I used the script below and didn't encounter any CAPTCHAs:
from seleniumbase import SB
with SB(uc=True, ad_block_on=True) as sb:
url = "https://rateyourmusic.com/artist/pink-floyd/"
sb.driver.uc_open_with_reconnect(url, 8)Also, whenever you need to click in UC Mode, use sb.driver.uc_click(selector) to remain undetected.
(That'll work unless they already detected you in a previous step.)
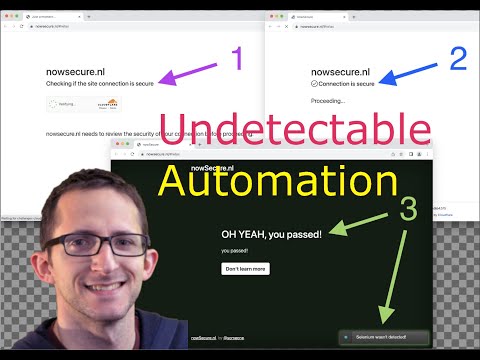
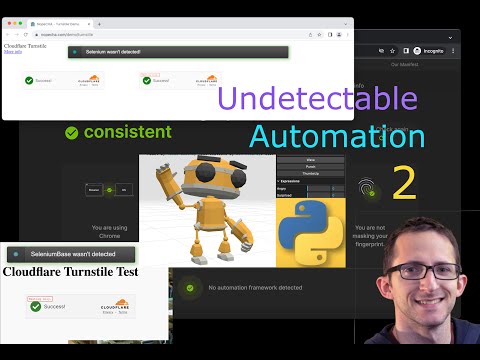
The following code works on a direct connection (no verification asked), however when using VPN (or an http proxy, NordVPN in my case) clicking on the verification box doesn't let the verification go through:
I have tried other libraries with undected capabilities through VPN, and while most didn't go through I was able to go past the verification box with https://github.com/kaliiiiiiiiii/Selenium-Driverless.
Anyone else experienced a similar behaviour?