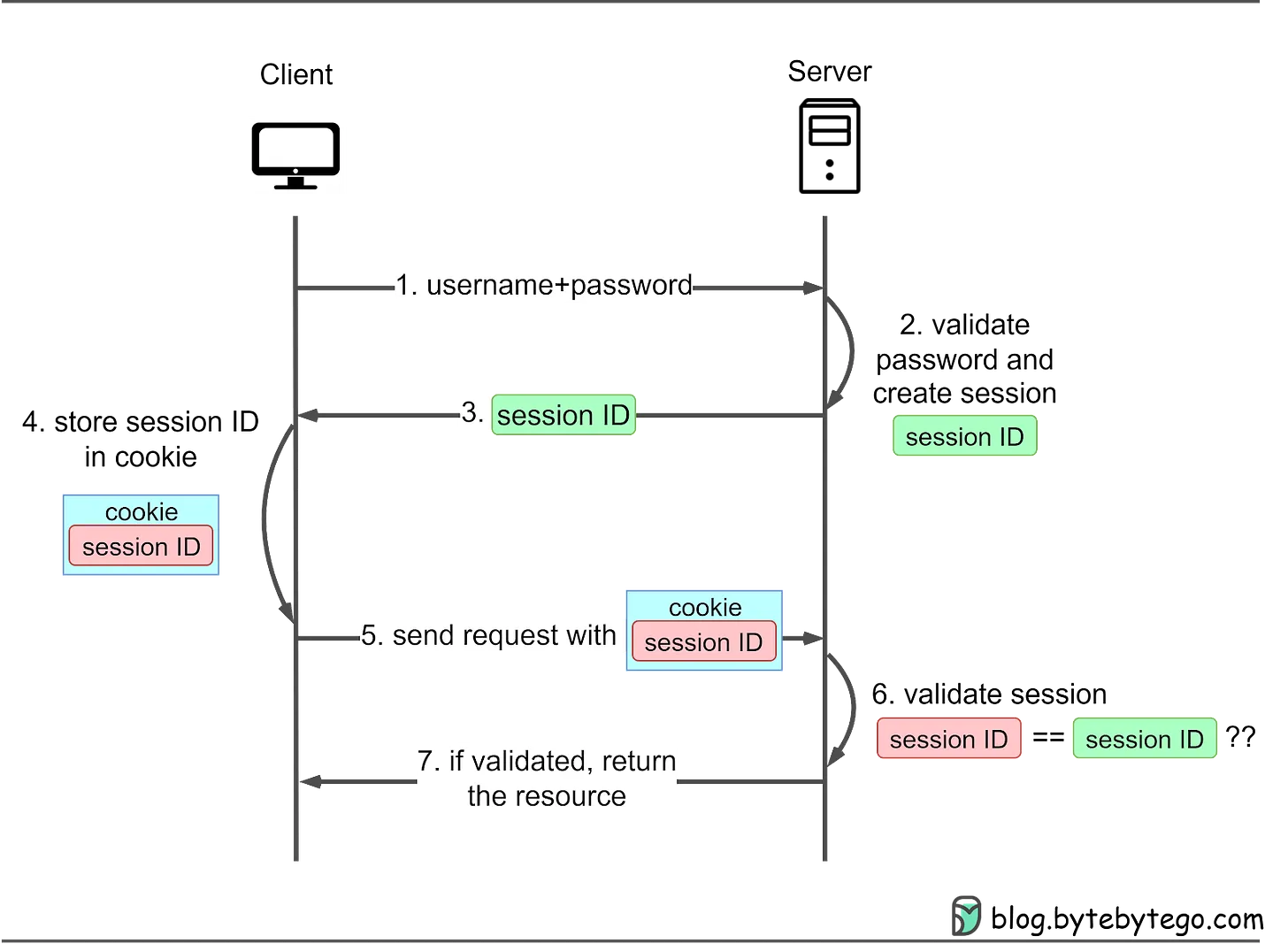
- In the early of internet days, sharing usernames and passwords between services was common but discouraged due to potential misuse.
