## Task 2 - The Message
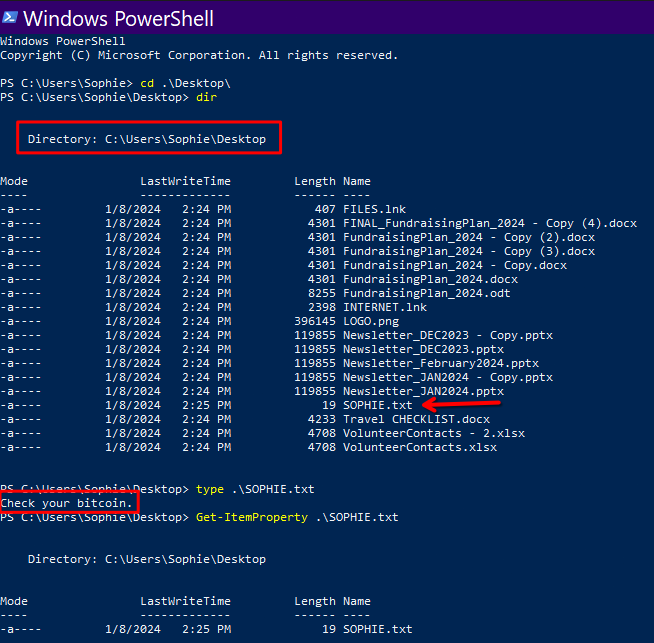
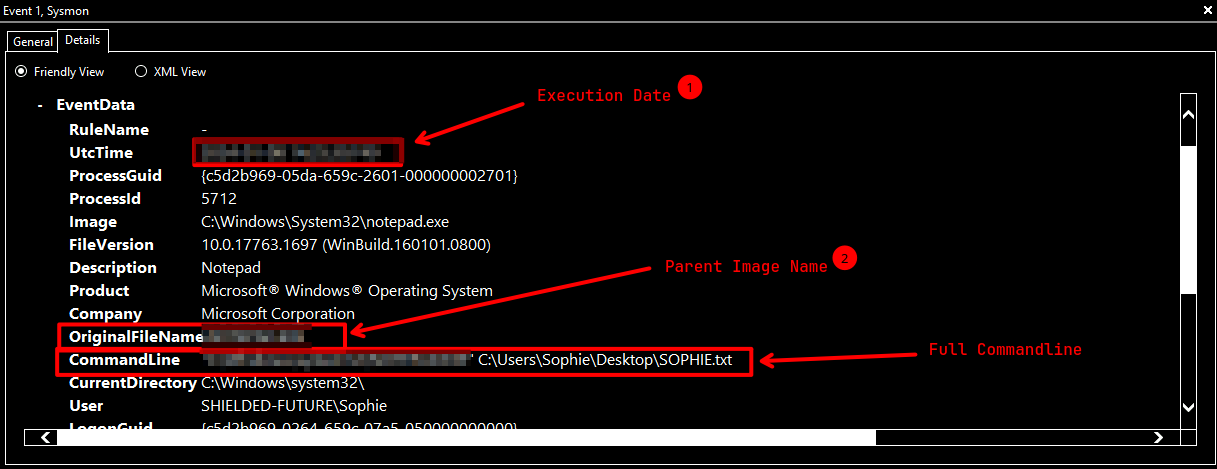
### What is the full path of the text file containing the "message"?
A: `C:\Users\Sophie\Desktop\SOPHIE.txt`
### What program was used to create the text file? What is the time of execution of the process that created the text file?
After waiting for `Event Viewer` to open for a while, you can go to `Application and Service Logs > Microsoft > Windows > Sysmon > Operational`.
After opening the logs, filter the logs with `Event ID ` `1` by clicking `Filter Current Log`.
