waiting for network to get connected...
asking server electrum.qtornado.com:50002:s for its peers
got 113 servers
contacting 109 servers
connected to 85 servers
85 answers
Results: attacker 25, honest 60
Attacker servers: [
'gregoire12.mldlab-works.space:50002:s',
'readonly.23734430190.pro:50002:s',
'wireless12.bitquantum.space:50002:s',
'superuser.23734430190.pro:50002:s',
'pacslinkip12.krypto-familar.fun:50002:s',
'topicres.imaginarycoin.info:50002:s',
'wlseuser12.bitcoinplug.website:50002:s',
'operatns.imaginarycoin.info:50002:s',
'superman.cryptoplayer.fun:50002:s',
'lucent01.23734430190.pro:50002:s',
'qtmhhttp12.mldlab-works.space:50002:s',
'plmimservice.bitcoinplug.website:50002:s',
'username.cryptoplayer.fun:50002:s',
'qlpinstall.krypto-familar.fun:50002:s',
'adminstat.imaginarycoin.info:50002:s',
'lessonuser2.cryptoplayer.fun:50002:s',
'utilities12.pebwindkraft.space:50002:s',
'openspirit.cryptoplayer.fun:50002:s',
'qautprof12.coinucopiaspace.xyz:50002:s',
'prodcics12.imaginarycoin.info:50002:s',
'vcoadmin.23734430190.pro:50002:s',
'siteminder.23734430190.pro:50002:s',
'videouser.bitcoinplug.website:50002:s',
'anonymous.bitcoinplug.website:50002:s',
'oraprobe.23734430190.pro:50002:s'
]





EDIT2: To users: when you broadcast a transaction, servers can tell you about errors with the transaction. In Electrum versions before 3.3.3, this error is arbitrary text, and what's worse, it is HTML/rich text (as that is the Qt default). So the server you are connected to can try to trick you by telling you to install malware (disguised as an update). You should update Electrum from the official website so that servers can no longer do this to you. If you see these messages/popups, just make sure you don't follow them and that you don't install what they tell you to install. The messages are just messages, they cannot hurt you by themselves.
TL;DR: There is an ongoing attack against users where servers raise exceptions when a client broadcasts a transaction; in this case the error text is displayed as is in the client GUI. The attacker has spawned lots of servers on different /16 IPv4s to increase his chances of being connected to. The error messages are trying to get the user to download and install malware (disguised as updated versions of electrum).
In relation to https://github.com/spesmilo/electrum/issues/4953, we were privately sent a screenshot that was apparently floating around a German chat room (on 2018-12-21).
There wasn't really any extra information given, however most likely the following happened:
https://github.com/spesmilo/electrum/blob/b491a30dd9f550ab2f335ae88889c910125d4559/electrum/network.py#L734-L741
To make the attack more effective, the attacker is creating lots of servers (sybils), hence increasing the chance a client would connect to him. See this graph on the number of servers hsmiths shared re the peers found by his server: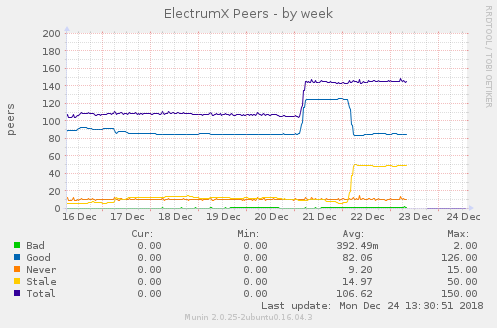
At the very least, the message should not be displayed as rich text. It is untrusted input afterall... We should also show some additional explanatory text at the beginning (prepend something).
