fofa2Xray
A tool that can combine fofa and xray for automatic batch multithreading scanning.
Can also scan the IP/domain name list by using Xray.
Coding by golang, both for windows, linux and macOS.
Documentation
Introduction
Use fofa api to get target domain list, then make webscan by xray.
Demo

File Mode Quick start
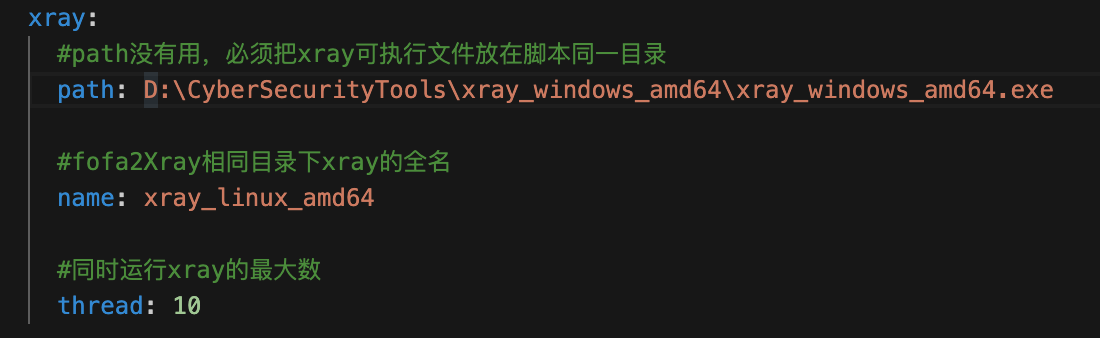
1. Configure the xray executable file address and the number of threads in f2Xconfig.yaml
2. Using "-t file" specify as file list scan mode(default is fofa mode), -f specify IP list file
./fofa2Xray -t file -f ipList.txt3. Perhaps it's a little strange, but for better scalability
Fofa Mode Quick start
-
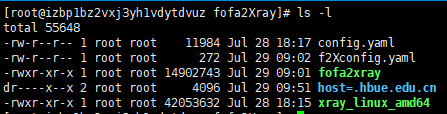
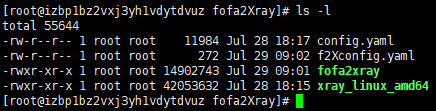
Move xray to the directory where fofa2xray is located
-
Vi f2Xconfig.yaml
fofa: email: {fofa账户} key: {fofaKey} # 固定查询语句 fixedQuerySyntexList: - status_code=200 - country="CN" # 查询语法 # 更多查询语法见https://fofa.info/ querySyntax: host # 使用querySyntax查询语法分别查询target targetList: - .hubu.edu.cn # - .hbue.edu.cn # - .wust.edu.cn xray: #path没有用,必须把xray可执行文件放在脚本同一目录 path: D:\CyberSecurityTools\xray_windows_amd64\xray_windows_amd64.exe #fofa2Xray相同目录下xray的全名 name: xray_windows_amd64.exe #同时运行xray的最大数 thread: 10 -
Run fofa2Xray.
./fofa2Xray nohup ./fofa2Xray & // 持久化 -
Check Result.
Fofa2Xray will create result folder for every target.