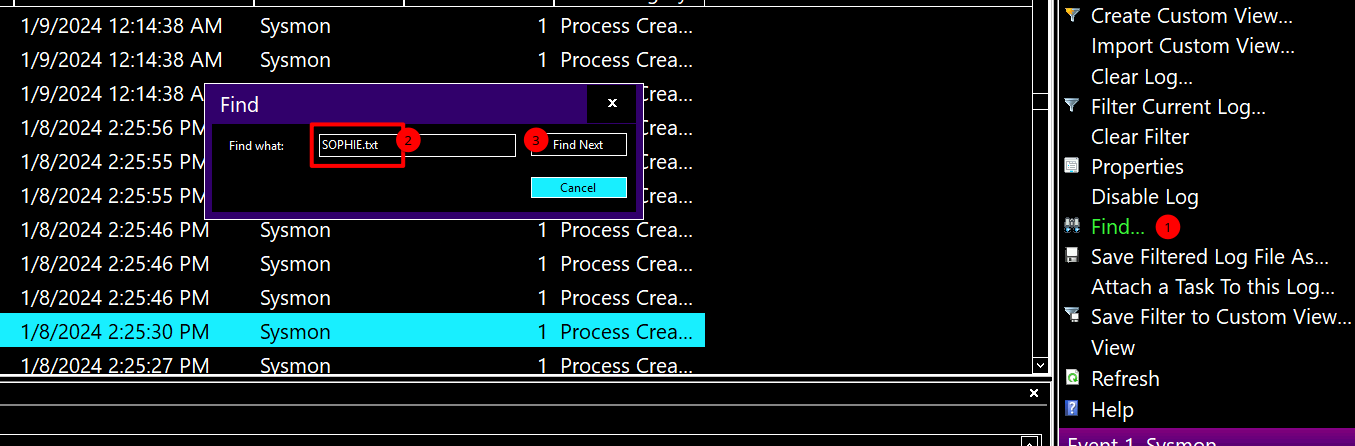
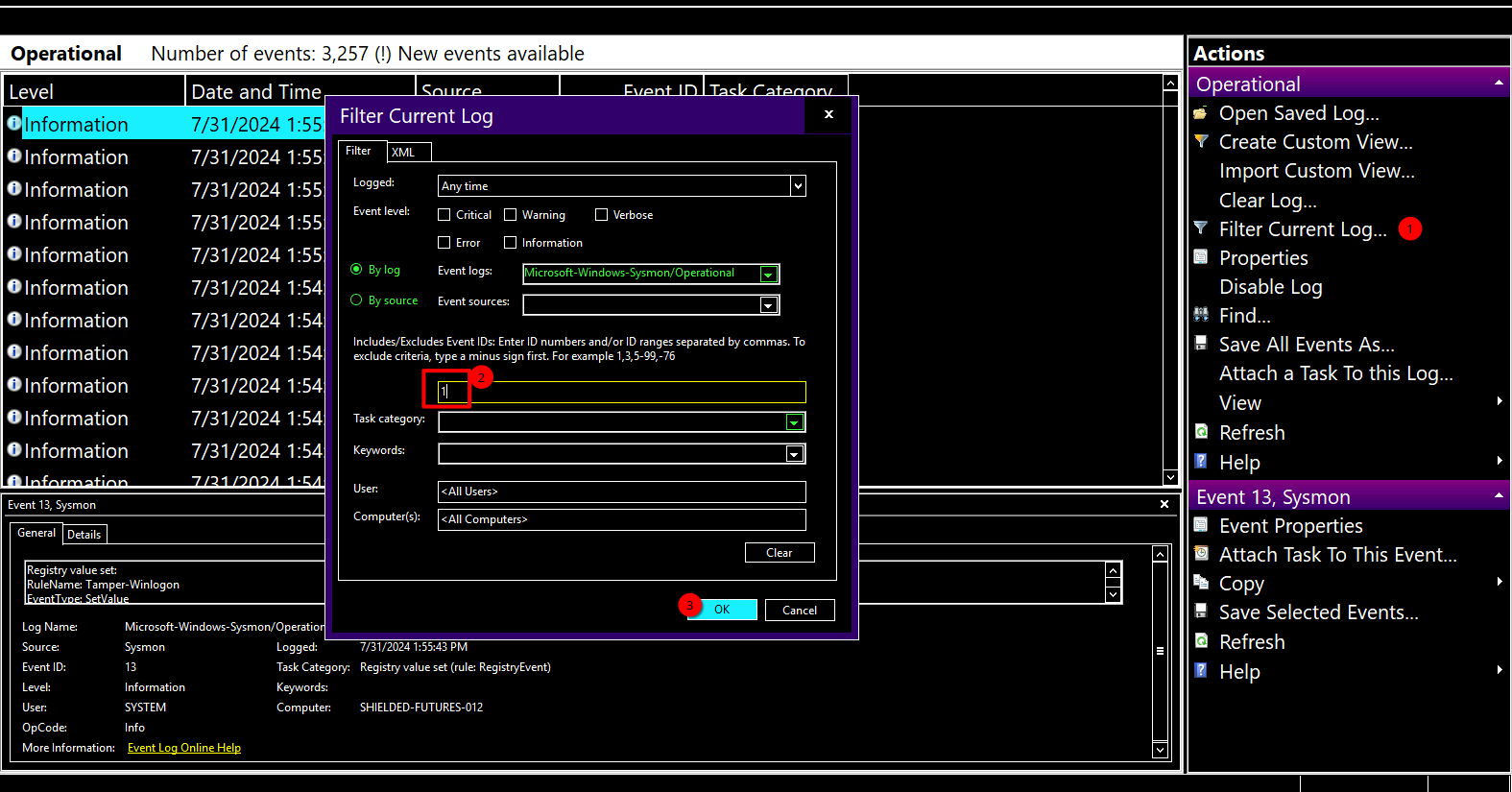After filtering the logs as `Event ID 1`, search for `SOPHIE.txt` by clicking `Find...`.
