 OWASP VulnerableApp
OWASP VulnerableApp
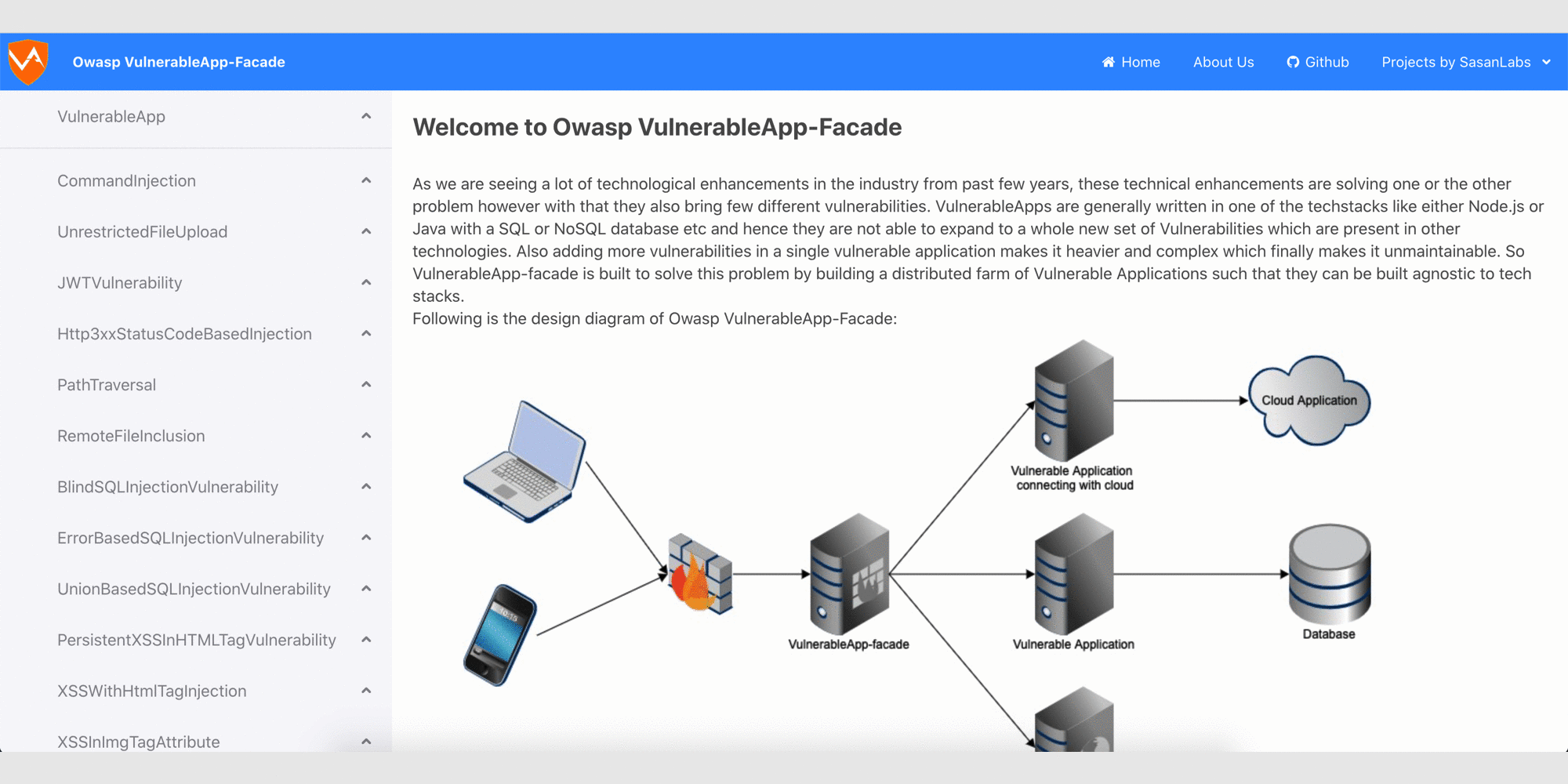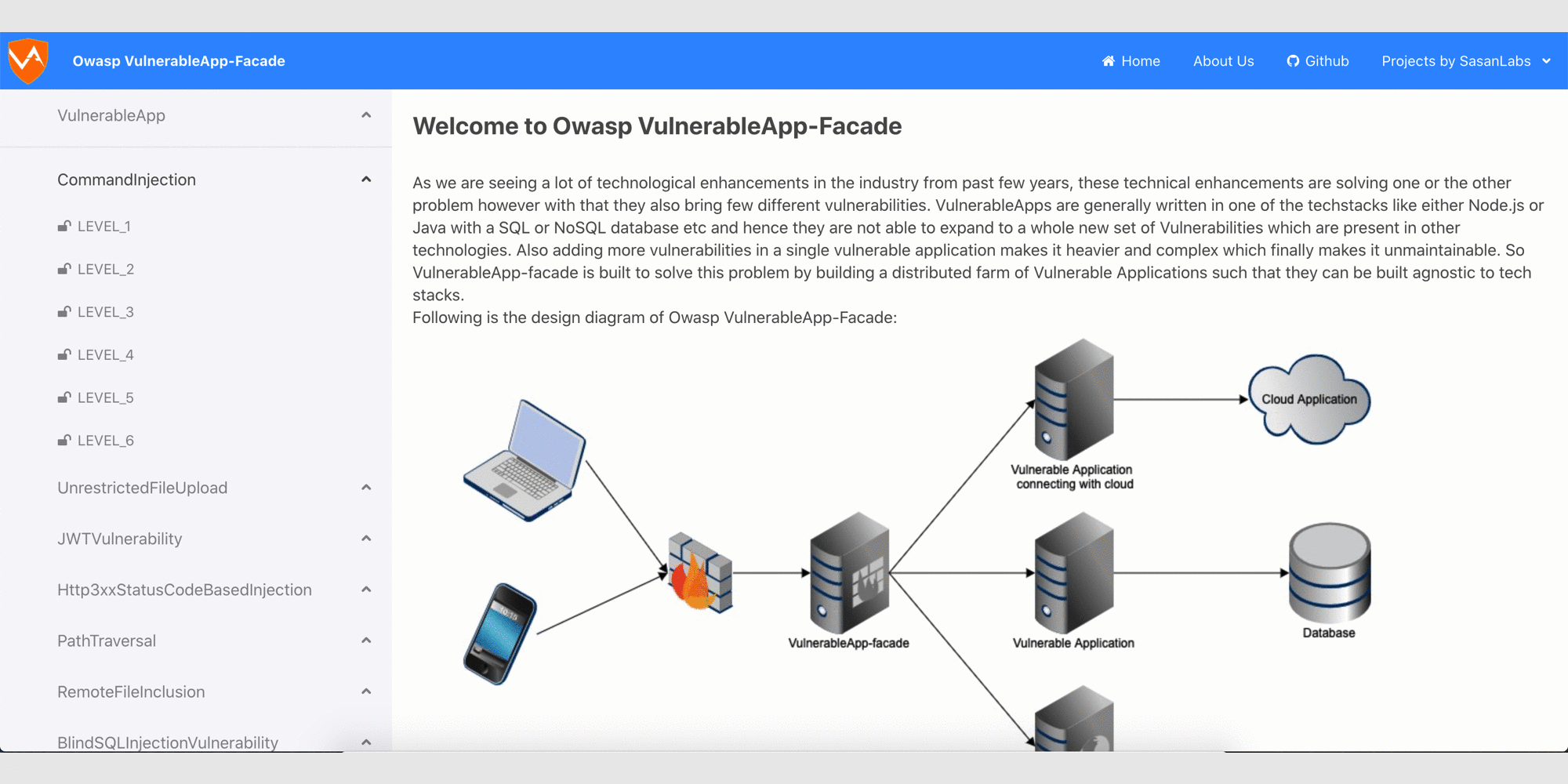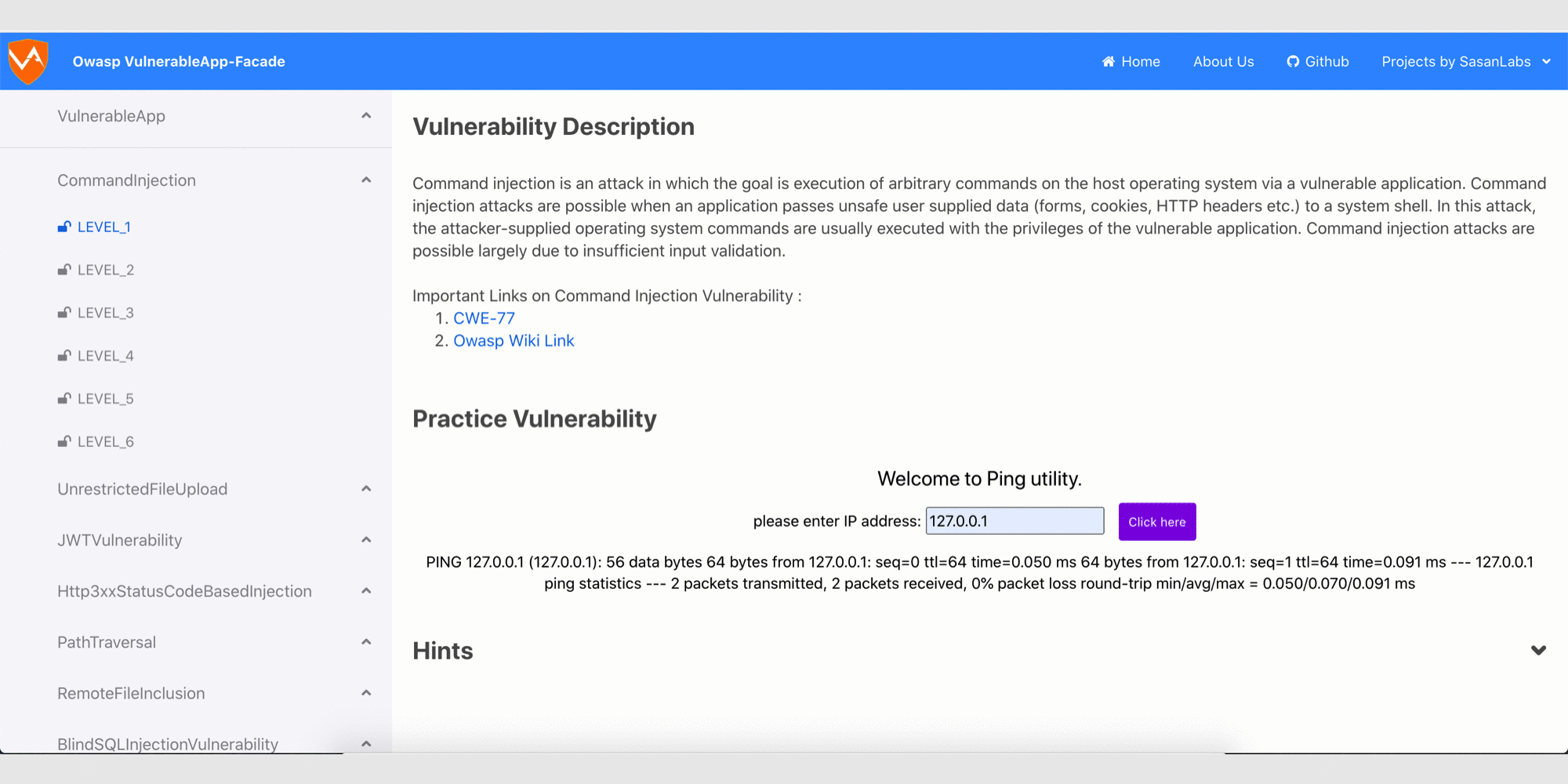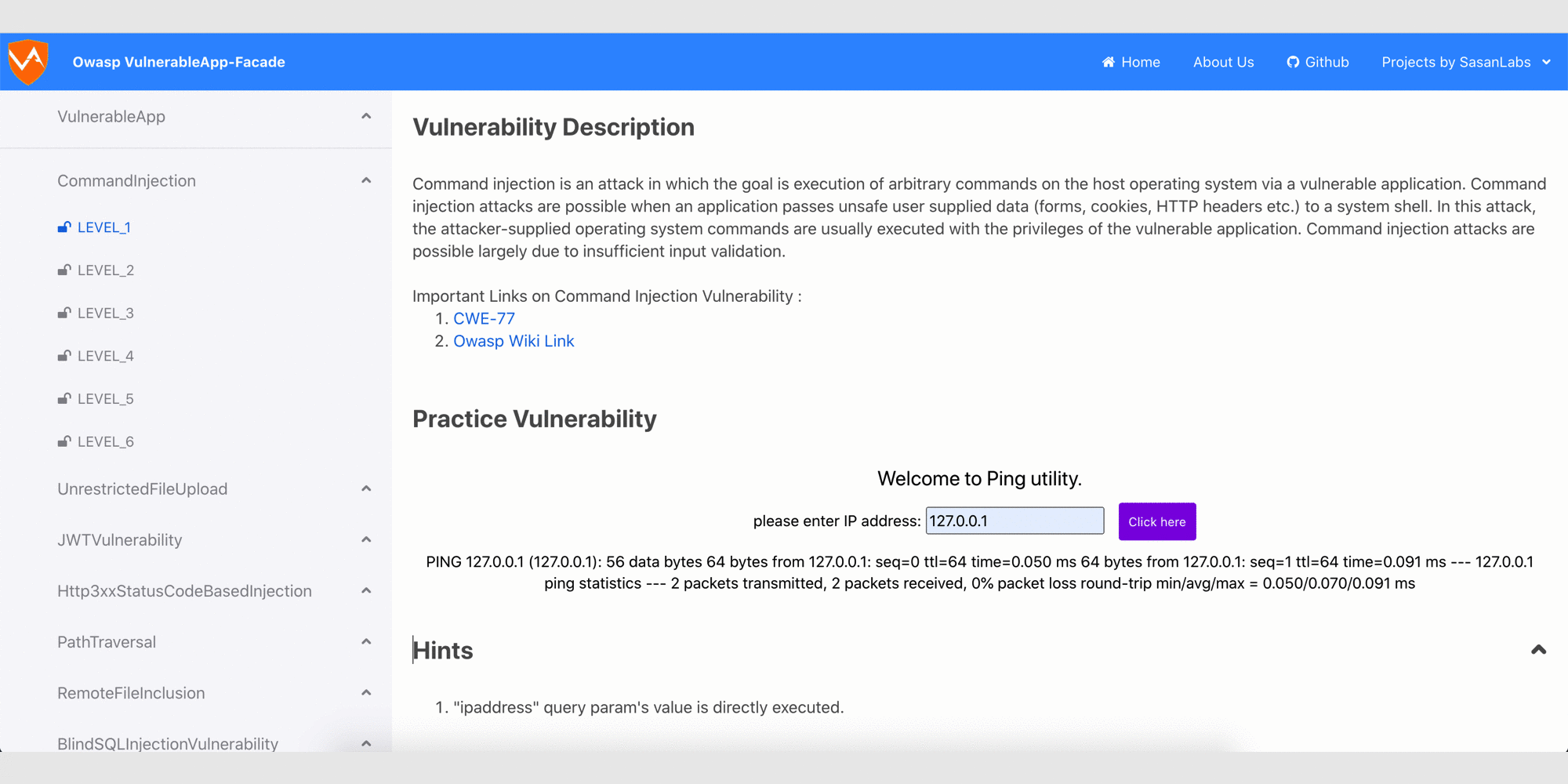
As Web Applications are becoming popular these days, there comes a dire need to secure them. Although there are several Vulnerability Scanning Tools, however while developing these tools, developers need to test them. Moreover, they also need to know how well the Vulnerability Scanning tool is performing. As of now, there are little or no such vulnerable applications existing for testing such tools. There are Deliberately Vulnerable Applications existing in the market but they are not written with such an intent and hence lag extensibility, e.g. adding new vulnerabilities is quite difficult. Hence, developers resort to writing their own vulnerable applications, which usually causes productivity loss and the pain of reworking.
