
Metlo CSP Report Listener
Easily build your CSP
---
[](http://makeapullrequest.com)
[](https://discord.gg/4xhumff9BX)

[](/LICENSE)
---
Building a good CSP is hard to do when you have tons of unknown scripts across your web apps.
The easiest way to incrementally build your CSP using the `report-uri` directive and listen for anything that breaks in report only mode.
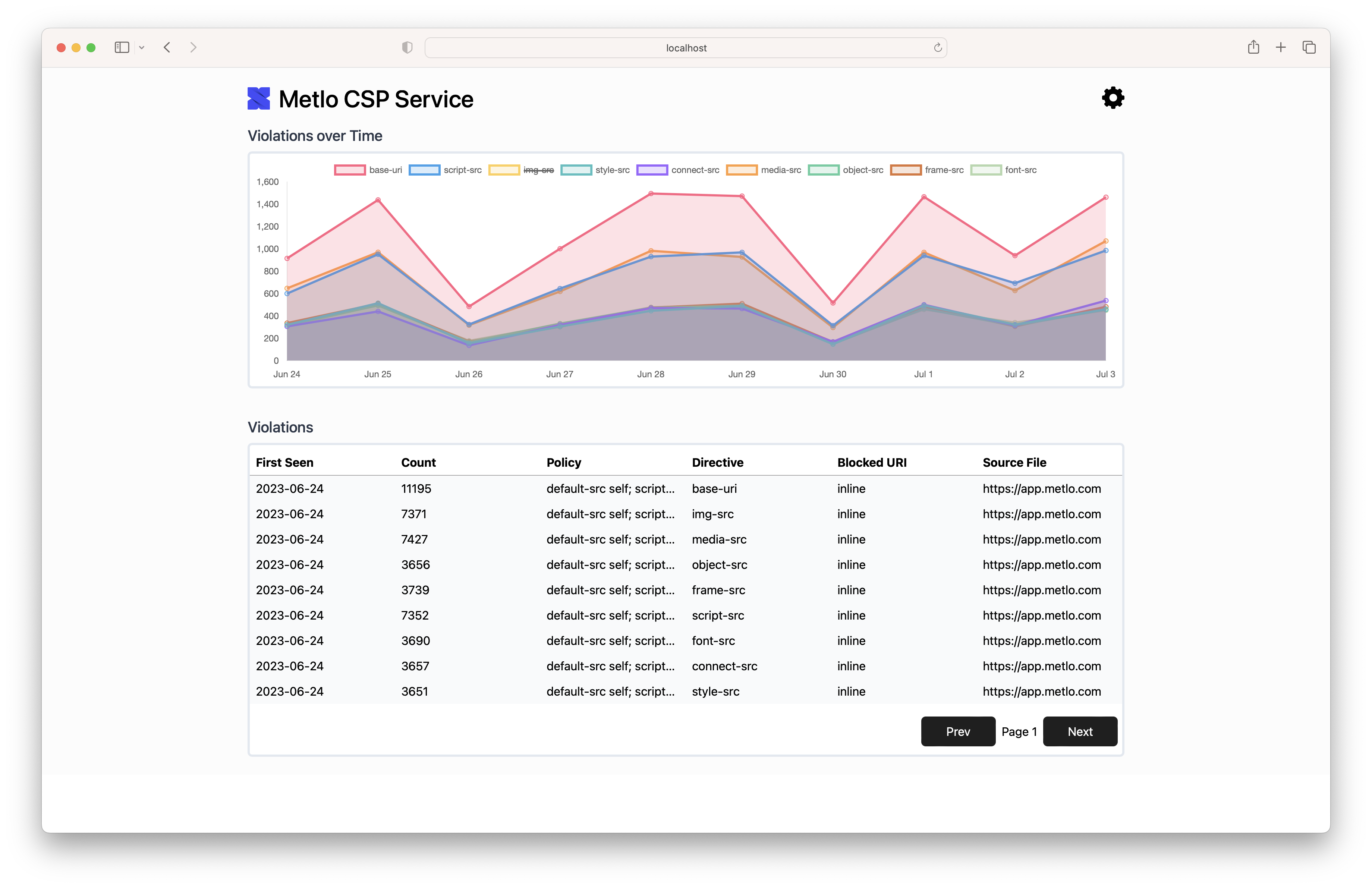
Our CSP Reporter makes this easy by storing all CSP report logs and displaying distinct reports you can add to your policy.
Checkout [Metlo API Security](https://www.metlo.com/) for more complete API protection!
## Setup
### 1. Install the Service
You can either use Docker or our Binary to install. You can configure the CSP Report listener with the following env vars:
1. **`METLO_SECRET_KEY` [required]** - A secret key to view CSP Reports. **Be sure to set this to something secure!**
2. **`METLO_DATA_PATH` [default `/tmp/metlo_csp/`]** - Where to store CSP Report data. By default we store it in a tmp folder so change this if you want your data to be persisted.
3. **`METLO_PORT` [default 8080]** - The port the service will listen on
4. **`METLO_LOG_LEVEL` [default info]** - Set the logging level to debug
**Docker Setup**
```bash
$ docker run -p 8080:8080 --env METLO_SECRET_KEY=