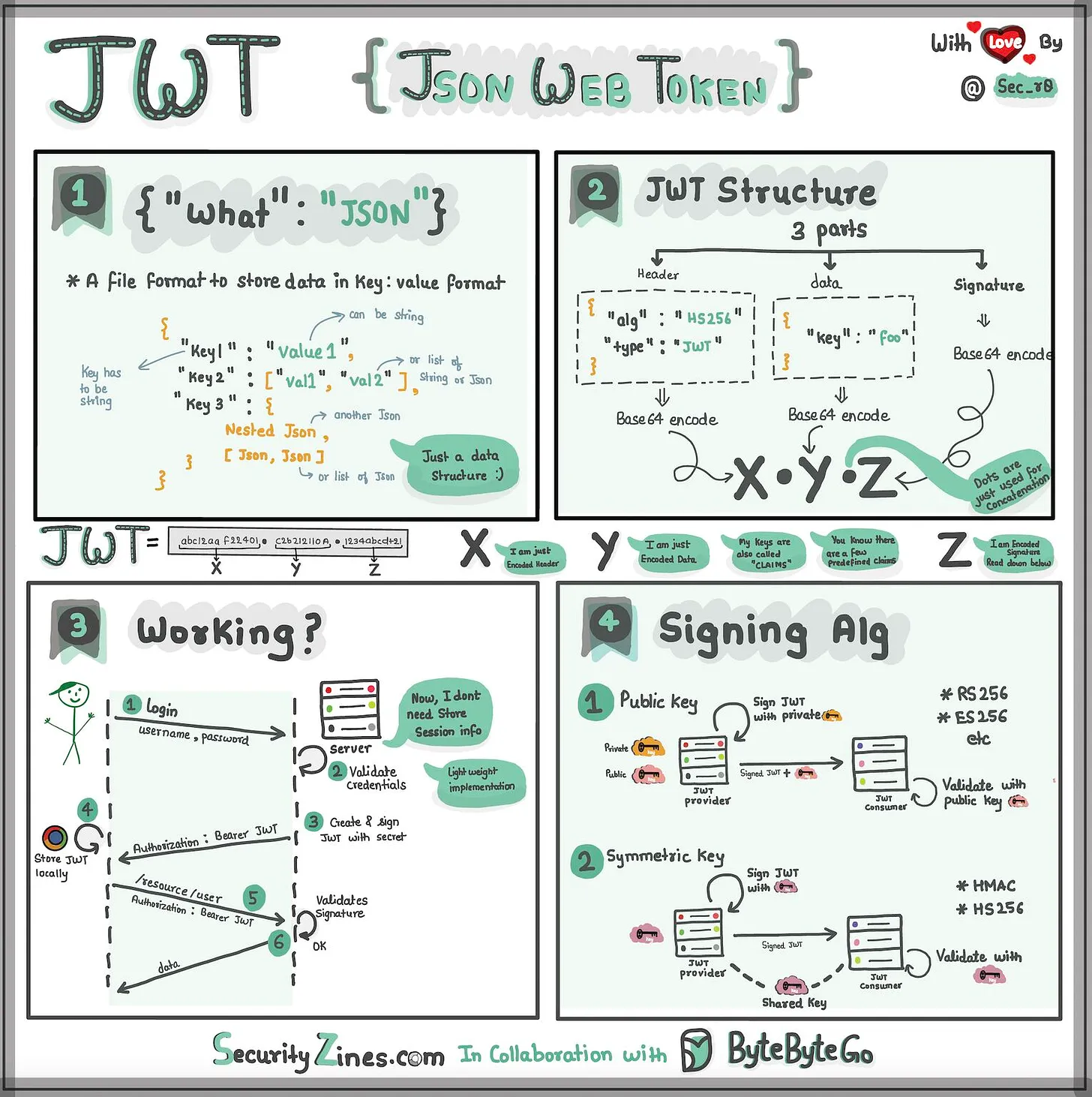
When we use various applications and websites, three essential security steps are continuously at play:
Bellow is a diagram where these methods applied in a typical website architecture
Overview
This article revisits the authentication related common senses.