VulnerableApp is built keeping these factors in mind. This project is scalable, extensible, easier to integrate and easier to learn. As solving the above issue requires addition of various vulnerabilities, hence it becomes a very good platform to learn various security vulnerabilities.
User Interface
Technologies used
- Java8
- Spring Boot
- ReactJS
- Javascript/TypeScript
Currently handled Vulnerability types
- JWT Vulnerability
- Command Injection
- File Upload Vulnerability
- Path Traversal Vulnerability
- SQL Injection
- XSS
- XXE
- Open Redirect
- SSRF
Contributing to Project
There are multiple ways in which you can contribute to the project:
- If you are a developer and trying to start on to the project, then the suggestion is to go through the list of issues which contains
good first issuewhich can be a good starter. - If you are a developer or a security professional looking to add new Vulnerability type then you can Generate the Sample Vulnerability by running
./gradlew GenerateSampleVulnerability. It will generate the Sample Vulnerability template which has placeholders and comments. Modified files can be seen in the logs of the command or in the github history. You can navigate to those files, fill in the placeholders and then build the project to see the effect of the changes. - In case you are looking to contribute to the project by publicising it or working on the growth of the project, please feel free to add your thoughts to discussions section or issues and we can discuss over them.
Running the project
There are 2 ways to run the project:
-
The simplest way to run the project is using Docker containers which will run the full-fleged VulnerableApplication with all the components. For running as Docker application, follow following steps:
- Download and Install Docker Compose
- Clone this Github repository
- Open the terminal and Navigate to the Project root directory
- Run the command
docker-compose pull && docker-compose up - Navigate to browser and visit
http://localhostand this will give the User Interface for VulnerableApp.
Note: The above steps will run the latest unreleased VulnerableApp version. If you want to run the latest released version, please use docker latest tag.
- Another way to run the VulnerableApp is as standalone Vulnerable Application is:
- Navigate to Releases Section in github and download the Jar for the latest released version
- Open the terminal and navigate to the project root directory
- Run the command
java -jar VulnerableApp-* - Navigate to browser and visit
http://localhost:9090/VulnerableApp. This will give the Legacy User Interface for the VulnerableApp.
Building the project
There are 2 ways in which this project can be built and used:
- As a Docker application which will help in running the full-fledged VulnerableApplication. For running as Docker application, follow following steps:
- Build the docker image by running
./gradlew jibDockerBuild - Download Docker-Compose and run in the same directory
docker-compose up - Navigate to browser and visit
http://localhostand this will give the User Interface for VulnerableApp.
- Build the docker image by running
- As a SpringBoot application which will run with the Legacy UI or Rest API but gives the benefit of debugging and solving issues. This is the simple way,
- Import the project into your favorite IDE and run it
- Navigate to browser and visit:
http://localhost:9090/VulnerableAppand this will give the Legacy User Interface for VulnerableApp which you can use to debug and test.
Connecting to embedded H2 database
For accessing database from browser, visit: http://localhost:9090/VulnerableApp/h2
Database Connection properties:
JDBC Url: jdbc:h2:mem:testdb
User Name: admin
Password: hackerContact
In case you are stuck with any of the steps or understanding anything related to project and its goals, feel free to shoot a mail at karan.sasan@owasp.org or raise an issue and we will try our best to help you.
Documentation and References
- Documentation
- Design Documentation
- Owasp VulnerableApp
- Overview video for OWASP Spotlight series
- Overview Video
Blogs
- Overview of Owasp-VulnerableApp - Medium article
- Overview of Owasp-VulnerableApp - Blogspot post
- Introduction to Owasp VulnerableApp by Kenji Nakajima



