One thing I feel is missing here is the ability to do this process manually. There should be a way to export the PoST proof from the node and then import a certificate. I think this could come in handy in some situations and should be easy to support. E.g. what you wrote in the end about requiring payment for certification. Also private PoETs could just manually sign their users' smesher ID and then users can import the signature into their node (with no "certification service") - for this, perhaps we should allow an empty certification service URL in info and only return a public key - users who don't already have a certificate for this key won't be able to use that PoET, so error messages should be clear.
Status quo
Currently, registration for a poet round requires proof of work. Its purpose is to guard poet from DOS in form of submitting many challenges by requiring certain amount of work to be done in order to register.
This is far from ideal for a few reasons:
Proposal
The proposal is to substitute the PoW with a certification that the miner spent significant resources to initialize its POST data. Every node that wishes to create an ATX must create an "initial POST proof" (a proof with an empty challenge). This initial proof should be verified by a trusted certifier service and the public key of the associated miner should be signed.
Every registration to the poet should carry the certificate to prove that the miner trying to register had properly initialized POST in the past. The certificate is eternal, it doesn't expire and doesn't need to be acquired again for future registrations - it can be persisted by the node.
The poet would specify an address and public key of the certifier service it trusts on /Info endpoint.
The following diagram presents the proposed flow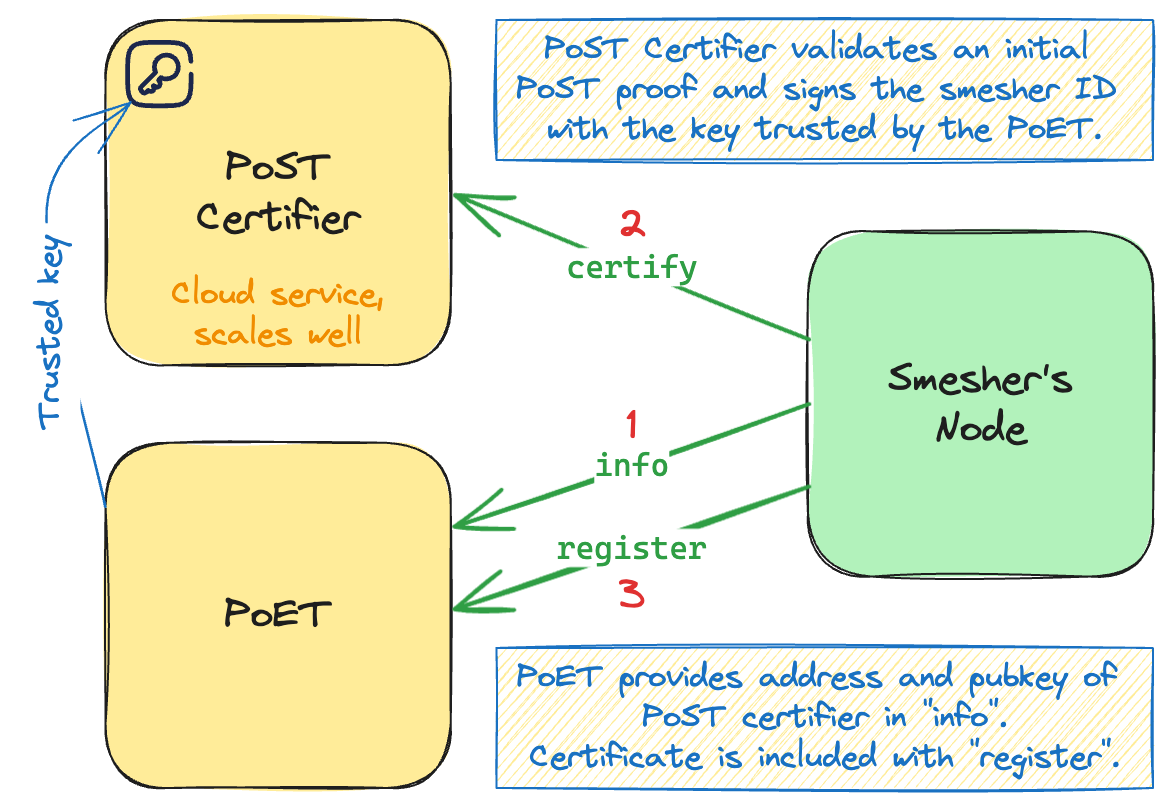
Considerations for private & community poets
There are a few ways that these poets can go about the proposed solution
We should probably provide a docker image for the certification service with clear step-by-step instructions for deployment on popular cloud(s).
Rotation of compromised certification services
We should be able to somehow change the trusted certification service in case it's compromised. The poet should return an unauthorized error code on
/Submitif an invalid certificate was used. The node would then know it must re-certify.Tasks
Opens
Custom certification services, paid poets :dollar:
A custom certification service could utilize any other heuristic to validate and sign the node's request. For example, it could require payment. The poet's side remains unchanged.