OpenRedireX
A fuzzer for detecting open redirect vulnerabilities
🏗️ Install
⛏️ Usage
📚 Dependencies
Install
git clone https://github.com/devanshbatham/openredirex
cd openredirex
sudo chmod +x setup.sh
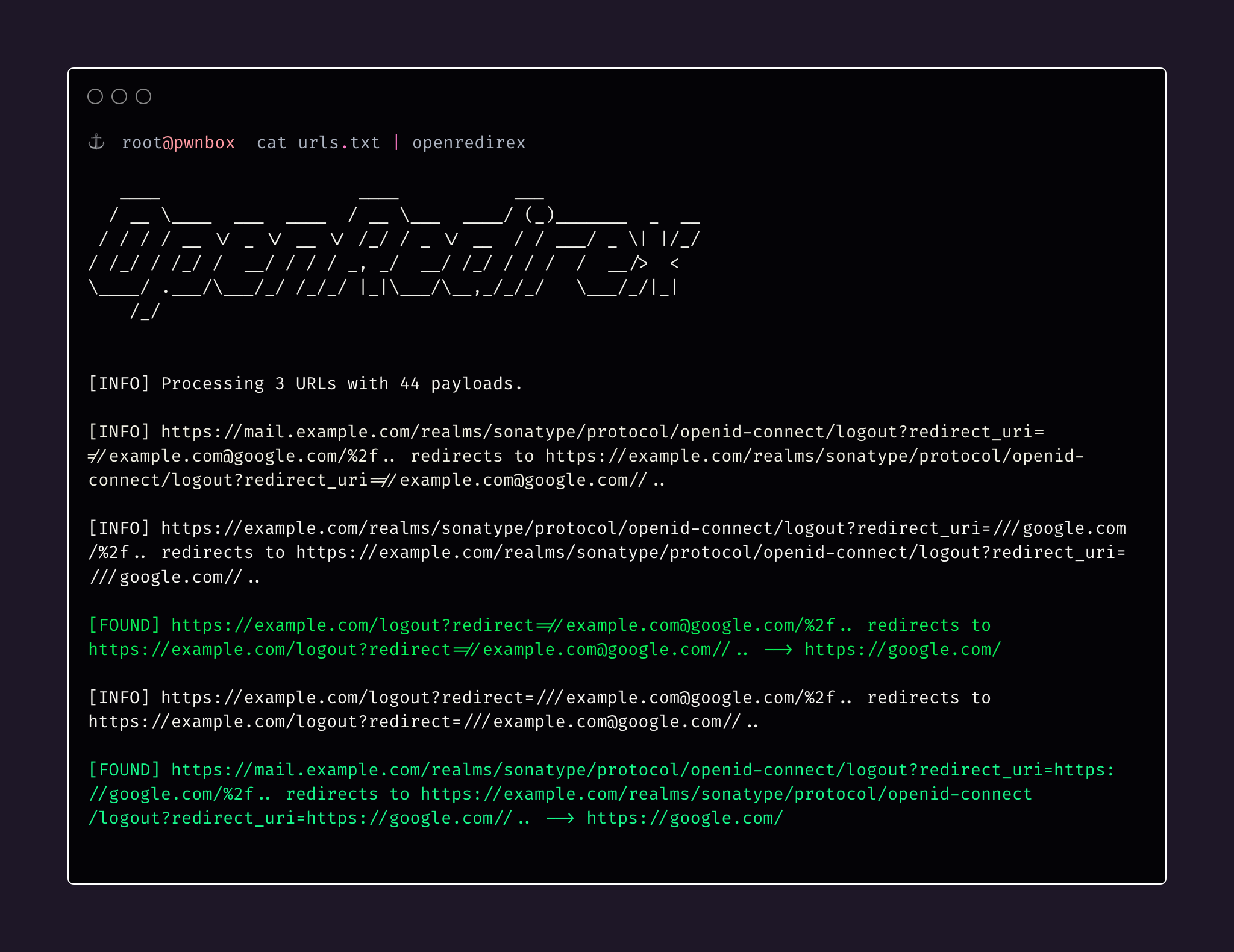
./setup.shUsage
The script is executed from the command line and has the following usage options:
openredirex [-p payloads] [-k keyword] [-c concurrency]-p,--payloads: File containing a list of payloads. If not specified, a hardcoded list is used.-k,--keyword: Keyword in URLs to replace with payload. Default is "FUZZ".-c,--concurrency: Number of concurrent tasks. Default is 100.
The script expects a list of URLs as input. Each URL should contain the keyword specified by the -k option. The script replaces the keyword with each of the payloads, and attempts to fetch the modified URL.
Example usage:
cat list_of_urls.txt | openredirex -p payloads.txt -k "FUZZ" -c 50List of URLs should look like below:
cat list_of_urls.txt
https://newsroom.example.com/logout?redirect=FUZZ
https://auth.example.com/auth/realms/sonatype/protocol/openid-connect/logout?redirect_uri=test
https://exmaple.com/php?test=baz&foo=barThis example reads URLs from the file list_of_urls.txt, replaces all the values of the parameters to FUZZ (if --keyword is not supplied), then again replaces the keyword FUZZ or the supplied keyword with each payload from payloads.txt, and fetches each URL concurrently, with a maximum of 50 concurrent tasks.
Dependencies
The script uses the following libraries:
argparsefor handling command-line arguments.aiohttpfor making HTTP requests.tqdmfor displaying progress.concurrent.futuresfor handling concurrent tasks.asynciofor managing asynchronous tasks.
You need to install these dependencies before running the script. Most of them are part of the standard Python library. You can install aiohttp and tqdm using pip:
pip install aiohttp tqdmYou can use this script to check for open redirects in web applications. However, you should only use it on systems that you have been given explicit permission to test.