For context, this mechanism of the server returning error message text to txn broadcasts is used to display error messages originating from bitcoind, such as low incremental fee or missing inputs, etc. Maybe the server should return error codes (ints) instead, and we could have our own decoding table, but then this would need to be kept in sync with bitcoind... (EDIT3: looked into this more, see https://github.com/spesmilo/electrum/issues/4968#issuecomment-455557296)
Hours after we were sent the screenshot, we silently made mitigations in https://github.com/spesmilo/electrum/commit/5248613e9d7b8b8ec85a1cee897d1901d747f5b4 and https://github.com/spesmilo/electrum/commit/5dc240d4ed39796bec72ac115d920160865b3ec5; and released 3.3.2. This is not a true fix, but the more proper fix of using error codes would entail upgrading the whole federated server ecosystem out there...
We did not publicly disclose this until now, as around the time of the 3.3.2 release, the attacker stopped; however they now started the attack again.
This is how the attack, live as writing this now, looks on 3.3.2:
This is on server
plmimservice.bitcoinplug.websiteon mainnet.My current server peers on bitcoin mainnet
``` Host Status TCP SSL Server Min Max Pruning Last Good Last Try Tries Source IP Address nl.bitops.me good 50001 50002 ElectrumX 1.8.12 1.2 1.4 01h 40m 07s 01h 40m 07s 0 peer 103.214.4.65 207.154.223.80 good 50001 50002 ElectrumX 1.2.1 0.9 1.2 01h 50m 14s 01h 50m 14s 0 peer 207.154.223.80 hsmiths4fyqlw5xw.onion good 50001 50002 ElectrumX 1.8.12 1.2 1.4 02h 17m 08s 02h 17m 14s 0 peer y4td57fxytoo5ki7.onion good 50001 50002 ElectrumX 1.8.12 1.2 1.4 02h 17m 18s 02h 17m 24s 0 peer 4cii7ryno5j3axe4.onion good 50001 ElectrumX 1.3.1 0.9 1.2 02h 17m 27s 02h 17m 29s 0 peer luggscoqbymhvnkp.onion good 80 ElectrumX 1.8.7 1.1 1.4 02h 17m 28s 02h 17m 32s 0 peer qtornadoklbgdyww.onion good 50001 50002 ElectrumX 1.8.12 1.2 1.4 02h 17m 57s 02h 18m 01s 0 peer ndndword5lpb7eex.onion good 50001 ElectrumX 1.8.12 1.2 1.4 02h 18m 09s 02h 18m 14s 0 peer electrum-server.ninja good 50001 50002 ElectrumX 1.8.12 1.2 1.4 02h 19m 31s 02h 19m 33s 0 peer 220.233.178.199 yuio.top good 50001 50002 ElectrumX 1.8.12 1.2 1.4 02h 19m 33s 02h 19m 35s 0 peer 118.86.185.36 139.162.14.142 good 50001 50002 ElectrumX 1.8.12 1.2 1.4 02h 19m 37s 02h 19m 38s 0 peer 139.162.14.142 electrumx.ddns.net good 50001 50002 ElectrumX 1.8.7 1.1 1.4 02h 19m 44s 02h 19m 45s 0 peer 169.0.147.67 