It is problem not only for SSD. I got the same problem with 2.5'' SSD and HDD with hardware RAID0. Very low IOPS... 3-10 times less depending on hardware. Common symptom: writing is less affected than reading.
Due to this issue CPU speed does not make a lot of sense to estimate how fast disk encryption will be. So it would be very good if somebody can help to at least understand the reason.
UPDATE
I had to switch my storage system to DiskCryptor solution due to this issue.
It has approximately the same speed as unencrypted volume.
Hardware HDD RAID0 with on-board RAM cache gives me 10 times more read IOPS and +170 MB/s for linear read speed. Single SSD setup has 8 times more IOPS and + 90 MB/s for linear read.
So I can say it is 98% of "raw" speed.
The only drawback of DiskCryptor for me is no audits.
But I cannot accept so dramatic speed regression even if VeraCrypt is successor of TC and it was audited.
I read some opinions that TC was also slow on fast SSD disks. So I afraid it is some architecture problem initially created in TC.


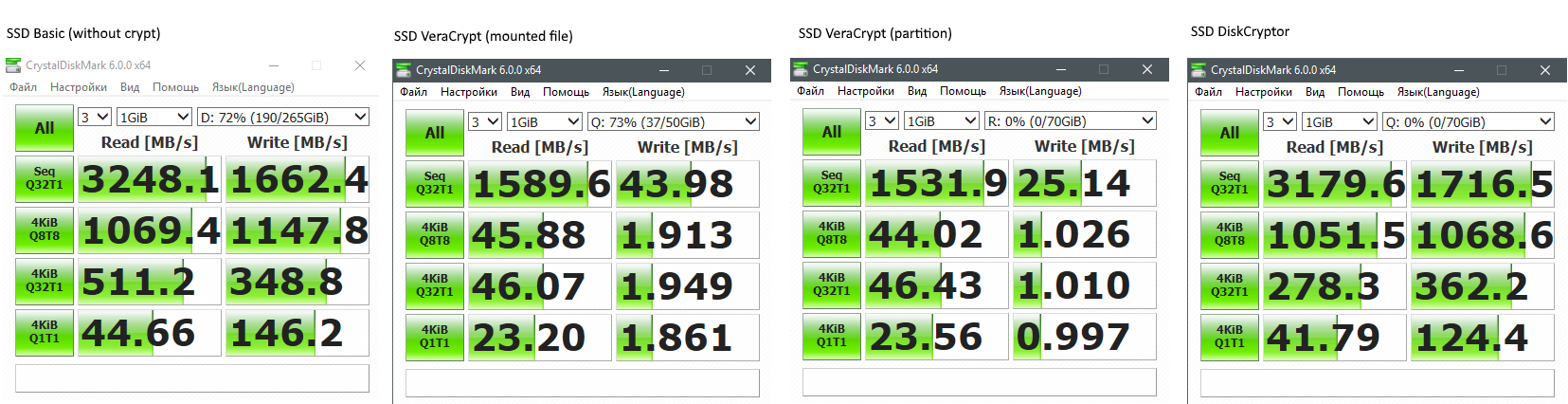 As you can see, the performance is practically not degraded by DiskCryptor, but on VeraCrypt the performance drops in many times.
As you can see, the performance is practically not degraded by DiskCryptor, but on VeraCrypt the performance drops in many times. The degradation in performance on single HDD is not noticeable.
The degradation in performance on single HDD is not noticeable.



Hi,
Please don't take that as a complain, I only wish to help improve the software so I can use it.
I achieve very bad performance on Windows 10 LTSB 2016 with a Samsung EVO 960 250Gb and Veracrypt AES encryption:
Before :
After :
My hardware :
I7 7700k @ stock 16Gb Corsair DDR4 Samsung 960 Evo 250Gb with up to date Samsung NVME driver Windows 10 LTSB 2016 up to date Veracrypt 1.19 64 bits
Veracrypt Benchmark :
How can I manage to get close performance to non encrypted drive ? Is this even possible ?
Thanks and best regards, Nicolas