crypto-algos💯
This repository consists of some of the Cryptography Algorithms and it is a part of Hacktoberfest.
So if you are having any Cryptography Algorithm, all you need is to create a PR and I will try to merge it all.
This is an amazing opportunity for beginners to exhibit their Cryptography skills and take part in one of the largest Open-Source event!
Contribution:
1. Fork this repository.
Click on the ![]() symbol at the top right corner.
symbol at the top right corner.
2. Clone the forked repository.
git clone https://github.com/<your-github-username>/crypto-algos3. Navigate to the project directory.
cd crypto-algos4. Add new Crypto Algo, update the README with a brief and concise info about the same
5. Stage your changes and commit
#Add changes to Index
git add .
#Commit to the local repo
git commit -m "<your_commit_message>"7. Push your local commits to the remote repo.
git push 8. Create a PR !
9. Congratulations! Sit and relax, you've made your contribution to crypto-algos project.
Issues:
For major changes, you are welcome to open an issue to discuss what you would like to change. Enhancements will be appreciated.
Note:
Do drop a ⭐if you like this initiative of mine.
Check out my Github profile here.
Algorithms
AES
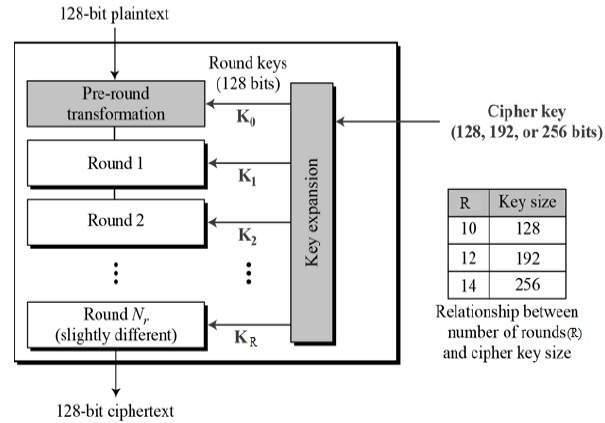
AES is an iterative rather than Feistel cipher. It is based on ‘substitution–permutation network’. It comprises of a series of linked operations, some of which involve replacing inputs by specific outputs (substitutions) and others involve shuffling bits around (permutations).
BlowFish

Blowfish is an encryption technique designed by Bruce Schneier in 1993 as an alternative to DES Encryption Technique. It is significantly faster than DES and provides a good encryption rate with no effective cryptanalysis technique found to date. It is one of the first, secure block cyphers not subject to any patents and hence freely available for anyone to use.
Columnar Transposition Cipher
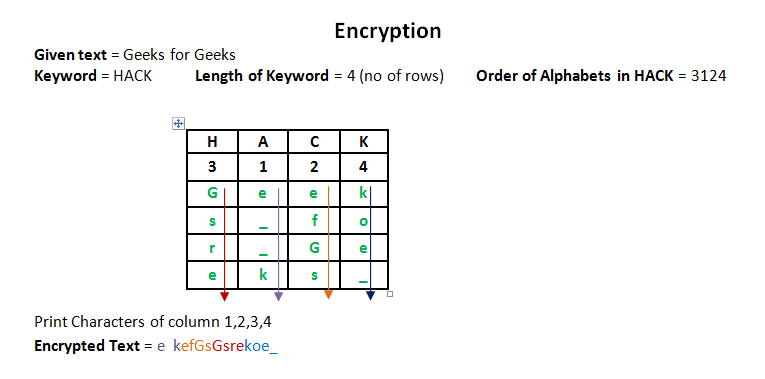
Given a plain-text message and a numeric key, cipher/de-cipher the given text using Columnar Transposition Cipher The Columnar Transposition Cipher is a form of transposition cipher just like Rail Fence Cipher. Columnar Transposition involves writing the plaintext out in rows, and then reading the ciphertext off in columns one by one.
RSA
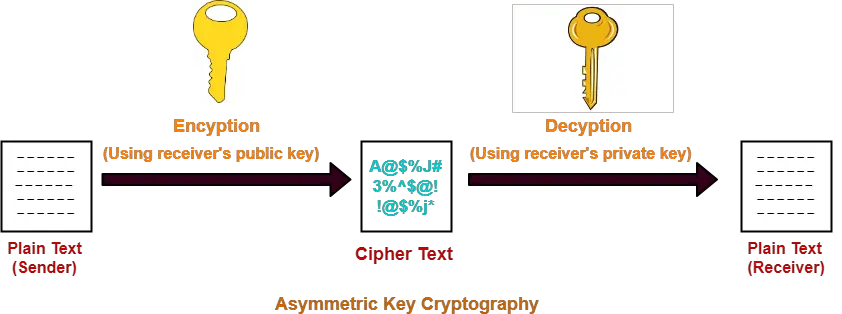
RSA algorithm is a public key encryption technique and is considered as the most secure way of encryption. It was invented by Rivest, Shamir and Adleman in year 1978 and hence name RSA algorithm. Algorithm
The RSA algorithm holds the following features −
RSA algorithm is a popular exponentiation in a finite field over integers including prime numbers.
The integers used by this method are sufficiently large making it difficult to solve.
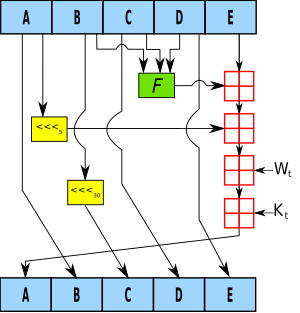
There are two sets of keys in this algorithm: private key and public key.SHA-1
SHA-1 or Secure Hash Algorithm 1 is a cryptographic hash function which takes an input and produces a 160-bit (20-byte) hash value. This hash value is known as a message digest. This message digest is usually then rendered as a hexadecimal number which is 40 digits long. It is a U.S. Federal Information Processing Standard and was designed by the United States National Security Agency.




