The problem was fixed after re-deploying keycloak's reverse proxy. I'm not sure, what caused the problem described above, but now it works now.
Closed MichaelSasser closed 2 years ago
The problem was fixed after re-deploying keycloak's reverse proxy. I'm not sure, what caused the problem described above, but now it works now.
Playbook Configuration:
My
vars.ymlfile looks like this:OIDC Relevant vars
`matrix_nginx_proxy_proxy_matrix_client_api_forwarded_location_synapse_oidc_api_enabled: true` In `matrix_synapse_configuration_extension_yaml`: ```yaml oidc_providers: - idp_id: keycloak idp_name: "Single Sign-On" issuer: "https://acme.foo.org/realms/bar" client_id: "synapse" client_secret: "secret" scopes: ["openid", "profile"] allow_existing_users: true user_mapping_provider: config: localpart_template: "{% raw %}{{ user.preferred_username }}{% endraw %}" display_name_template: "{% raw %}{{ user.name }}{% endraw %}" email_template: "{% raw %}{{ user.email }}{% endraw %}" ```
Full vars
```yaml matrix_domain: foo.org matrix_ssl_lets_encrypt_support_email: user@foo.org matrix_common_after_systemd_service_start_wait_for_timeout_seconds: 28 # Fix issue where the admin api is not reacheable anymore matrix_nginx_proxy_proxy_matrix_client_redirect_root_uri_to_domain: "" matrix_nginx_proxy_proxy_matrix_client_api_forwarded_location_synapse_admin_api_enabled: true # Setup matrix client for self-hosted jitsi matrix_client_element_integrations_jitsi_widget_url: "https://jitsi.{{ matrix_domain }}/api/widgets/jitsi.html" matrix_client_element_jitsi_preferredDomain: "jitsi.{{ matrix_domain }}" # set integration manager # workaround dimension matrix_client_element_integrations_ui_url: "https://scalar.vector.im/" matrix_client_element_integrations_rest_url: "https://scalar.vector.im/api" matrix_client_element_integrations_widgets_urls: ["https://scalar.vector.im/api"] # set server room directory matrix_client_element_roomdir_servers: - foo.org - matrix.org # Extra themes matrix_client_element_themes_enabled: false # Default Template matrix_client_element_default_theme: "dark" # Postgres matrix_postgres_connection_password: "foo" matrix_postgres_container_postgres_bind_port: 5432 matrix_postgres_process_extra_arguments: [ "-c max_connections=200", "-c shared_buffers=2GB", "-c effective_cache_size=6GB", "-c maintenance_work_mem=512MB", "-c checkpoint_completion_target=0.9", "-c wal_buffers=16MB", "-c default_statistics_target=100", "-c random_page_cost=1.1", "-c effective_io_concurrency=200", "-c work_mem=5242kB", "-c min_wal_size=1GB", "-c max_wal_size=4GB", "-c max_worker_processes=4", "-c max_parallel_workers_per_gather=2", "-c max_parallel_workers=4", "-c max_parallel_maintenance_workers=2", ] # Postgres Backups matrix_postgres_backup_enabled: true matrix_postgres_backup_keep_months: 12 # LDAP Synapse # # matrix_ma1sd_enabled: true matrix_synapse_ext_password_provider_rest_auth_enabled: true matrix_synapse_ext_password_provider_rest_auth_endpoint: "http://matrix-ma1sd:8090" matrix_synapse_password_config_localdb_enabled: false # disable the internal password auth matrix_ma1sd_configuration_extension_yaml: | ldap: enabled: true connection: host: foo tls: false port: 389 baseDNs: ['dc=foo,dc=org'] bindDn: 'foo' bindPassword: foo filter: '(memberOf=cn=matrix-users,cn=groups,dc=foo,dc=org)' attribute: uid: type: 'uid' value: 'uid' name: 'cn' threepid: email: - 'mail' msisdn: - 'mobile' # Federation matrix_synapse_federation_enabled: true matrix_synapse_allow_public_rooms_over_federation: true # Rooms without auth matrix_synapse_allow_public_rooms_without_auth: true # OpenID (Keycloak) (rest see below in matrix_synapse_configuration_extension_yaml) matrix_nginx_proxy_proxy_matrix_client_api_forwarded_location_synapse_oidc_api_enabled: true # Extra Synapse homeserver.yaml config matrix_synapse_configuration_extension_yaml: | redaction_retention_period: 30d retention: enabled: true default_policy: min_lifetime: 4w max_lifetime: 8w allowed_lifetime_min: 1d allowed_lifetime_max: 24w purge_jobs: - longest_max_lifetime: 3d interval: 12h - shortest_max_lifetime: 3d interval: 1d server_notices: system_mxid_localpart: server system_mxid_display_name: "Server Notices" system_mxid_avatar_url: "mxc://{{ matrix_domain }}/foo" room_name: "Server Notices" oidc_providers: - idp_id: keycloak idp_name: "Single Sign-On" issuer: "https://acme.foo.org/realms/foo" client_id: "synapse" client_secret: "foo" scopes: ["openid", "profile"] allow_existing_users: true user_mapping_provider: config: localpart_template: "{% raw %}{{ user.preferred_username }}{% endraw %}" display_name_template: "{% raw %}{{ user.given_name }}{% endraw %} {% raw %}{{ user.family_name }}{% endraw %}" email_template: "{% raw %}{{ user.email }}{% endraw %}" # Media retention matrix_synapse_media_retention_local_media_lifetime: 8w matrix_synapse_media_retention_remote_media_lifetime: 2w # Enable location sharing matrix_well_known_matrix_client_configuration_extension_json: |- { "jitsi": { "preferred_domain": "jitsi.foo.org" }, "org.matrix.msc3488.tile_server": { "map_style_url": "https://api.maptiler.com/maps/streets/style.json?key=foo" }, "m.tile_server": { "map_style_url": "https://api.maptiler.com/maps/streets/style.json?key=foo" }, "setting_defaults": { "MessageComposerInput.showStickersButton": false }, "features": { "feature_latex_maths": true, "feature_pinning": true, "feature_thread": true }, "admins": [{ "matrix_id": "@user:foo.org", "email_address": "info@foo.org", "role": "admin" }, { "email_address": "abuse@foo.org", "role": "security" }] } # workers matrix_synapse_workers_enabled: true matrix_synapse_workers_preset: one-of-each # default matrix_synapse_workers_presets: one-of-each: generic_workers_count: 4 pusher_workers_count: 1 appservice_workers_count: 1 federation_sender_workers_count: 4 media_repository_workers_count: 1 # Disabled until https://github.com/matrix-org/synapse/issues/8787 is resolved. user_dir_workers_count: 0 frontend_proxy_workers_count: 1 # LDAP Jitsi matrix_jitsi_auth_type: "ldap" matrix_jitsi_ldap_auth_method: "bind" matrix_jitsi_ldap_version: "3" matrix_jitsi_ldap_use_tls: false matrix_jitsi_ldap_url: "ldap://foo:389" matrix_jitsi_ldap_base: "dc=foo,dc=org" matrix_jitsi_ldap_binddn: "foo" matrix_jitsi_ldap_bindpw: "foo" matrix_jitsi_ldap_filter: "(&(uid=%u)(memberOf=cn=jitsi-users,cn=groups,dc=foo,dc=org))" # Jitsi matrix_jitsi_enabled: true matrix_jitsi_enable_auth: true matrix_jitsi_enable_guests: true matrix_jitsi_enable_lobby: true matrix_jitsi_enable_recording: false matrix_jitsi_enable_transcriptions: false # Run `bash inventory/scripts/jitsi-generate-passwords.sh` to generate these # passwords, or define your own strong passwords manually. matrix_jitsi_jicofo_component_secret: foo matrix_jitsi_jicofo_auth_password: foo matrix_jitsi_jvb_auth_password: foo matrix_jitsi_jibri_recorder_password: foo matrix_jitsi_jibri_xmpp_password: foo matrix_jitsi_web_config_resolution_width_ideal_and_max: 1920 matrix_jitsi_web_config_resolution_height_ideal_and_max: 1200 matrix_jitsi_web_config_resolution_width_min: 1280 matrix_jitsi_web_config_resolution_height_min: 720 matrix_jitsi_web_custom_config_extension: | config.enableLayerSuspension = true; config.disableAudioLevels = true; config.channelLastN = 4; config.disableSimulcast = true; # https://github.com/jitsi/docker-jitsi-meet/tree/master/web/rootfs/defaults #https://github.com/jitsi/docker-jitsi-meet/blob/c475d537e63b83bde603135a9dd26031e78bccb5/web/rootfs/defaults/interface_config.js matrix_jitsi_web_custom_interface_config_extension: | interfaceConfig.SHOW_JITSI_WATERMARK = false; interfaceConfig.SHOW_BRAND_WATERMARK = false; interfaceConfig.SHOW_WATERMARK_FOR_GUESTS = true; interfaceConfig.GENERATE_ROOMNAMES_ON_WELCOME_PAGE = true; interfaceConfig.DISABLE_TRANSCRIPTION_SUBTITLES = false; # Honoroit matrix_bot_honoroit_enabled: true matrix_bot_honoroit_database_engine: "postgres" matrix_bot_honoroit_database_password: "foo" matrix_bot_honoroit_password: "foo" matrix_bot_honoroit_login: foo matrix_bot_honoroit_roomid: "!foo:{{ matrix_domain }}" matrix_bot_honoroit_text_prefix_open: "[OPEN]" matrix_bot_honoroit_text_prefix_done: "[CLOSED]" matrix_bot_honoroit_text_greetings: "foo" matrix_bot_honoroit_text_error: "foo" matrix_bot_honoroit_text_emptyroom: "foo" matrix_bot_honoroit_text_done: "foo" # E-Mail matrix_mailer_sender_address: "service@foo.org" matrix_mailer_relay_use: true matrix_mailer_relay_host_name: "mail.foo.org" matrix_mailer_relay_host_port: 587 matrix_mailer_relay_auth: true matrix_mailer_relay_auth_username: "service@foo.org" matrix_mailer_relay_auth_password: "foo" matrix_coturn_turn_static_auth_secret: "foo" matrix_synapse_macaroon_secret_key: "foo" matrix_homeserver_generic_secret_key: "{{ matrix_synapse_macaroon_secret_key }}" matrix_synapse_max_upload_size_mb: 256 matrix_synapse_auto_join_rooms: - "#support:{{ matrix_domain }}" # Shared Secret Provider matrix_synapse_ext_password_provider_shared_secret_auth_enabled: true matrix_synapse_ext_password_provider_shared_secret_auth_shared_secret: "foo" # Base Domain Serving matrix_nginx_proxy_base_domain_serving_enabled: true # Maintenance # matrix_synapse_rust_synapse_compress_state_min_state_groups_required: 100000 # <- default matrix_synapse_rust_synapse_compress_state_find_rooms_command_wait_time: 1200 matrix_synapse_rust_synapse_compress_state_compress_room_time: 18000 # 2.5h -> 5h matrix_synapse_rust_synapse_compress_state_psql_import_time: 18000 # 2.5h -> 5h # Prometheus & Grafana matrix_prometheus_enabled: true matrix_prometheus_node_exporter_enabled: true matrix_prometheus_postgres_exporter_enabled: false matrix_prometheus_postgres_exporter_database_username: "matrix_prometheus_postgres_exporter" matrix_prometheus_postgres_exporter_database_password: "foo" matrix_grafana_enabled: true matrix_grafana_anonymous_access: false matrix_grafana_default_admin_user: user # Do not change, will not work matrix_grafana_default_admin_password: foo matrix_bot_mjolnir_enabled: true matrix_bot_mjolnir_access_token: "foo" matrix_bot_mjolnir_management_room: "!foo:foo.org" matrix_bot_mjolnir_configuration_extension_yaml: | recordIgnoredInvites: true commands: additionalPrefixes: - foo automaticallyRedactForReasons: - foo protections: wordlist: words: - foo minutesBeforeTrusting: 40 ```
Matrix Server:
Linux matrix 5.10.0-15-amd64 #1 SMP Debian 5.10.120-1 (2022-06-09) x86_64 GNU/LinuxAnsible: If your problem appears to be with Ansible, tell us:
Linux ms-thinkpad 5.18.5-arch1-1 #1 SMP PREEMPT_DYNAMIC Thu, 16 Jun 2022 20:40:45 +0000 x86_64 GNU/Linuxansible --version)Problem description:
I'm trying to get OpenId Connect (Keycloak) to work, so I can switch from LDAP to OIDC. But only get the following error after getting redirected from keycloak.