electrum.hsmiths.com good 50001 50002 ElectrumX 1.8.12 1.2 1.4 02h 19m 50s 02h 19m 51s 0 peer 76.174.26.91 orannis.com good 50001 50002 ElectrumX 1.8.12 1.2 1.4 02h 19m 51s 02h 19m 52s 0 peer 50.35.67.146 enode.duckdns.org good 50001 50002 ElectrumX 1.8.12 1.2 1.4 02h 19m 52s 02h 19m 53s 0 peer 75.159.6.167 electrum.leblancnet.us good 50001 50002 ElectrumX 1.8.12 1.2 1.4 02h 19m 52s 02h 19m 53s 0 peer 205.197.210.32 dragon085.startdedicated.de good 50002 ElectrumX 1.8.12 1.2 1.4 02h 19m 54s 02h 19m 55s 0 peer 69.64.46.27 electrumx.bot.nu good 50001 50002 ElectrumX 1.8.12 1.2 1.4 02h 19m 56s 02h 19m 57s 0 peer 173.91.90.62 technetium.network good 50002 ElectrumX 1.8.7 1.1 1.4 02h 19m 57s 02h 19m 58s 0 peer 96.27.8.242 E-X.not.fyi good 50001 50002 ElectrumX 1.8.12 1.2 1.4 02h 19m 57s 02h 19m 58s 0 peer 170.130.28.174 us.electrum.be good 50001 50002 ElectrumX 1.8.7 1.1 1.4 02h 19m 58s 02h 19m 59s 0 peer 208.110.73.107 electrum.coinucopia.io good 50001 50002 ElectrumX 1.4.3 1.0 1.2 02h 20m 01s 02h 20m 01s 0 peer 67.205.187.44 elec.luggs.co good 443 ElectrumX 1.8.7 1.1 1.4 02h 20m 05s 02h 20m 06s 0 peer 95.211.185.14 electrum2.eff.ro good 50001 50002 ElectrumX 1.8.5 1.1 1.4 02h 20m 06s 02h 20m 06s 0 peer 195.135.194.3 AZZARITA.hopto.org good 50001 50002 ElectrumX 1.8.12 1.2 1.4 02h 20m 08s 02h 20m 08s 0 peer 2.236.8.149 electrumx.soon.it good 50001 50002 ElectrumX 1.8.11 1.2 1.4 02h 20m 08s 02h 20m 09s 0 peer 79.11.31.76 electrumx.ftp.sh good 50002 ElectrumX 1.8.12 1.2 1.4 02h 20m 09s 02h 20m 09s 0 peer 213.246.56.95 81-7-13-84.blue.kundencontroll good 50002 ElectrumX 1.8.12 1.2 1.4 02h 20m 09s 02h 20m 09s 0 peer 81.7.13.84 electrum.petrkr.net good 50001 50002 ElectrumX 1.4.3 1.0 1.2 02h 20m 09s 02h 20m 09s 0 peer 213.168.187.27 fedaykin.goip.de good 50001 50002 ElectrumX 1.8.12 1.2 1.4 02h 20m 09s 02h 20m 10s 0 peer 109.192.105.174 81-7-16-182.blue.kundencontrol good 50002 ElectrumX 1.8.12 1.2 1.4 02h 20m 10s 02h 20m 10s 0 peer 81.7.16.182 elx01.knas.systems good 50001 50002 ElectrumX 1.8.4 1.1 1.4 02h 20m 10s 02h 20m 10s 0 peer 83.233.65.59 bitcoin.grey.pw good 50001 50002 ElectrumX 1.8.7 1.1 1.4 02h 20m 10s 02h 20m 10s 0 peer 173.249.8.197 electrum.festivaldelhumor.org good 50001 50002 ElectrumX 1.8.12 1.2 1.4 02h 20m 10s 02h 20m 11s 0 peer 207.180.219.223 tardis.bauerj.eu good 50001 50002 ElectrumX 1.8.12 1.2 1.4 02h 20m 10s 02h 20m 11s 0 peer 51.15.138.64 electrum.anduck.net good 50001 50002 ElectrumX 1.8.12 1.2 1.4 02h 20m 11s 02h 