Maybe it's useful to look at how this problem is approached in Haskell. Here are some relevant slides: https://wiki.haskell.org/wikiupload/b/b4/HIW2011-Talk-Loeh.pdf
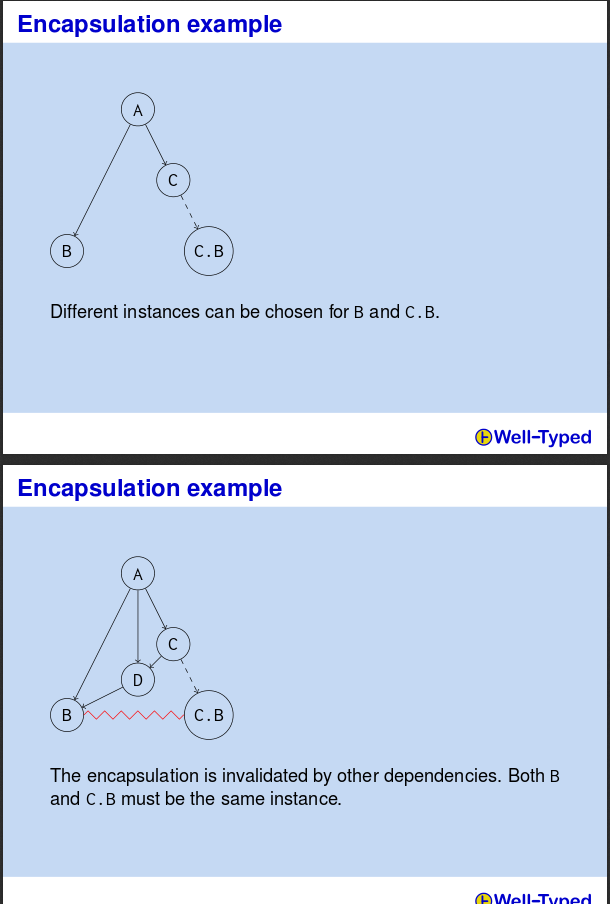
Here is an example of a subtle issue that occurs with private dependencies:
Btw, I found it through this post: http://harry.garrood.me/blog/purescript-why-bower/
Summary
RFC (original, superseded): #1977 RFC: #3516 Cargo tracking issue: https://github.com/rust-lang/cargo/issues/6129 Issues: https://github.com/rust-lang/rust/issues?q=is%3Aissue+is%3Aopen+label%3AF-public_private_dependencies Cargo issues: https://github.com/rust-lang/cargo/issues?q=is%3Aopen+is%3Aissue+label%3AZ-public-dependency Documentation: https://doc.rust-lang.org/nightly/cargo/reference/unstable.html#public-dependency
This feature enables the ability to track which dependencies are publicly exposed through a library's interface. It has two sides to the implementation: rustc (lint and
--externflag), and cargo (Cargo.tomlsyntax, and passing--externflags).This feature was originally specified in rust-lang/rfcs#1977, but was later down-scoped in rust-lang/rfcs#3516.
About tracking issues
Tracking issues are used to record the overall progress of implementation. They are also used as hubs connecting to other relevant issues, e.g., bugs or open design questions. A tracking issue is however not meant for large scale discussion, questions, or bug reports about a feature. Instead, open a dedicated issue for the specific matter and add the relevant feature gate label. Discussion comments will get marked as off-topic or deleted. Repeated discussions on the tracking issue may lead to the tracking issue getting locked.
Unresolved Questions
Steps
Command to update Cargo.lock to minimal versions (rust-lang/cargo#4100)Makecargo publishuse the minimal versions allowed by Cargo.tomlexported-private-dependenciesallow-by-default pre-2024 anddeny-by-default in 2024+ / in the 2024-compatibility lint groupalloworwarn(context from zulip)Non-blocking further improvements
Changes from RFC
cc @rust-lang/cargo @epage