origin
The nice thing about cyber warfare is that unlike climate change... cyber can be funny.

Tumblr user "lagonegirl" was at the head of a Russian psyop. This is the sort of thing they were posting. What agenda could this possibly advance?
(The honest answer might be "well, they made bogstandard tumblr posts to build a following for doing Russian psyop stuff, like pretending to be a BLM activist who believes the world needs a race war". That's the less funny side of what lagonegirl was up to. Even still... thanks, Russia, for making the worst social media site just a slightly bit worse.)






 ^Social media is catered toward one's preferences, especially political ones, thus polarizing communities on the Internet.
^Social media is catered toward one's preferences, especially political ones, thus polarizing communities on the Internet.

 Recent cyberattacks by sector. 2021 Nonprofit Cybersecurity Incident Report. March 2021. Retrieved from
Recent cyberattacks by sector. 2021 Nonprofit Cybersecurity Incident Report. March 2021. Retrieved from 



 (a black to white hat transformation playing on the names given to malicious hackers (black hats) and their more positive peers (white hats) and mirroring the ethical shifts that some in the hacking community are beginning to undergo)
(a black to white hat transformation playing on the names given to malicious hackers (black hats) and their more positive peers (white hats) and mirroring the ethical shifts that some in the hacking community are beginning to undergo)

























 -- Ray Bradbury, I assume
(The original image is a still from the 1966 film adaptation of "Fahrenheit 451", with text added by me)
-- Ray Bradbury, I assume
(The original image is a still from the 1966 film adaptation of "Fahrenheit 451", with text added by me)






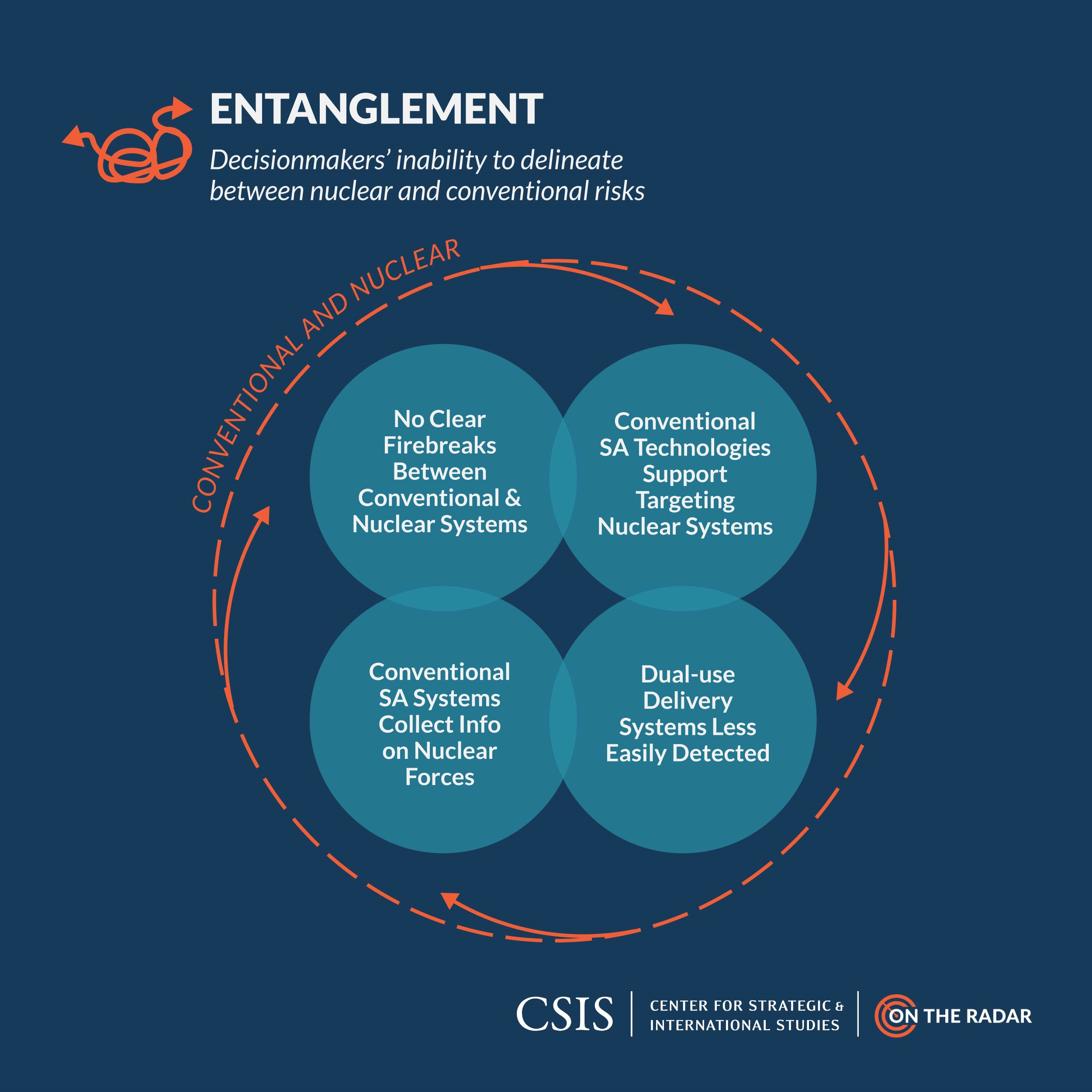
Leave below as comments your memos that grapple with the topic of cyber inspired by the readings, movies & novels (at least one per quarter), your research, experiences, and imagination! Also add a thumbs up to the 5 memos you find most awesome, challenging, and discussion-worthy!
Recall the following instructions: Memos: Every week students will post one memo in response to the readings and associated topic. The memo should be 300–500 words + 1 visual element (e.g., figure, image, hand-drawn picture, art, etc. that complements or is suggestive of your argument). The memo should be tagged with one or more of the following:
origin: How did we get here? Reflection on the historical, technological, political and other origins of this existential crisis that help us better understand and place it in context.
risk: Qualitative and quantitative analysis of the risk associated with this challenge. This risk analysis could be locally in a particular place and time, or globally over a much longer period, in isolation or in relation to other existential challenges (e.g., the environmental devastation that follows nuclear fallout).
policy: What individual and collective actions or policies could be (or have been) undertaken to avert the existential risk associated with this challenge? These could include a brief examination and evaluation of a historical context and policy (e.g., quarantining and plague), a comparison of existing policy options (e.g., cost-benefit analysis, ethical contrast), or design of a novel policy solution.
solutions: Suggestions of what (else) might be done. These could be personal, technical, social, artistic, or anything that might reduce existential risk.
framing: What are competing framings of this existential challenge? Are there any novel framings that could allow us to think about the challenge differently; that would make it more salient? How do different ethical, religious, political and other positions frame this challenge and its consequences (e.g., “End of the Times”).
salience: Why is it hard to think and talk about or ultimately mobilize around this existential challenge? Are there agencies in society with an interest in downplaying the risks associated with this challenge? Are there ideologies that are inconsistent with this risk that make it hard to recognize or feel responsible for?
nuclear/#climate/#bio/#cyber/#emerging: Partial list of topics of focus.
Movie/novel memo: Each week there will be a selection of films and novels. For one session over the course of the quarter, at their discretion, students will post a memo that reflects on a film or fictional rendering of an existential challenge. This should be tagged with:
movie / #novel: How did the film/novel represent the existential challenge? What did this highlight; what did it ignore? How realistic was the risk? How salient (or insignificant) did it make the challenge for you? For others (e.g., from reviews, box office/retail receipts, or contemporary commentary)?