20m 11s 0 peer 62.210.6.26 ndnd.selfhost.eu good 50001 50002 ElectrumX 1.8.12 1.2 1.4 02h 20m 11s 02h 20m 11s 0 peer 87.156.193.92 qmebr.spdns.org good 50001 50002 ElectrumX 1.8.12 1.2 1.4 02h 20m 11s 02h 20m 11s 0 peer 92.116.97.34 bitcoins.sk good 50001 50002 ElectrumX 1.8.12 1.2 1.4 02h 20m 11s 02h 20m 11s 0 peer 46.229.238.187 tomscryptos.com good 50001 50002 ElectrumX 1.8.12 1.2 1.4 02h 20m 11s 02h 20m 11s 0 peer 95.216.28.117 ulrichard.ch good 50001 50002 ElectrumX 1.8.12 1.2 1.4 02h 20m 11s 02h 20m 11s 0 peer 151.248.186.86 electrum.villocq.com good 50001 50002 ElectrumX 1.8.12 1.2 1.4 02h 20m 11s 02h 20m 12s 0 peer 78.143.214.223 b.ooze.cc good 50001 50002 ElectrumX 1.8.12 1.2 1.4 02h 20m 12s 02h 20m 12s 0 peer 145.239.252.207 vmd27610.contaboserver.net good 50002 ElectrumX 1.8.12 1.2 1.4 02h 20m 12s 02h 20m 12s 0 peer 173.249.48.200 electrum.nute.net good 50002 ElectrumX 1.3 0.9 1.2 02h 20m 12s 02h 20m 12s 0 peer 37.187.141.73 currentlane.lovebitco.in good 50001 50002 ElectrumX 1.8.7 1.1 1.4 02h 20m 12s 02h 20m 12s 0 peer 88.198.91.74 rbx.curalle.ovh good 50002 ElectrumX 1.8.12 1.2 1.4 02h 20m 12s 02h 20m 12s 0 peer 176.31.252.219 185.64.116.15 good 50001 50002 ElectrumX 1.8.9 1.1 1.4 02h 20m 12s 02h 20m 13s 0 peer 185.64.116.15 13.80.67.162 good 50001 50002 ElectrumX 1.4.3 1.0 1.2 02h 20m 12s 02h 20m 13s 0 peer 13.80.67.162 kirsche.emzy.de good 50001 50002 ElectrumX 1.8.12 1.2 1.4 02h 20m 13s 02h 20m 13s 0 peer 78.47.61.83 vmd30612.contaboserver.net good 50002 ElectrumX 1.8.12 1.2 1.4 02h 20m 13s 02h 20m 13s 0 peer 173.212.249.224 electrum.vom-stausee.de good 50001 50002 ElectrumX 1.3.1 0.9 1.2 02h 20m 13s 02h 20m 13s 0 peer 37.59.46.112 fn.48.org good 50003 50002 ElectrumX 1.8.7 1.1 1.4 02h 20m 13s 02h 20m 13s 0 peer 5.79.90.70 electrum.taborsky.cz good 50002 ElectrumX 1.8.12 1.2 1.4 02h 20m 13s 02h 20m 13s 0 peer 37.205.8.78 e-1.claudioboxx.com good 50001 50002 ElectrumX 1.8.12 1.2 1.4 02h 20m 13s 02h 20m 13s 0 peer 37.61.209.146 e-2.claudioboxx.com good 50001 50002 ElectrumX 1.8.12 1.2 1.4 02h 20m 14s 02h 20m 14s 0 peer 37.61.209.147 btc.cihar.com good 50001 50002 ElectrumX 1.8.7 1.1 1.4 02h 20m 14s 02h 20m 14s 0 peer 78.46.177.74 dedi.jochen-hoenicke.de good 50001 50002 ElectrumX 1.8.12 1.2 1.4 02h 20m 14s 02h 20m 14s 0 peer 88.198.39.205 hetzner01.fischl-online.de good 50002 ElectrumX 1.8.12 1.2 1.4 02h 20m 14s 02h 20m 14s 0 peer 5.9.124.124 electrum.be good 50001 50002 ElectrumX 1.8.7 1.1 1.4 02h 20m 14s 02h 20m 