I think this is a test case exhibiting the problem:
- Do a nop draw to a surface at address
X. For my test I used a 128x128x4 surface format. - Do a CPU blit starting before the surface and extending over half the texture, address
Y=X - 128*64*4 - Set the surface to some other memory to be used as a standard framebuffer, set
Yas a texture, and render a quad.
Since the CPU blit to Y covered the entirety of the memory being used as a texture, you should just see whatever was blitted.
HW results:
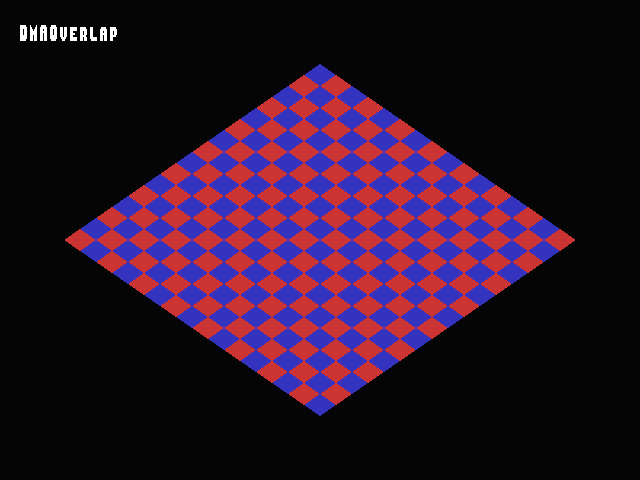
xemu:
Bug Description
This issue has been observed with Burnout 3, but due to its nature, the issue more than likely affects other titles too.
pgraph_surface_access_callback, corrupting the buffer used by the IDE DMA transfer.Notes Shortly after the kernel loads the default.xbe into memory; the game will attempt to load into memory one of its packed resources that overlap with a previous surface buffer.
The IDE DMA transfer can be monitored and traced at the kernel
IdexDiskReadWriteof the disk driver object.On success, the buffer at 0x03C1C000 should equal
00 00 3C 54 ..., and the game should boot normally. Note, attempting to read the buffer from gdb will still triggerpgraph_surface_access_callback.Example of corrupt buffer and normal buffer:
Expected Behavior
Surface loading/unloading should work in a manner that does not conflict with other hw functions, such as DMA.
xemu Version
0.7.96-4-g18cee9c2e3
System Information
No response
Additional Context
BIOS: m8plus
760a6817566a79cca2d2d733bead29f0bf8347bb