It does indeed look quite weird crash dump. What would you get if you set a break point onto nt!RtlpGetStackLimitsEx+0x14acc5 (ie, int 29h) and reproduce the issue?
Open nerded1337 opened 4 years ago
It does indeed look quite weird crash dump. What would you get if you set a break point onto nt!RtlpGetStackLimitsEx+0x14acc5 (ie, int 29h) and reproduce the issue?
Context:
- I am manually mapping a kernel driver based on SimpleSvmHook (nearly no modification except adding stuff in entry point).
Please don't use this for P2C 💀 💀
If you are manually mapping it, you need to start your hypervisor from a system thread, as your hypervisor will be mapped from Kdmapper context, with kdmapper cr3. As soon as kdmapper exits, that cr3 base won't exist for nested page table translations anymore.
You should also load the driver normally rather than manual map if you are trying to get better testing results.
Context:
- I am manually mapping a kernel driver based on SimpleSvmHook (nearly no modification except adding stuff in entry point).
Please don't use this for P2C 💀 💀
If you are manually mapping it, you need to start your hypervisor from a system thread, as your hypervisor will be mapped from Kdmapper context, with kdmapper cr3. As soon as kdmapper exits, that cr3 base won't exist for nested page table translations anymore.
You should also load the driver normally rather than manual map if you are trying to get better testing results.
I am not using this for a P2C :P. I am not using kdmapper and I already tried loading the driver normally for testing purposes. It's more like I wanted to learn stuff, and haven't done any further investigations to fix this issue. Thanks for the reply tho :)