14s 0 peer 88.198.241.196 electrum.qtornado.com good 50001 50002 ElectrumX 1.8.12 1.2 1.4 02h 20m 15s 02h 20m 15s 0 peer 88.99.162.199 bitcoin.corgi.party good 50001 50002 ElectrumX 1.8.12 1.2 1.4 02h 30m 09s 02h 30m 09s 0 peer 176.223.139.65 mooo.not.fyi good 50011 50012 ElectrumX 1.8.12 1.2 1.4 02h 38m 52s 02h 38m 53s 0 peer 71.239.40.8 2AZZARITA.hopto.org good 50001 50002 ElectrumX 1.8.12 1.2 1.4 03h 07m 03s 03h 07m 03s 0 peer 173.212.253.26 tpslocalserver12.cryptoplayer. good 50001 50002 ElectrumX 1.8.12 1.2 1.4 04h 28m 07s 04h 28m 09s 0 peer 128.199.223.21 62.80.227.49 good 50001 50002 ElectrumX 1.8.12 1.2 1.4 04h 30m 12s 04h 30m 12s 0 peer 62.80.227.49 ozahtqwp25chjdjd.onion good 50001 50002 ElectrumX 1.8.12 1.2 1.4 04h 46m 27s 04h 46m 34s 0 peer sysdump112.bitcoinplug.website good 50001 50002 ElectrumX 1.8.12 1.2 1.4 04h 49m 49s 04h 49m 50s 0 peer 128.199.223.23 prodcics12.imaginarycoin.info good 50001 50002 ElectrumX 1.8.12 1.2 1.4 04h 50m 00s 04h 50m 02s 0 peer 128.199.223.22 sysadmin12.23734430190.pro good 50001 50002 ElectrumX 1.8.12 1.2 1.4 04h 50m 04s 04h 50m 05s 0 peer 128.199.225.8 computer12.krypto-familar.fun good 50001 50002 ElectrumX 1.8.12 1.2 1.4 04h 50m 23s 04h 50m 25s 0 peer 128.199.225.13 gregoire12.mldlab-works.space good 50001 50002 ElectrumX 1.8.12 1.2 1.4 04h 50m 54s 04h 50m 55s 0 peer 128.199.218.24 quaternion.tech good 50001 50002 ElectrumX 1.8.12 1.2 1.4 04h 58m 38s 04h 58m 39s 0 peer 104.244.222.239 btc.smsys.me good 995 ElectrumX 1.8.12 1.2 1.4 04h 59m 50s 04h 59m 52s 0 peer 50.198.167.205 helicarrier.bauerj.eu good 50001 50002 ElectrumX 1.8.7 1.1 1.4 05h 00m 12s 05h 00m 12s 0 peer 178.32.88.133 bfav33xnleliriow.onion good 50001 50002 ElectrumX 1.8.12 1.2 1.4 05h 26m 47s 05h 26m 52s 0 peer 128.199.223.10 good 50001 50002 ElectrumX 1.8.12 1.2 1.4 05h 43m 10s 05h 43m 11s 0 peer 128.199.223.10 utilities12.pebwindkraft.space good 50001 50002 ElectrumX 1.8.12 1.2 1.4 05h 48m 13s 05h 48m 14s 0 peer 52.221.249.16 security12.cryptoplayer.fun good 50001 50002 ElectrumX 1.8.12 1.2 1.4 06h 04m 33s 06h 04m 36s 0 peer 13.229.97.230 museadmin12.imaginarycoin.info good 50001 50002 ElectrumX 1.8.12 1.2 1.4 06h 04m 55s 06h 04m 56s 0 peer 3.0.98.224 qtmhhttp12.mldlab-works.space good 50001 50002 ElectrumX 1.8.12 1.2 1.4 06h 05m 17s 06h 05m 19s 0 peer 13.229.197.132 qautprof12.coinucopiaspace.xyz good 50001 50002 ElectrumX 1.8.12 1.2 1.4 06h 05m 38s 06h 05m 39s 0 peer 54.255.206.0 politcally12.23734430190.pro