## Task 3 - Something Wrong
Clear the filter first by clicking `Clear Filter`
### What is the filename of this "installer"? (Including the file extension) What is the download location of this installer?
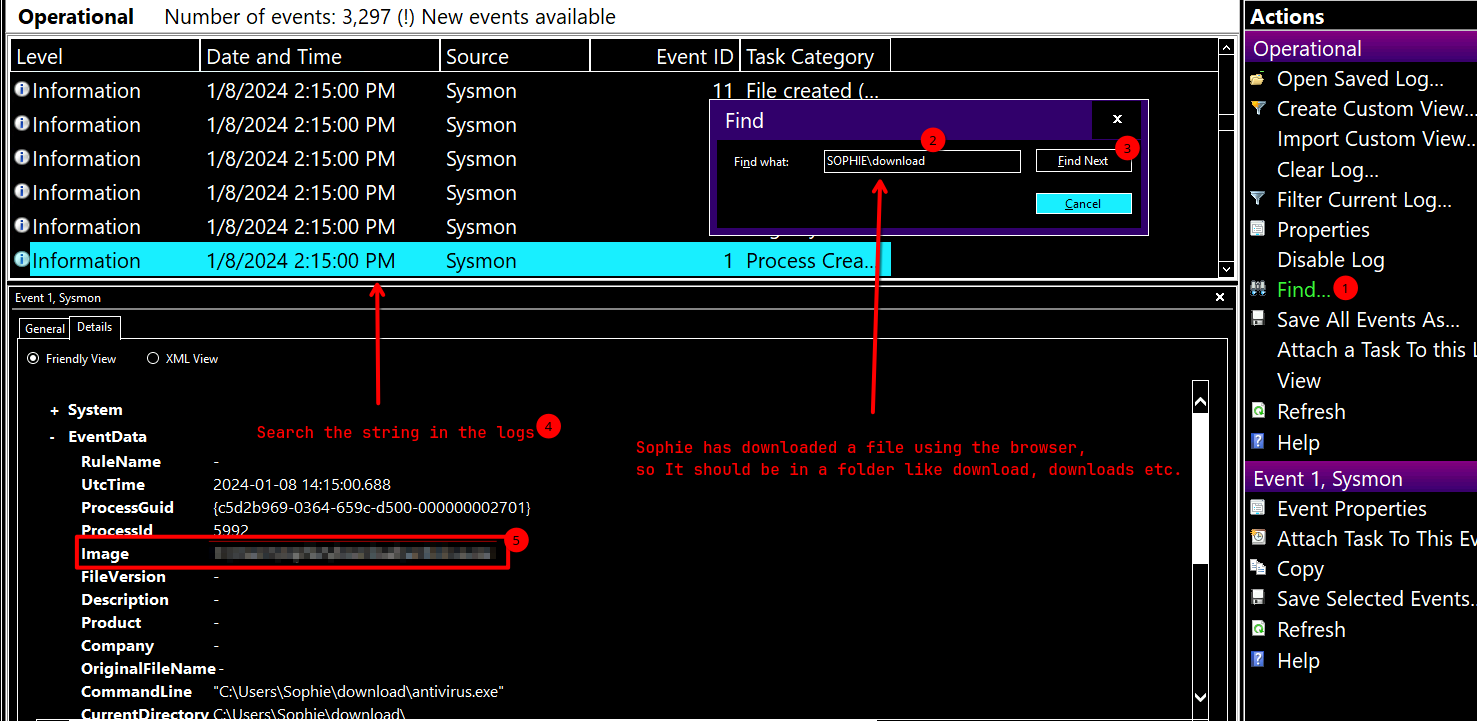
### The installer encrypts files and then adds a file extension to the end of the file name. What is this file extension?
