Thanks for reporting this, @Andreas-PPI!
It looks as though the change in 63607ee213c74d84ef52167ac08a2f67eb0b2f89 changed the way attribute values are searched/returned and subsequently mapped, resulting in the possible NPE. Would you be interested in submitting a PR to fix the issue?
I believe the authorityMapper would need to be changed to return null in this case, and the for-loop below would skip null return values.

Describe the bug I want to evaluate the LDAP entries of a user to derive the role of the user. The attribute I have chosen is 'description' of the groups the user is a member of. The corresponding configuration in the security.xml is as follows:
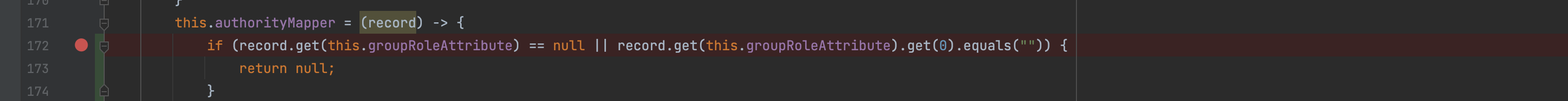
If 'description' is not assigned for one of the entries, a NullPointerException occurs in the class DefaultLdapAuthoritiesPopulator. I think this happens in line 172:
String role = record.get(this.groupRoleAttribute).get(0);In this caserecord.get(this.groupRoleAttribute)returns null.I'm using spring-security-ldap:5.7.3 - the newest version which works with Java 8. Previously I used V3.1.1, no NullPointerException was thrown there. Instead such entries were skipped, which I think is the better behavior.
To Reproduce Add a group without description to your LDAP-groups or remove description from existing group.
Expected behavior Unspecified attribute values should be treated as empty strings. Alternatively, the affected entries can be omitted so that DefaultLdapAuthoritiesPopulator.getGrantedAuthorities() returns fewer entries than are present in the LDAP.
Stack trace