good 50001 50002 ElectrumX 1.8.12 1.2 1.4 06h 07m 29s 06h 07m 30s 0 peer 13.229.130.59 wlseuser12.bitcoinplug.website good 50001 50002 ElectrumX 1.8.12 1.2 1.4 06h 08m 07s 06h 08m 08s 0 peer 18.136.203.167 pacslinkip12.krypto-familar.fu good 50001 50002 ElectrumX 1.8.12 1.2 1.4 06h 08m 10s 06h 08m 11s 0 peer 3.0.139.42 wireless12.bitquantum.space good 50001 50002 ElectrumX 1.8.12 1.2 1.4 06h 08m 18s 06h 08m 19s 0 peer 13.229.224.194 walle.dedyn.io good 50002 ElectrumX 1.8.12 1.2 1.4 06h 25m 12s 06h 25m 12s 0 peer 79.148.156.226 daedalus.bauerj.eu good 50001 50002 ElectrumX 1.8.12 1.2 1.4 06h 45m 56s 06h 45m 56s 0 peer 5.230.24.38 db2admin1.krypto-familar.fun good 50001 50002 ElectrumX 1.8.12 1.2 1.4 06h 49m 42s 06h 49m 44s 0 peer 172.104.57.12 oraprobe.23734430190.pro good 50001 50002 ElectrumX 1.8.12 1.2 1.4 06h 54m 09s 06h 54m 11s 0 peer 45.76.70.111 videouser.bitcoinplug.website good 50001 50002 ElectrumX 1.8.12 1.2 1.4 06h 54m 44s 06h 54m 47s 0 peer 108.61.218.93 vcoadmin.23734430190.pro good 50001 50002 ElectrumX 1.8.12 1.2 1.4 06h 54m 46s 06h 54m 49s 0 peer 66.42.103.16 openspirit.cryptoplayer.fun good 50001 50002 ElectrumX 1.8.12 1.2 1.4 06h 55m 31s 06h 55m 32s 0 peer 45.77.241.145 security1.bitcoinplug.website good 50001 50002 ElectrumX 1.8.12 1.2 1.4 06h 55m 43s 06h 55m 45s 0 peer 103.3.63.9 anonymous.bitcoinplug.website good 50001 50002 ElectrumX 1.8.12 1.2 1.4 06h 55m 47s 06h 55m 49s 0 peer 66.42.104.125 adminstat.imaginarycoin.info good 50001 50002 ElectrumX 1.8.12 1.2 1.4 06h 55m 48s 06h 55m 50s 0 peer 45.32.101.251 siteminder.23734430190.pro good 50001 50002 ElectrumX 1.8.12 1.2 1.4 06h 56m 11s 06h 56m 14s 0 peer 45.76.70.99 operatns.imaginarycoin.info good 50001 50002 ElectrumX 1.8.12 1.2 1.4 06h 56m 26s 06h 56m 27s 0 peer 207.148.75.252 username.cryptoplayer.fun good 50001 50002 ElectrumX 1.8.12 1.2 1.4 06h 56m 26s 06h 56m 27s 0 peer 45.77.242.185 lessonuser2.cryptoplayer.fun good 50001 50002 ElectrumX 1.8.12 1.2 1.4 06h 56m 32s 06h 56m 33s 0 peer 139.180.132.139 adminstat1.bitquantum.space good 50001 50002 ElectrumX 1.8.12 1.2 1.4 06h 57m 11s 06h 57m 12s 0 peer 172.104.164.217 btc.xskyx.net good 50001 50002 ElectrumX 1.8.7 1.1 1.4 08h 01m 13s 08h 01m 13s 0 peer 185.183.158.170 oaihub902.imaginarycoin.info good 50001 50002 ElectrumX 1.8.12 1.2 1.4 09h 04m 39s 09h 04m 40s 0 peer 54.169.204.38 username.bitcoinplug.website good 50001 50002 ElectrumX 1.8.12 1.2 1.4 09h 05m 08s 09h 05m 09s 0 peer 13.229.98.142 