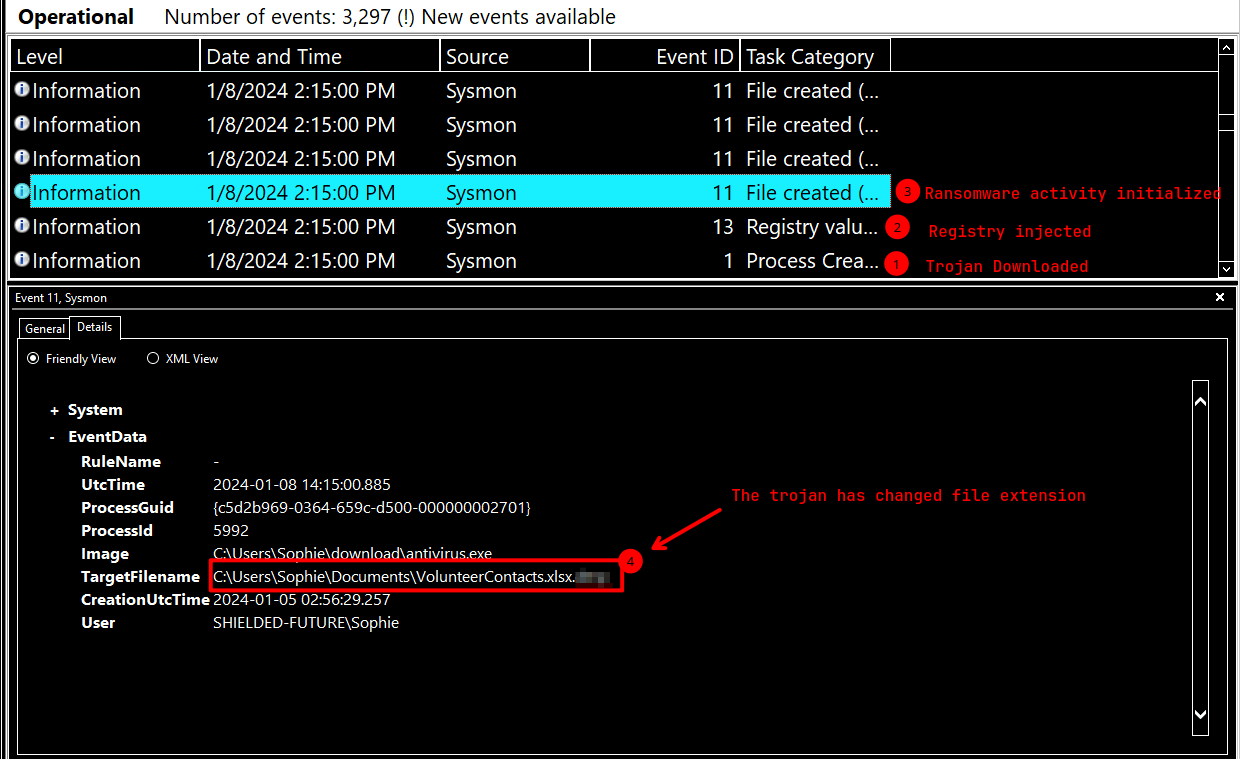
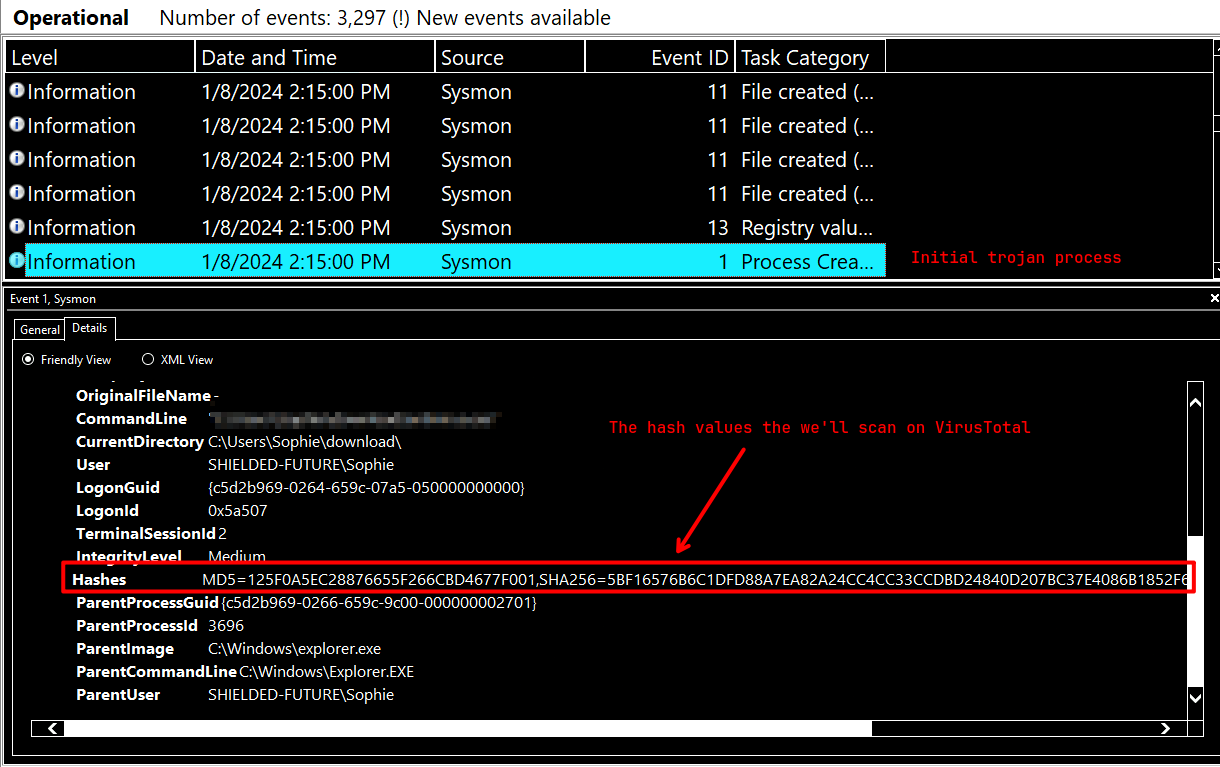
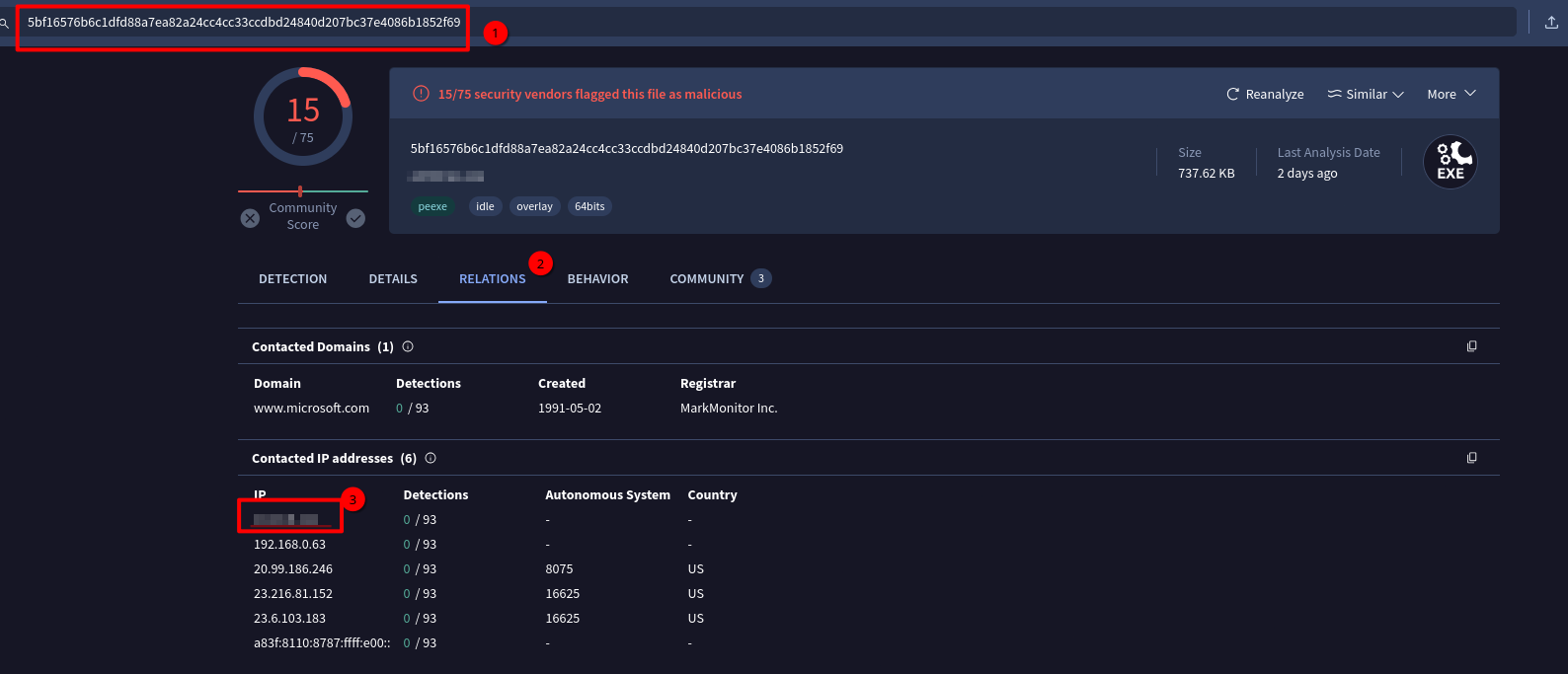
### The installer reached out to an IP. What is this IP?
## Task 4 - Back To Normal
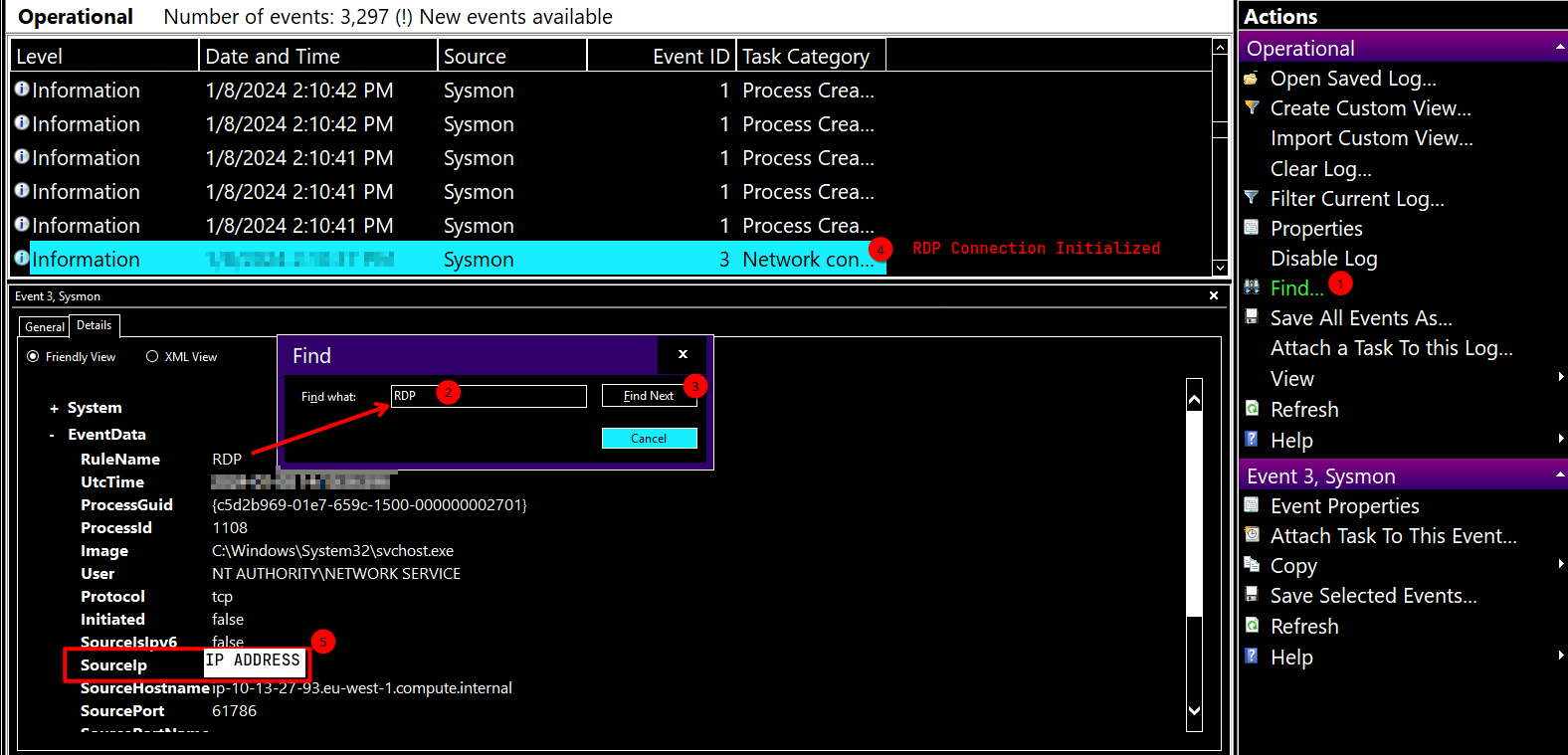
### The threat actor logged in via RDP right after the “installer” was downloaded. What is the source IP? This other person downloaded a file and ran it. When was this file run? Timezone UTC (Format YYYY-MM-DD hh:mm:ss)
## Task 5 - Doesn't Make Sense
## Arrange the following events in sequential order from 1 to 7, based on the timeline in which they occurred.
1. Sophie downloaded the malware and ran it.
2. The malware encrypted the files on the computer and showed a ransomware note.
3. Sophie ran out and reached out to you for help.
4. Someone else logged into Sophie's machine via RDP and started looking around.
5. The intruder downloaded a decryptor and decrypted all the files.
