Hi, thanks for the issue. You can achieve this today using the generator https://github.com/slsa-framework/slsa-github-generator/blob/main/internal/builders/generic/README.md and setting the upload-asset: true. Can you confirm this works for your use case?
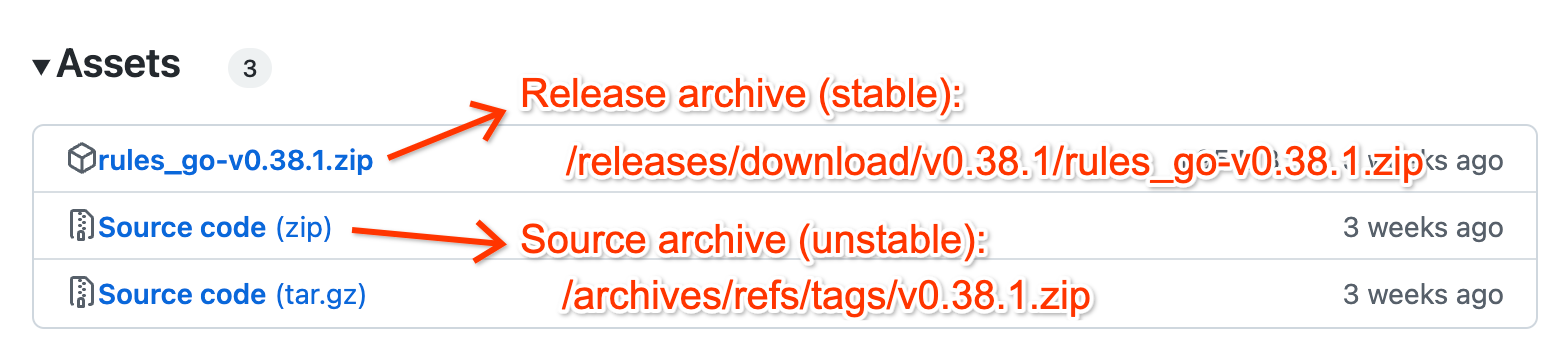
Is your feature request related to a problem? Please describe. Bazel recommends publishing source code archives as release assets – and Bazel Central Registry verifies stability by checking for
…/releases/download/…in GitHub URLs. Usinggh release downloadandgh release upload, GitHub Actions can automate this trivially, but OpenSSF punishes projects whose release assets lack signature and provenance.Describe the solution you'd like SLSA should provide a workflow for publishing source code archives as release assets with signature and provenance. Ideally, any project's
releaseworkflow could include a job specifying onlypermissionsanduseskeys and get.zip,.zip.intoto.jsonl,.tar.gzand.tar.gz.intoto.jsonlfiles attached to the release.Describe alternatives you've considered Letting N different projects implement this themselves in approximately N different ways. ;)
Additional context N/A