topicres.imaginarycoin.info good 50001 50002 ElectrumX 1.8.12 1.2 1.4 09h 05m 14s 09h 05m 15s 0 peer 13.250.37.215 scientific.23734430190.pro good 50001 50002 ElectrumX 1.8.12 1.2 1.4 09h 05m 29s 09h 05m 30s 0 peer 54.169.192.215 security.cryptoplayer.fun good 50001 50002 ElectrumX 1.8.12 1.2 1.4 09h 05m 32s 09h 05m 33s 0 peer 3.0.59.204 plmimservice.bitcoinplug.websi good 50001 50002 ElectrumX 1.8.12 1.2 1.4 09h 05m 41s 09h 05m 42s 0 peer 18.136.102.143 readonly.23734430190.pro good 50001 50002 ElectrumX 1.8.12 1.2 1.4 09h 05m 58s 09h 06m 00s 0 peer 54.255.195.58 qlpinstall.krypto-familar.fun good 50001 50002 ElectrumX 1.8.12 1.2 1.4 09h 06m 04s 09h 06m 06s 0 peer 3.0.19.36 superman.cryptoplayer.fun good 50001 50002 ElectrumX 1.8.12 1.2 1.4 09h 06m 15s 09h 06m 16s 0 peer 54.169.53.21 lucent01.23734430190.pro good 50001 50002 ElectrumX 1.8.12 1.2 1.4 09h 08m 00s 09h 08m 01s 0 peer 52.74.115.7 erbium1.sytes.net good 50001 50002 ElectrumX 1.8.12 1.2 1.4 09h 58m 02s 09h 58m 03s 0 peer 46.246.49.225 superuser.23734430190.pro good 50001 50002 ElectrumX 1.8.12 1.2 1.4 12h 00m 33s 12h 00m 34s 0 peer 54.254.191.195 VPS.hsmiths.com good 50001 50002 ElectrumX 1.8.12 1.2 1.4 12h 14m 29s 12h 14m 31s 0 peer 51.15.77.78 electrum2.villocq.com good 50001 50002 ElectrumX 1.8.5 1.1 1.4 12h 30m 08s 12h 30m 09s 0 peer 88.81.143.198 electrumx.schmoock.net good 50001 50002 ElectrumX 1.8.12 1.2 1.4 17h 44m 18s 17h 44m 18s 0 peer 46.4.92.21 e.keff.org good 50001 50002 ElectrumX 1.8.12 1.2 1.4 19h 07m 57s 19h 07m 57s 0 peer 194.71.109.91 electrum3.everynothing.net good 50001 50002 ElectrumX 1.8.12 1.2 1.4 20h 59m 59s 21h 00m 00s 0 peer 198.23.152.179 electrumx.strangled.net good 50002 ElectrumX 1.8.12 1.2 1.4 22h 49m 55s 22h 49m 57s 0 peer 69.30.215.42 62.210.170.57 good 50002 ElectrumX 1.8.12 1.2 1.4 23h 02m 38s 23h 02m 38s 0 peer 62.210.170.57 s7clinmo4cazmhul.onion good 50001 ElectrumX 1.8.12 1.2 1.4 23h 21m 28s 23h 21m 35s 0 peer bitcoin-server.cf good 50002 ElectrumX 1.8.12 1.2 1.4 23h 21m 46s 23h 21m 47s 0 peer 185.181.61.140 n3o2hpi5xnf3o356.onion stale 50001 50002 ElectrumX 1.3 0.9 1.2 1d 02h 02m 01h 02m 30s 4 peer electrum.coineuskal.com stale 50001 50002 ElectrumX 1.3 0.9 1.2 1d 02h 09m 01h 09m 57s 4 peer 34.207.56.59 54.179.187.114 stale 50001 50002 ElectrumX 1.8.12 1.2 1.4 1d 02h 25m 34s 5 peer 54.179.187.114 bauerjhejlv6di7s.onion stale 50001 50002 ElectrumX 1.8.7 1.1 1.4 1d 04h 47m 04h 55m 27s 1 peer 54.251.183.105 stale 50001 50002 ElectrumX 