This PR is invalid; marking as spam.
- The going to production checklist states that you would need to run the application behind a proxy such as Cloudflare. Such proxies provide the rate-limiting protection.
- Rate limiting should be boundled with other robot validations such as smart captchas to reduce degradation of the experience for legitimate users that might be having technical difficulties.
- The stated solution is insufficient since, express-rate-limit, does not have any smart ways to identify if it is behind a proxy. In the context of hackathon-starter such smarts are a must-have since, without it, the dev teams can completely stall during a time-crunched weekend when they do server deployments.
https://huntr.dev/users/arjunshibu has fixed the Lack of Rate Limiting vulnerability 🔨. Think you could fix a vulnerability like this?
Get involved at https://huntr.dev/
Q | A Version Affected | ALL Bug Fix | YES Original Pull Request | https://github.com/418sec/hackathon-starter/pull/1 Vulnerability README | https://github.com/418sec/huntr/blob/master/bounties/other/hackathon-starter/1/README.md
User Comments:
📊 Metadata *
hackathon-starteris a boilerplate for Node.js web applications. It lacks rate-limiting, which allows an attacker to brute-force login credentials and mass account creationBounty URL: https://www.huntr.dev/bounties/1-other-hackathon-starter
⚙️ Description *
Lack of rate-limiting in the login and signup page of
hackathon-starter💻 Technical Description *
This fix uses the
express-rate-limitpackage, which is a rate-limiting middleware for express based servers. I've applied it to POST requests issuing to/loginand/signuproutes.🐛 Proof of Concept (PoC) *
Login Brute-Force
/loginand send the POST request to Burp IntruderFound. Redirecting to <a href="/login">/login</a>/instead of/loginhttps://raw.githubusercontent.com/arjunshibu/files/main/hackathon-starter-poc/poc1.png
https://raw.githubusercontent.com/arjunshibu/files/main/hackathon-starter-poc/poc2.png
https://raw.githubusercontent.com/arjunshibu/files/main/hackathon-starter-poc/poc3.png
Mass Account Creation
/signupand send the POST request to Burp IntruderFound. Redirecting to <a href="/">/</a>/and to/signupif there is already a userhttps://raw.githubusercontent.com/arjunshibu/files/main/hackathon-starter-poc/poc4.png
https://raw.githubusercontent.com/arjunshibu/files/main/hackathon-starter-poc/poc5.png
🔥 Proof of Fix (PoF) *
After fix any brute-forcing of login credentials and mass account creation is prevented by responding with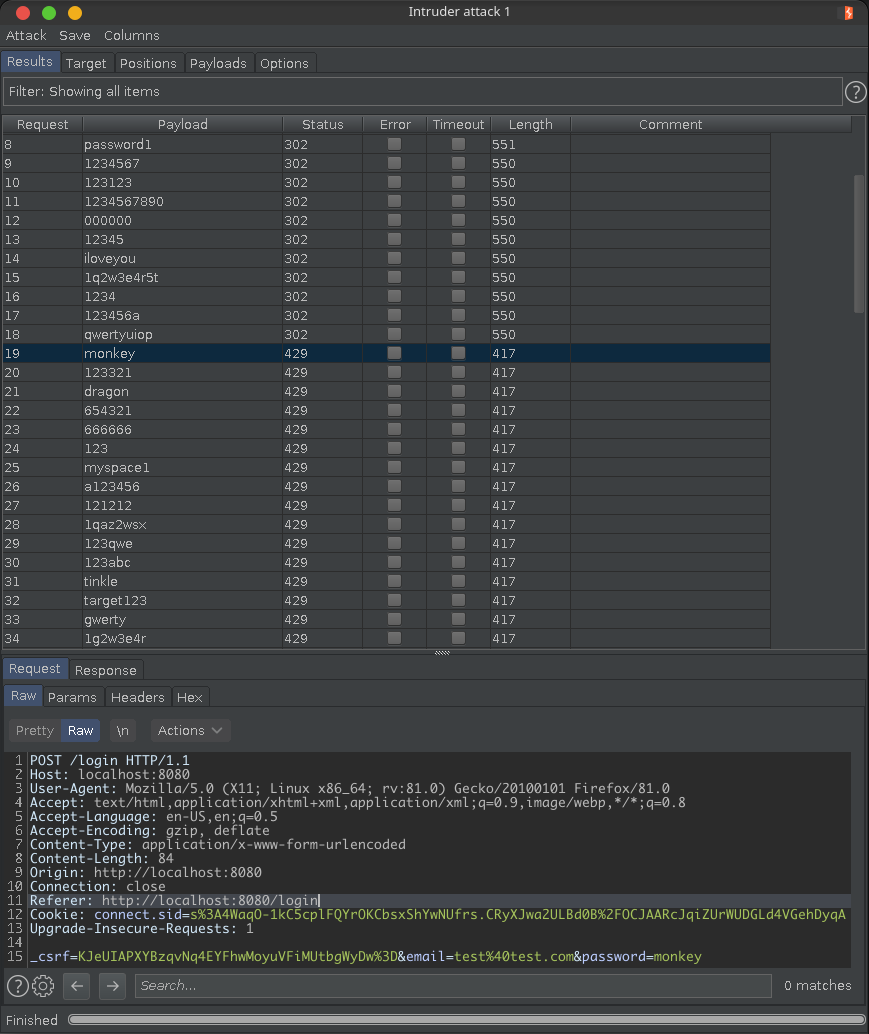
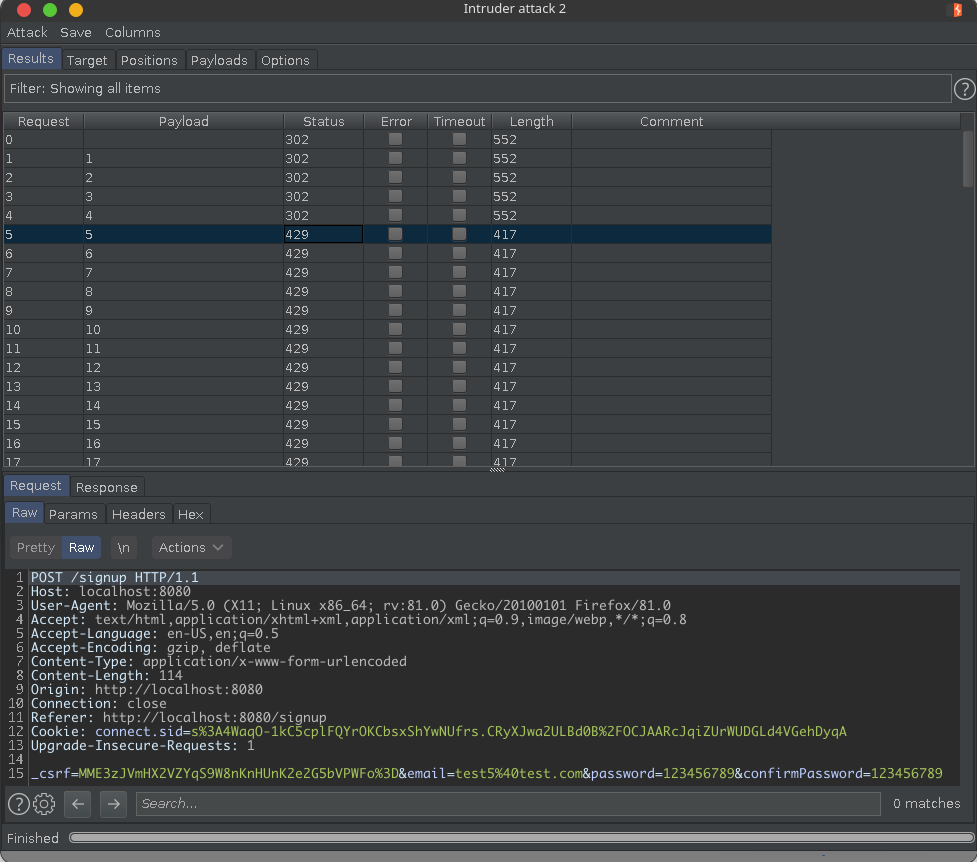
429 - Too Many Requests👍 User Acceptance Testing (UAT)