Issue: Account enumeration attacks
Since Customer's emailAddress is constrained to be unique, and we allow the customer to change their emailAddress, this opens the door to an enumeration attack. Consider:
- Attacker creates an account with the email address "hacker@leet.net"
- Attacker goes to own account page and attempts to update own account with new address "joe.smith@gmail.com"
- If a customer with the email "joe.smith@gmail.com" already exists, we cannot allow this change as it would violate the unique constraint. We return an error of some kind.
- Now the attacker knows that Joe Smith has an account with us.
- Attacker repeats this process (likely in an automated fashion directly against the GraphQL API) to build up a list of all of our registered users' email addresses.
The same process could also be taken against the "create account" endpoint, but would be a little less efficient since it would create a lot of new accounts for non-matching email addresses.
Severity
In the case outlined above, the disclosure of the existing email address is necessary and unavoidable. However, is it so bad?
Many well-known sites also allow such enumeration: https://markitzeroday.com/enumeration/privacy/2017/06/20/to-be-enumerated-or-not-to-be.html
This answer basically says it is a non-issue: https://security.stackexchange.com/a/42874
I tend to think it is of low severity since email addresses are public information in general.
Mitigation
The most practical mitigation I can think of would be some kind of throttling on the frequency that a given Customer may attempt to change their emailAddress.
A Customer can be a guest (has no associated User) or registered (has an associated User).
Account creation
An account can be created in one of two ways:
As the diagram shows, a customer does not need to create an account after placing an order. Indeed, the customer is free to only every do guest checkouts. For the checkout, however, the email address would be used to create a guest Customer, and then on subsequent checkouts with the same email address, the same guest Customer would be assumed.
At any time, the guest Customer can be converted into an authenticated Customer by registering in either of the two ways outlined above.
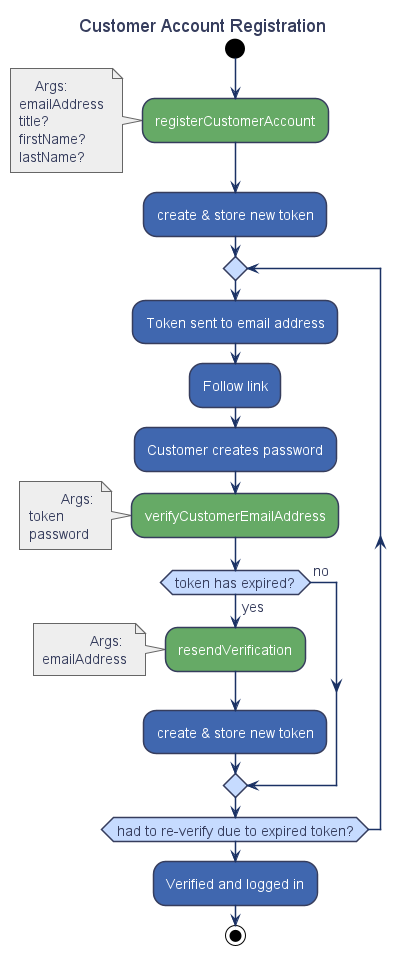
Registration process
There are 2 questions to resolve regarding registration:
Account Deletion (GDPR)
A user should have the ability to delete their account, as should an administrator. In this case, we want to keep the physical row in the DB for the purposes of data consistency and reporting, but we should completely remove any personally identifiable information (PII):