1.8.12 1.2 1.4 1d 09h 28m 04h 22m 43s 6 peer 54.251.183.105 159.65.137.67 stale 50001 50002 ElectrumX 1.8.12 1.2 1.4 1d 09h 41m 04h 41m 22s 6 peer 159.65.137.67 128.199.206.38 stale 50001 50002 ElectrumX 1.8.12 1.2 1.4 2d 01h 41m 04h 34m 48s 8 peer 128.199.206.38 81-7-10-251.blue.kundencontrol stale 50002 ElectrumX 1.8.12 1.2 1.4 3d 12h 00m 17h 40m 09s 9 peer 81.7.10.251 electrum.mindspot.org stale 50002 ElectrumX 1.8.12 1.2 1.4 4d 01h 39m 1d 07h 19m 9 peer 172.103.153.90 84.197.110.145 stale 50001 50002 ElectrumX 1.8.12 1.2 1.4 4d 12h 58m 1d 18h 38m 9 peer 84.197.110.145 node.ispol.sk stale 50001 50002 ElectrumX 1.3+ 0.9 1.2 10d 00h 40m 9d 00h 49m 1 peer 193.58.196.212 3smoooajg7qqac2y.onion stale 50001 50002 ElectrumX 1.8.12 1.2 1.4 15d 23h 39m 14d 22h 59m 3 peer such.ninja never 50001 50002 ElectrumX 1.2 0.9 1.1 Never 07m 51s 2 163.172.61.154 163.172.61.154 ip120.ip-54-37-91.eu never 50001 50002 ElectrumX 1.2.1 0.9 1.1 Never 08m 38s 1 54.37.91.120 54.37.91.120 electrum.dk never 50001 50002 ElectrumX 1.2 0.9 1.1 Never 13d 09h 00m 3 92.246.24.225 92.246.24.225 13.250.108.34 never 50001 50002 ElectrumX 1.8.12 1.2 1.4 Never 10d 03h 50m 2 13.250.108.34 13.250.108.34 ip119.ip-54-37-91.eu never 50001 50002 ElectrumX 1.2.1 0.9 1.1 Never 15m 04s 2 54.37.91.119 54.37.91.119 165.227.22.180 never 50001 50002 ElectrumX 1.2 0.9 1.1 Never 09m 46s 1 165.227.22.180 165.227.22.180 104.250.141.242 never 50002 ElectrumX 1.2 0.9 1.1 Never 16m 52s 2 104.250.141.242 104.250.141.242 ip239.ip-54-36-234.eu never 50001 50002 ElectrumX 1.2.1 0.9 1.1 Never 17m 24s 2 54.36.234.239 54.36.234.239 ip101.ip-54-37-91.eu never 50001 50002 ElectrumX 1.2.1 0.9 1.1 Never 05m 10s 2 54.37.91.101 54.37.91.101 xray587.startdedicated.de bad 50002 ElectrumX 1.8.12 1.2 1.4 42m 00s 42m 01s 0 peer 188.138.88.42 electrumx.ga bad 50002 ElectrumX 1.8.12 1.2 1.4 01h 20m 11s 01h 20m 11s 0 peer 178.32.223.22 7jwtirwsaogb6jv2.onion bad 50001 50002 ElectrumX 1.3+ 0.9 1.2 10d 00h 39m 9d 00h 34m 2 peer ```Notice there are 7
*.bitcoinplug.websitedomains. There are 6*.imaginarycoin.infodomains. There are 9*.23734430190.prodomains. There are 7*.cryptoplayer.fundomains. There are 4*.krypto-familar.fundomains.(EDIT1: noticed at 2018-12-27 14:48 UTC that these domains are no longer DNS resolving)
@ecdsa @ysangkok
EDIT4: For longer term resolution of this issue, see https://github.com/spesmilo/electrum/issues/4968#issuecomment-455557296 and https://github.com/spesmilo/electrum/pull/5011