After some investigation I found that if I lock the secure flash memory region, using for example SCRLOCK = 0x11, I am able to debug non-secure code as expected. However, now debugging secure code is not possible because of the lock. The chip must be totally erased (e.g. using the windows ICP tool) to enable secure debugging again. Erasing the chip through GNU/Eclipse by checking the Erase chip box in the debug configurations does not work.
How can simultaneous debugging of secure and non-secure code be achieved, without the need of additional locks/erasures?


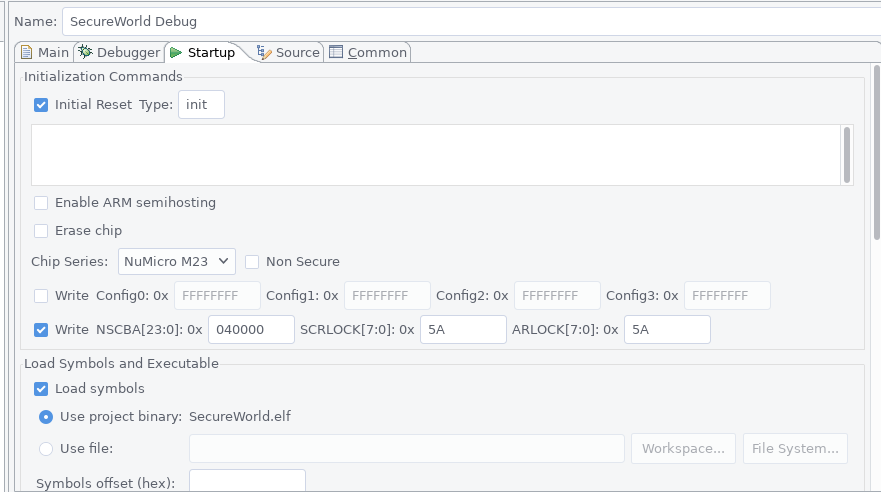

Hello there,
debugging non-secure code with GNU/Eclipse nad OpenOCD under Linux does not seem to work. Building the code is not an issue, but flashing it on the board fails (simply hangs) with the following error message:
On the other hand, building and debugging secure code works like a charm.
The code that was used for this demonstration is the TrustZone template code, which is generated by GNU/Eclipse automatically after creating a secure and non-secure project respectively. The configurations steps were followed as described in the official GNU/Eclipse user manual. The only difference is that from the secure zone I explicitly set
NCSBA = 0x040000andSCRLOCK = 0x5AandARLOCK = 0x5Abecause by defaultNCSBA = 0x080000would be written, which does not correspond to the default partitioning#define FMC_SECURE_ROM_SIZE 0x40000.Such a mismatch causes the device to hang in an infinite loop.