URI after redirect:
https://matrix.foo.org/_synapse/client/oidc/callback?state=foo&session_state=barScreenshot (Browser)
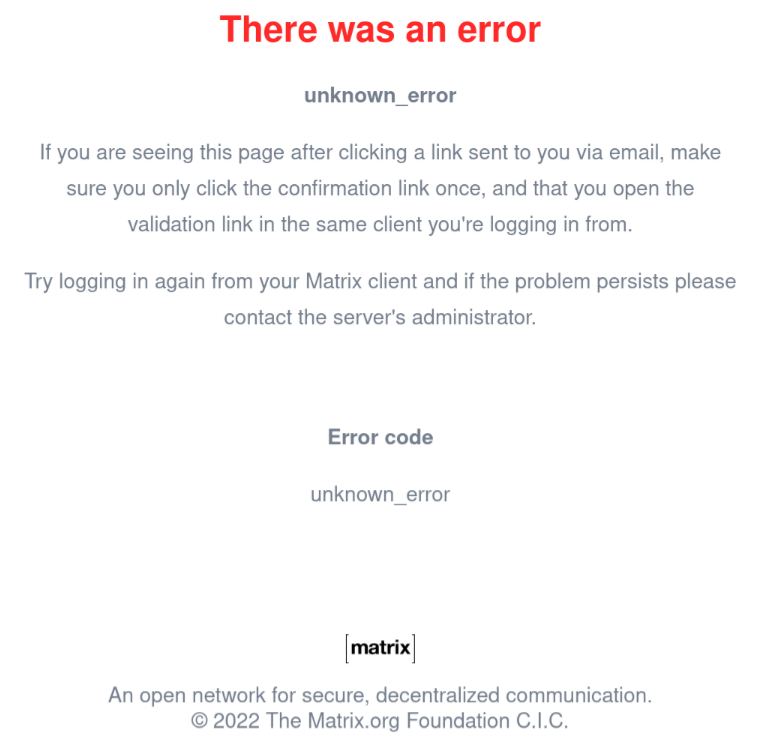
I'm not sure, maybe I missed something? I currently have the localdb (local password auth) and ma1sd (still) enabled. Might this have something to do with the problem?
Client (please complete the following information):
Linux ms-thinkpad 5.18.5-arch1-1 #1 SMP PREEMPT_DYNAMIC Thu, 16 Jun 2022 20:40:45 +0000 x86_64 GNU/LinuxAdditional context
Keycloak Client Config
(Keycloak 18.0.1) ```json { "clientId": "synapse", "surrogateAuthRequired": false, "enabled": true, "alwaysDisplayInConsole": false, "clientAuthenticatorType": "client-secret", "redirectUris": [ "https://matrix.foo.org/_synapse/client/oidc/callback" ], "webOrigins": [], "notBefore": 0, "bearerOnly": false, "consentRequired": false, "standardFlowEnabled": true, "implicitFlowEnabled": false, "directAccessGrantsEnabled": true, "serviceAccountsEnabled": false, "publicClient": false, "frontchannelLogout": false, "protocol": "openid-connect", "attributes": { "saml.force.post.binding": "false", "saml.multivalued.roles": "false", "frontchannel.logout.session.required": "false", "oauth2.device.authorization.grant.enabled": "false", "backchannel.logout.revoke.offline.tokens": "false", "saml.server.signature.keyinfo.ext": "false", "use.refresh.tokens": "true", "oidc.ciba.grant.enabled": "false", "backchannel.logout.session.required": "true", "client_credentials.use_refresh_token": "false", "require.pushed.authorization.requests": "false", "saml.client.signature": "false", "saml.allow.ecp.flow": "false", "id.token.as.detached.signature": "false", "saml.assertion.signature": "false", "client.secret.creation.time": "1655624809", "saml.encrypt": "false", "saml.server.signature": "false", "exclude.session.state.from.auth.response": "false", "saml.artifact.binding": "false", "saml_force_name_id_format": "false", "acr.loa.map": "{}", "tls.client.certificate.bound.access.tokens": "false", "saml.authnstatement": "false", "display.on.consent.screen": "false", "token.response.type.bearer.lower-case": "false", "saml.onetimeuse.condition": "false" }, "authenticationFlowBindingOverrides": {}, "fullScopeAllowed": true, "nodeReRegistrationTimeout": -1, "defaultClientScopes": [ "web-origins", "acr", "roles", "profile", "email" ], "optionalClientScopes": [ "address", "phone", "offline_access", "microprofile-jwt" ], "access": { "view": true, "configure": true, "manage": true } } ```
Relevant function in oidc.py