Hi @DavidXanatos about your https://github.com/sandboxie-plus/Sandboxie/issues/893#issuecomment-860052051 can you give me a link to some tutorial/guide to do this if possible? please
I would like to have at least two active connections on my computer, with things like Firefox using my local IP and Chrome using an OpenVPN connection.
Virtual machines are the only option I can find for now, but they consume too many resources for my taste, I would like to do this in a better way.
I know I can make this kind of things with Proxifier who allows have rules per proxy/program, but I wonder if possible use this with OpenVPN.
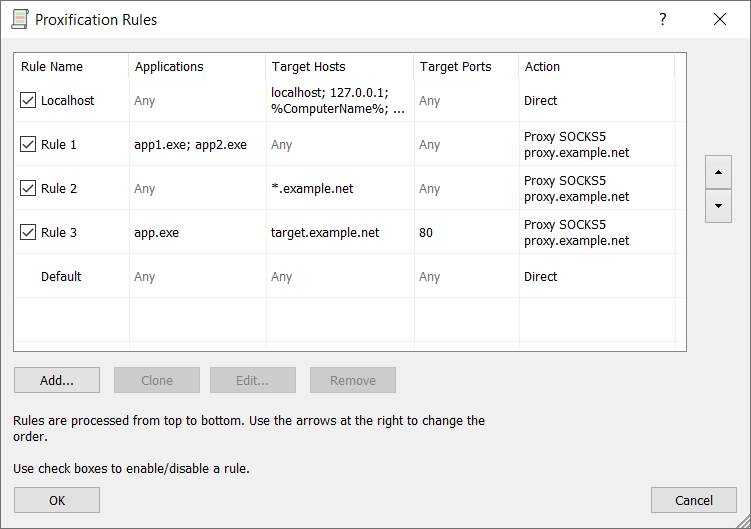
Maybe proxifier (or any other similar software) can be used as an optional third party tool for network options with Sandboxie? I suppose this might be an easier way to do, if possible.
Sandboxie currently blocks network access by denying the access to the underlying windows network stack objects, this often results in an application trying to use the internet crashing instead of just thinking its offline, as described in issues: #665 and #121
Currently it is possible to specify ports that can not be accessed by boxed applications, but its not possible to specify IP's or IP ranges, as requested in #96 it may be useful though to allow communication over the network of sandboxed processes with each other only. Also this limitation is not enforced on a kernel level and those can be bypassed.
And it may be useful to force the binding of newly created sockets to a given IP or NIC like requested in #893 and #237
Last but not least there may be a use case for network speed limiting #25
All this enhancements would mean the way sandboxie handles network restrictions need to be reworked, its required to add a kernel level packet filter that would allow to block some or all network communication by sandboxes applications on a packet level without blocking the entire network stack.
This would be a rather big rework but is something I plan to do in future.
If you have any feature requests related to sandboxies network aspects please post them in this issue if it is not already mentioned. Other issues on networking subjects will be closed on sight.