The following rights configuration worked for me as workaround instead of checking the box "Prevent unregistered users from viewing pages, regardless of the page rights":
Make XWikiAll group allowed to view any web-page (this is not checked by default).

Make XWikiGuest prohibited to do any action (you need to click several times on the checkbox to bring prohibition):
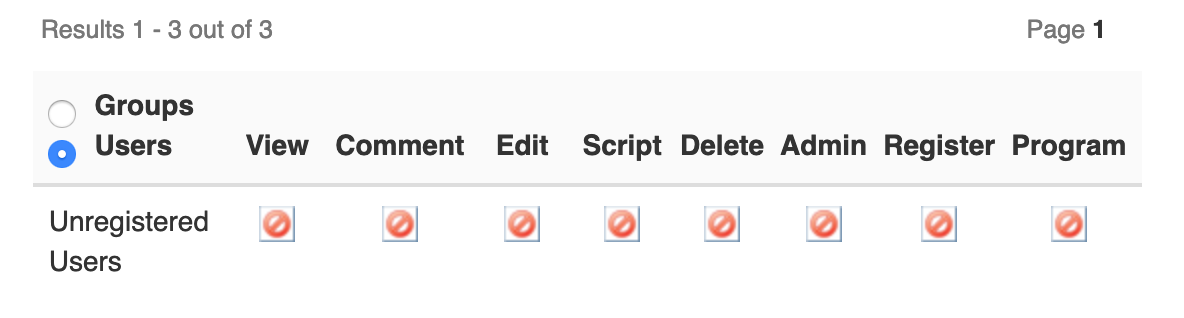
This made my anonymous access to any page that I could try be redirected to the login, the login buttons of XWiki and Google be displayed, and the login function with an identification on Google to work.

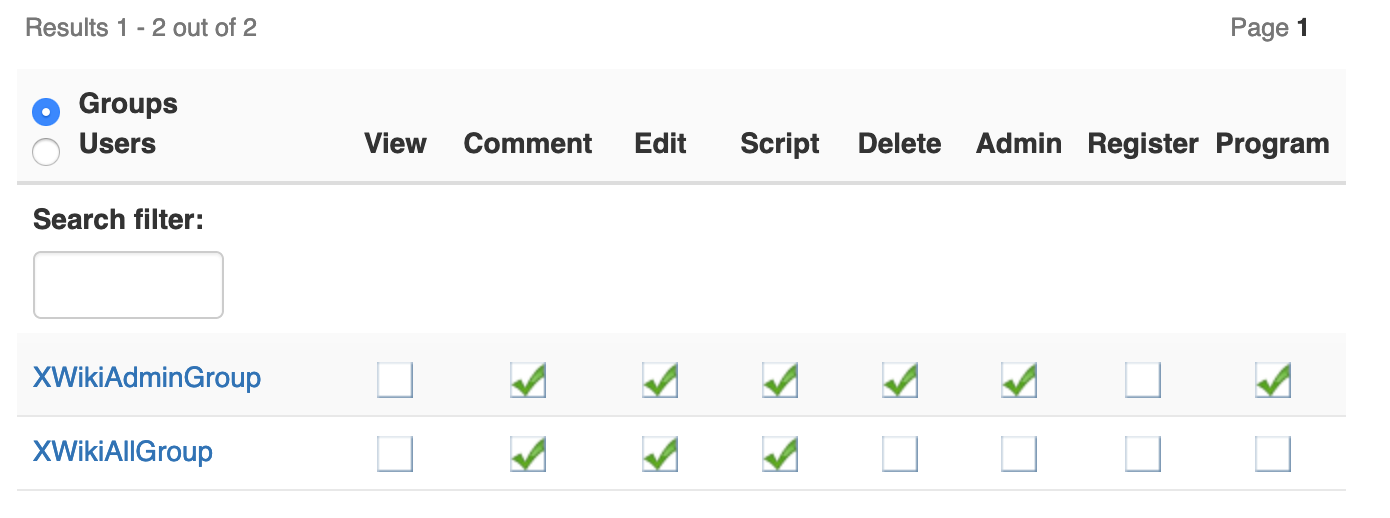

As of today, checking the global-rights checkbox "Prevent unregistered users from viewing pages, regardless of the page rights" prevents GoogleApps Login to work: The JS-Extensions scripts and OAuth pages cannot be delivered so that a login process can work.