6. A note was created on the desktop telling Sophie to check her Bitcoin.
7. We arrive on the scene to investigate.
What program was used to create the text file? What is the time of execution of the process that created the text file?
After waiting for Event Viewer to open for a while, you can go to Application and Service Logs > Microsoft > Windows > Sysmon > Operational.
After opening the logs, filter the logs with Event ID1 by clicking Filter Current Log.
After filtering the logs as Event ID 1, search for SOPHIE.txt by clicking Find....
Task 3 - Something Wrong
Clear the filter first by clicking Clear Filter
What is the filename of this "installer"? (Including the file extension) What is the download location of this installer?
The installer encrypts files and then adds a file extension to the end of the file name. What is this file extension?
The installer reached out to an IP. What is this IP?
Task 4 - Back To Normal
The threat actor logged in via RDP right after the “installer” was downloaded. What is the source IP? This other person downloaded a file and ran it. When was this file run? Timezone UTC (Format YYYY-MM-DD hh:mm:ss)
Task 5 - Doesn't Make Sense
Arrange the following events in sequential order from 1 to 7, based on the timeline in which they occurred.
Sophie downloaded the malware and ran it.
The malware encrypted the files on the computer and showed a ransomware note.
Sophie ran out and reached out to you for help.
Someone else logged into Sophie's machine via RDP and started looking around.
The intruder downloaded a decryptor and decrypted all the files.
A note was created on the desktop telling Sophie to check her Bitcoin.
Medium
Markdown
TryHackMe Retracted
Task 2 - The Message
What is the full path of the text file containing the "message"?
A:
C:\Users\Sophie\Desktop\SOPHIE.txtWhat program was used to create the text file? What is the time of execution of the process that created the text file?
Event Viewerto open for a while, you can go toApplication and Service Logs > Microsoft > Windows > Sysmon > Operational.After opening the logs, filter the logs with
Event ID1by clickingFilter Current Log.Event ID 1, search forSOPHIE.txtby clickingFind....Task 3 - Something Wrong
Clear the filter first by clicking
Clear FilterWhat is the filename of this "installer"? (Including the file extension) What is the download location of this installer?
The installer encrypts files and then adds a file extension to the end of the file name. What is this file extension?
The installer reached out to an IP. What is this IP?
Task 4 - Back To Normal
The threat actor logged in via RDP right after the “installer” was downloaded. What is the source IP? This other person downloaded a file and ran it. When was this file run? Timezone UTC (Format YYYY-MM-DD hh:mm:ss)
Task 5 - Doesn't Make Sense
Arrange the following events in sequential order from 1 to 7, based on the timeline in which they occurred.