👋 Thanks for opening your first issue here! If you're reporting a 🐞 bug, please make sure you include steps to reproduce it. We get a lot of issues on this repo, so please be patient and we will get back to you as soon as we can.
Open gzbabhishek opened 3 years ago
👋 Thanks for opening your first issue here! If you're reporting a 🐞 bug, please make sure you include steps to reproduce it. We get a lot of issues on this repo, so please be patient and we will get back to you as soon as we can.
You'll need to install an openssl or openssl-devel package that will include the openssl.cnf file. Once that's there, SAML will be able to generate and read certificates for you.
Thanks, I did this configuration but the issue not resolved.
If you are on Windows Server 2019, trying pointing OPENSSL_CONF System Environment Variable to location of your openssl.cnf maybe? EDIT: sorry if this isn't useful, I realized you'll probably need to do something different if you're running as webapp, but if the issue is the system environment variable there's a possible way to set it here.
@gzbabhishek
How shall I get SAML idP Metadata to insert in the given box?
The pattern for the URL looks like this: https://login.microsoftonline.com/<tenant-id>/federationmetadata/2007-06/federationmetadata.xml?appid=<app-id>
You can find this URL in the Single-Sign-On settings of your enterprise app in the Azure portal.
Following a tutorial, I have enabled SAML on Azure AD which is connected and having a positive response.
while configuring to SAML I am getting error as shown in below image.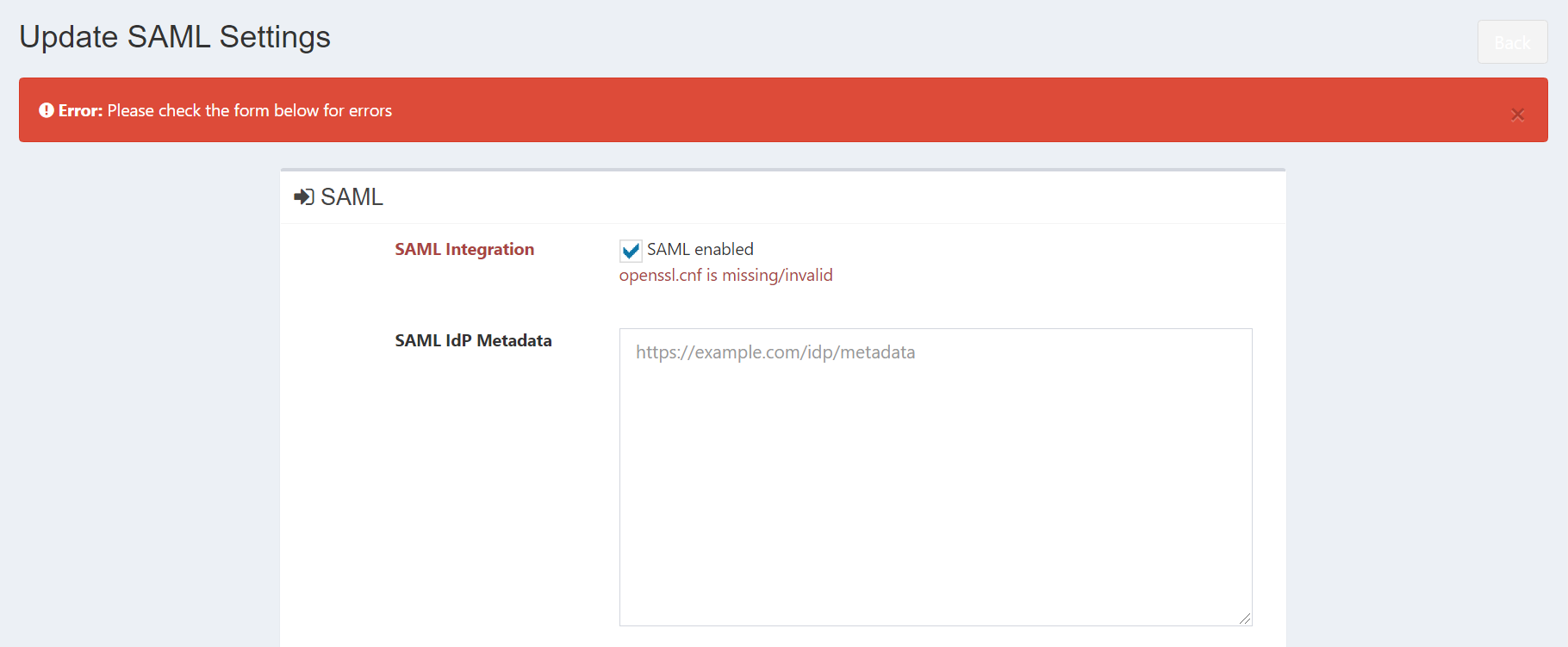
How shall I get SAML idP Metadata to insert in the given box?