I'm also getting random crashes like this it's driving me insane
Hi, I am experiencing something similar to #2.
Context:
Below is the Windbg summary of the memory dump you can download by clicking this link
In my case, the memory dump doesn't give the full stack trace. But I managed to have some insight:
following the stack here is what I extracted
nt!RtlpGetStackLimitsEx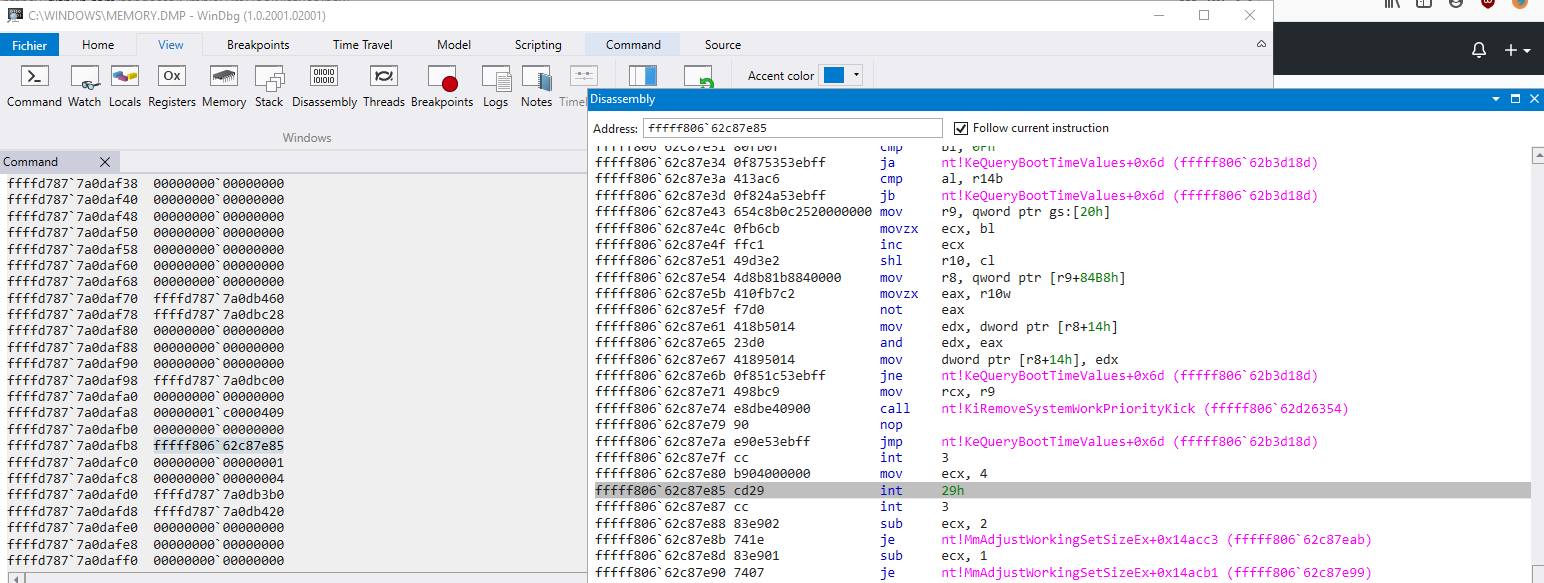
nt!nt!MiSetNonPagedPoolNoSteal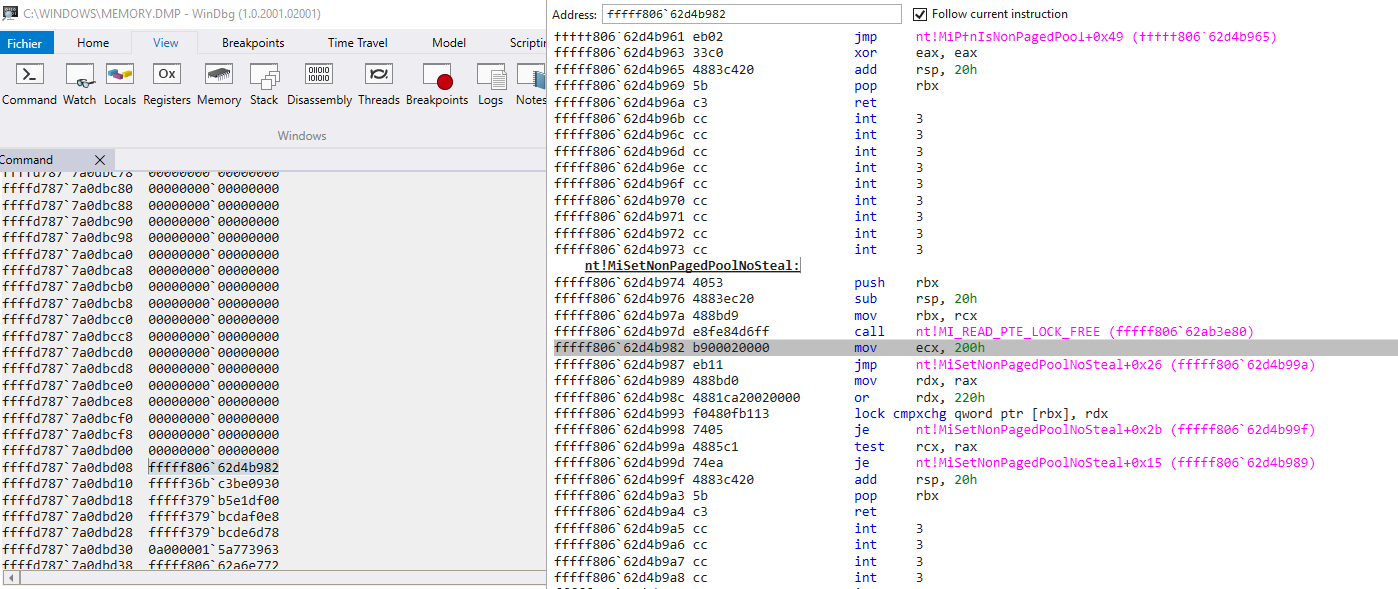
??????????? wtf is MiQueuePinDriverAddressLong also? patchguard???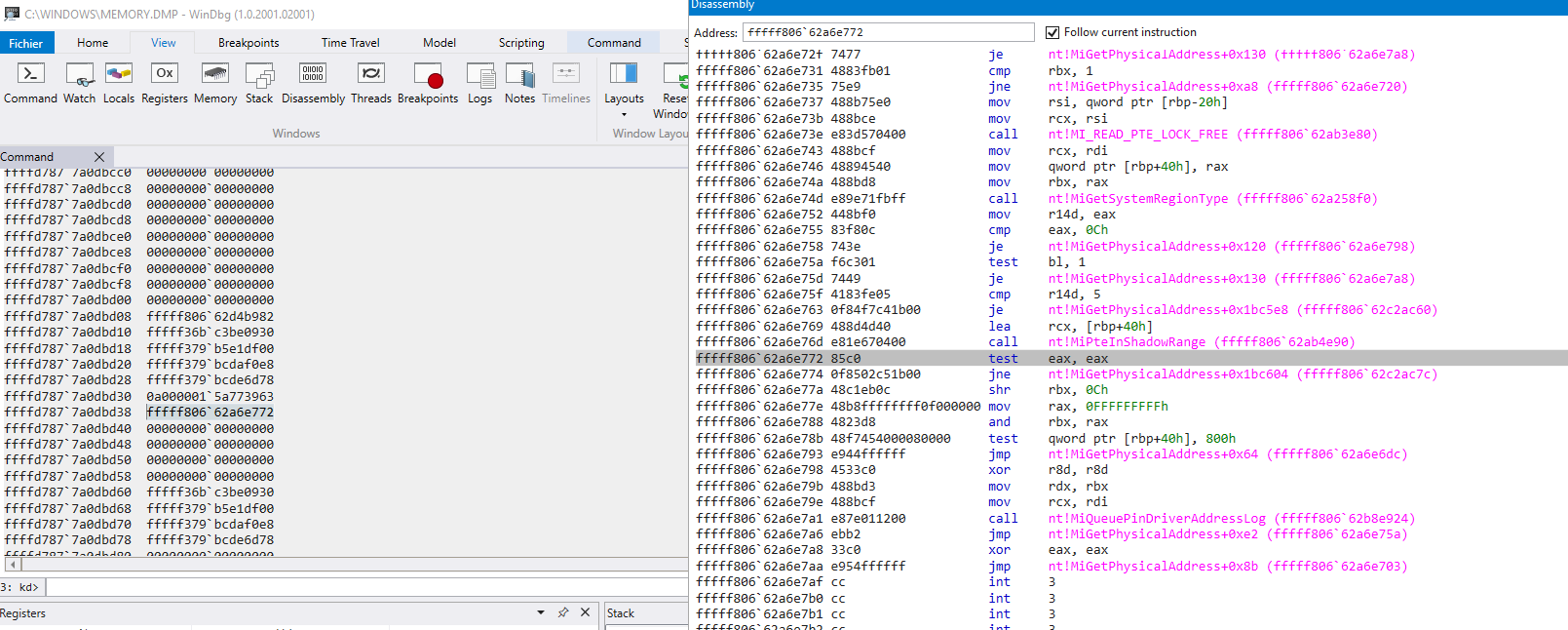
nt!MmGetPhysicalAddress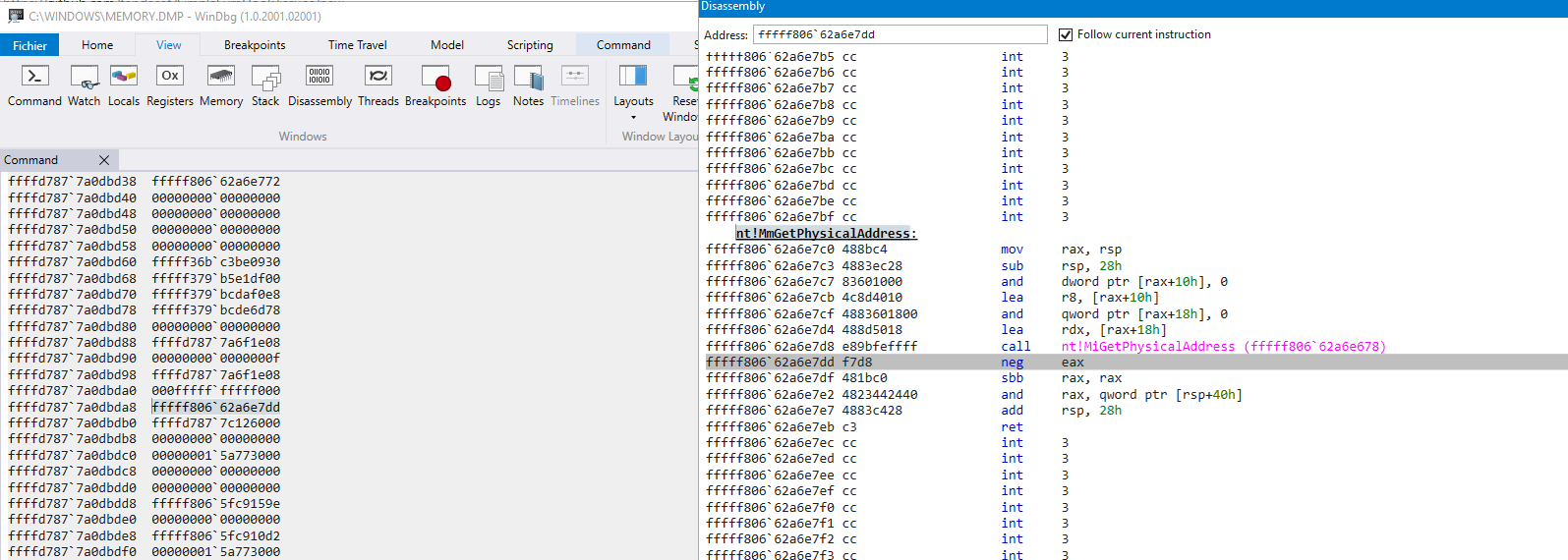
SimpleSvmHook!BuildNestedPageTableEntry
I really have no idea of what's going on and why this is happening from time to time.